Configuring Google Single Sign-On Integration with SAML
Google offers a Single sign-on service as part of their Cloud Identity product, a unified identity platform for IAM (Identity and Access Management) and EMM (Enterprise Mobility Management). Google Single Sign-On (SSO) provides single-click access to thousands of on-premises and in the cloud pre-integrated applications.
- Using Security Assertion Markup Language (SAML), a user can use their managed account credentials to sign in to enterprise cloud applications via SSO. An Identity Provider (IdP) service provides administrators with a single place to manage all users and cloud applications.
- You don’t have to manage individual user IDs and passwords tied to individual cloud applications for each of your users. An IdP service provides your users with a unified sign-on across all their enterprise cloud applications.
- You can also create a new user in Invicti Enterprise with the Enable Auto Provisioning option.
If you encounter any problem while setting up SSO integration, see Troubleshooting SSO Issues.
You have to use IdP-initiated SSO if you want to utilize Auto Provisioning.
If you will use SP-initiated SSO, please set the Name ID Format value to email address on the IdP side.
Single Sign-On Fields
This table lists and explains the Single Sign-On fields in the Configure Single Sign-On window.
| Field | Description |
| Enable | Select this option to enable the single sign-on feature. |
| Enforce to authenticate only with single sign-on | Enable this option so only administrator users can authenticate without single sign-on. Users can only sign in to Invicti Enterprise by using the email address that belongs to their employer. |
| IdP Identifier | This is the SAML identity provider’s Identifier value. |
| SAML 2.0 Service URL | This is the Consumer URL value (also called the SSO Endpoint or Recipient URL). |
| SAML 2.0 Endpoint | This is the URL from your IdP’s SSO Endpoint field. |
| X.509 Certificate | This is the X.509 certificate value. |
How to configure Google Single Sign-On Integration with SAML
- Log in to your Google account and navigate to the Admin console.
- Select Apps > Web and mobile apps.
- From the Web and mobile apps page, select Add app drop-down, then Add custom SAML app.
- On the Add custom SAML app page, enter a friendly name for your app. (For this illustration, we use Invicti.)
- Select Continue.
- Take note of the IdP Information: SSO URL, Entity ID, and certificate. (You will need them in a later step.)
- In IDP metadata, select Download Metadata.
- Select Continue.
- In the ACS URL field, copy and paste the contents of the SAML 2.0 Service URL field from Invicti Enterprise’s Single Sign-On page.
- In the Entity ID field, copy and paste the contents of the Identifier field (URL) from Invicti SSO configuration page.
- Select Continue.
- Configure the Attribute Mapping based on your needs.
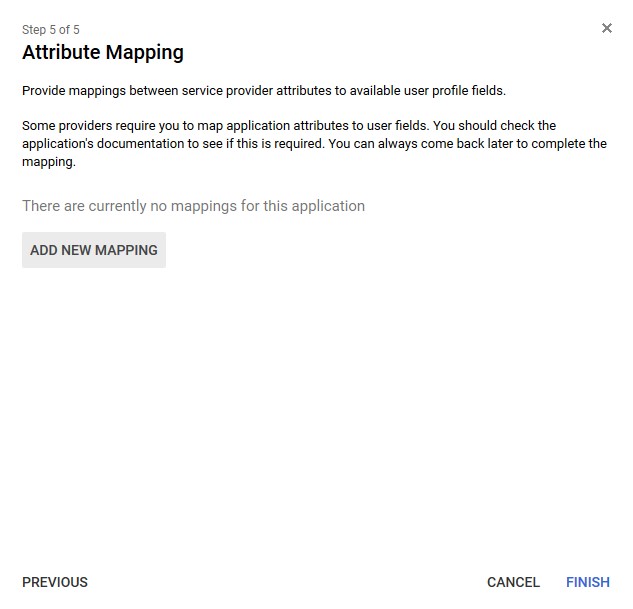
- Select Finish.
- Return to the SAML Settings page.
- Select the ellipsis (
) for More Options, then select ON for everyone.
- In the IdP Information note panel:
- Copy the URL from the Entity ID field.
- Then log in to Invicti Enterprise, and from the main menu, select Settings > Single Sign-On.
- Select Google from the drop-down list, and paste the URL into the Idp Identifier field.
- Next, copy the URL from the SSO URL field.
- Then in Invicti Enterprise’s Single Sign-On window, paste the URL into the SAML 2.0 Endpoint field.
- Finally, copy the content from the downloaded X.509 Certificate field.
- Then in Invicti Enterprise’s Single Sign-On window, paste it into the X.509 Certificate field.
