Encryption Settings
Invicti Enterprise On-Premises encrypts and decrypts sensitive data by using AES encryption. For encryption, Invicti uses a secret key.
Starting from the Invicti Enterprise On-Premises 2.2, this secret key is randomly generated during a new installation. During the installation, Invicti Enterprise requires you to download and store your secret key, as you cannot access this key again in Invicti Enterprise On-Premises. You can only regenerate the secret key.
- Deleting or resetting the application settings
- Installing a fresh copy of Invicti Enterprise On-Premises while using the previous configuration
- Changing the IIS AppPool user running Invicti Enterprise
- An access problem to the application settings by Invicti Enterprise.
Please note that if you want to have a clean installation with the new database and settings, you do not need to provide your secret key.
If you lose your secret key, the following data is corrupted, and you must configure these settings again:
- Account level Single Sign-On (SSO) settings
- All Integrations configuration settings
- Scan Policy proxy password
- All scan Authentication related passwords
- User two-factor authentication configurations
Invicti Enterprise generates a unique secret key during the installation. If you want to regenerate your secret key, you can do this in the Encryption settings.
Since all data containing sensitive data in the database will be re-encrypted with a new secret key, it is strongly recommended that you do not have any active scans during the re-encryption. Please pause or cancel any active scans if you have.
Using older versions than the On-Premises 2.2? While updating to the On-Premises 2.2 or newer versions, the application does not ask you to enter a secret key. You can continue using the application.
However, it is strongly recommended that you generate a new secret key. For further information, see Generating a new secret key in Invicti Enterprise.
This topic explains how to regenerate a new secret key in Invicti Enterprise On-Premises.
Encryption Settings Field
This table lists and explains the Encryption Settings fields on the Encryption Settings page.
| Button/Section/Field | Description |
| Last Revision | This is the last date that you take action, such as generating a key or downloading it. |
| Configuration | This displays who generated the secret key. The options are the following: User-Customized: This is a secret key generated during the Invicti Enterprise On-Premises installation. System Generated: This is a built-in secret key Invicti Enterprise provided. |
| Generate New Secret Key | This lets you generate a new secret key. |
Generating a new secret key in Invicti Enterprise
How to generate a new secret key in Invicti Enterprise
- Log in to Invicti Enterprise.
- From the main menu, select Settings > Encryption.
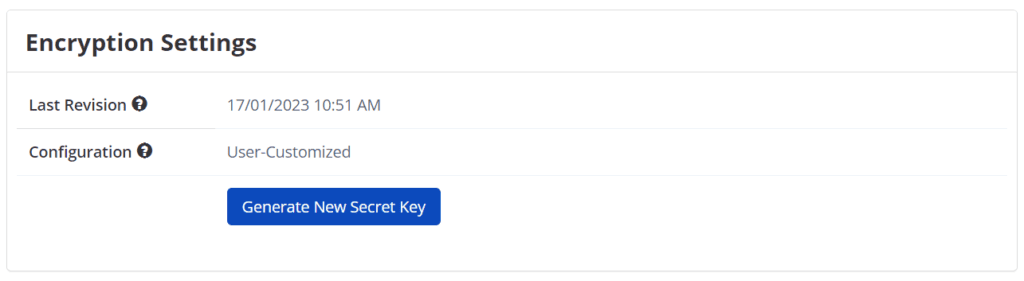
- Select Generate New Secret Key.
- From the Generate New Secret Key dialog, enter i agree to the text field. (Please note that this is case-sensitive.)
Before selecting the Re-encrypt button, make sure you downloaded the new secret key.