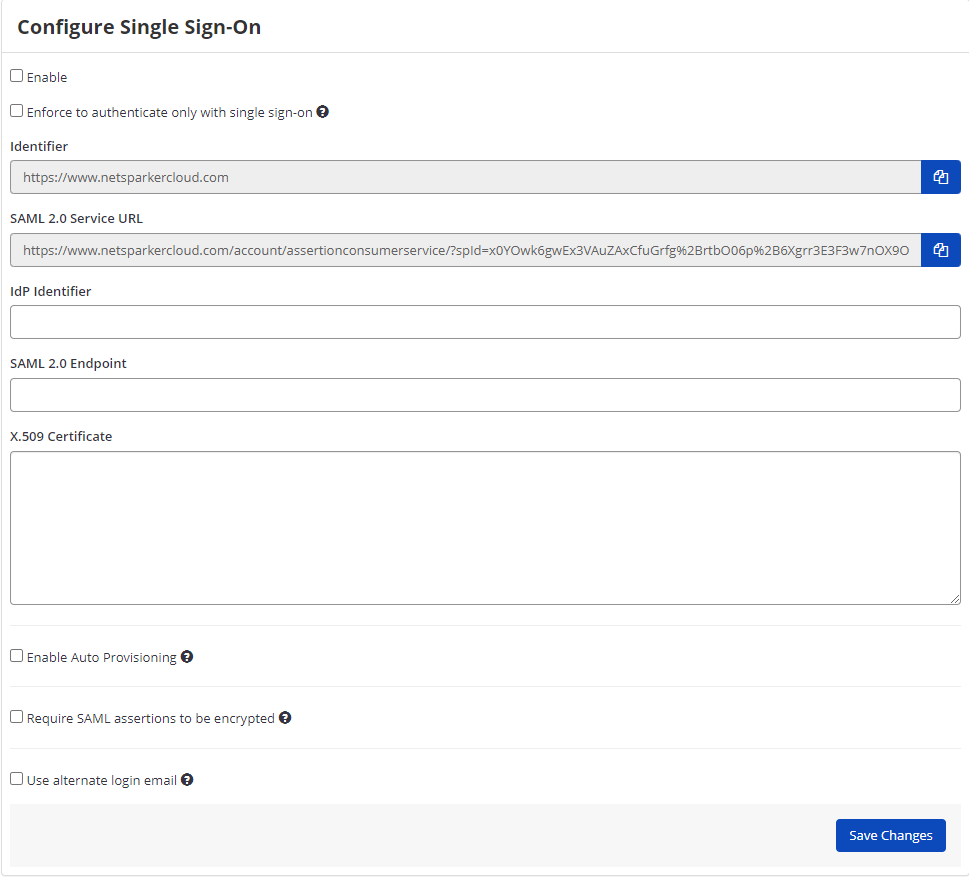
- Select one or all of the following options, if necessary:
- Enable Auto Provisioning: If enabled, an account will be automatically created for IdP-registered users when they first access Invicti Enterprise. To do so, you must complete the FirstName, LastName, and Phone Number (optional) fields in the Attribute Statements on the IdP side. For further information about OnlySsoLogin, see Provisioning a member.
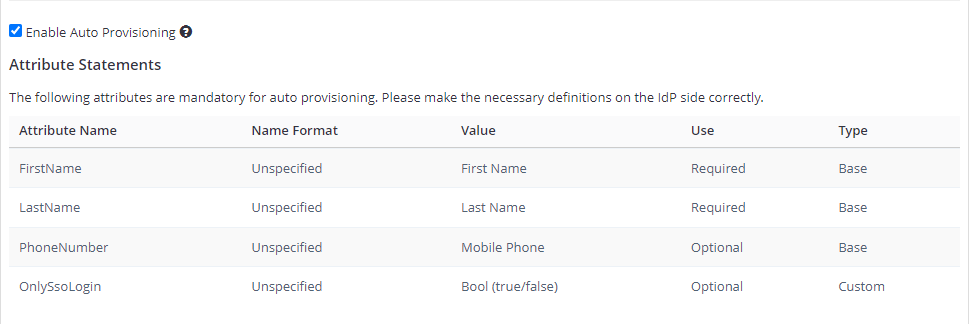
- Require SAML assertions to be encrypted: If enabled, it prevents third parties from reading private data in transit from assertions. There are two options:
- Generate a new certificate for me: Invicti generates a key pair. Invicti will keep a private key to decrypt received SAML messages and provide you with a certificate so that you can upload it on the IdP side.
- I have an existing certificate: You need to upload your certificate to Invicti by importing a decryption certificate from your files.
- Use Alternate Login Email: If enabled, this lets users use alternative email for SSO. So, you can enter an alternative email on the New Member Invitation page and while editing the user’s details in the Team window.
- On Invicti Enterprise’s Single Sign-On page, click Save Changes.
For further information, see the Google document.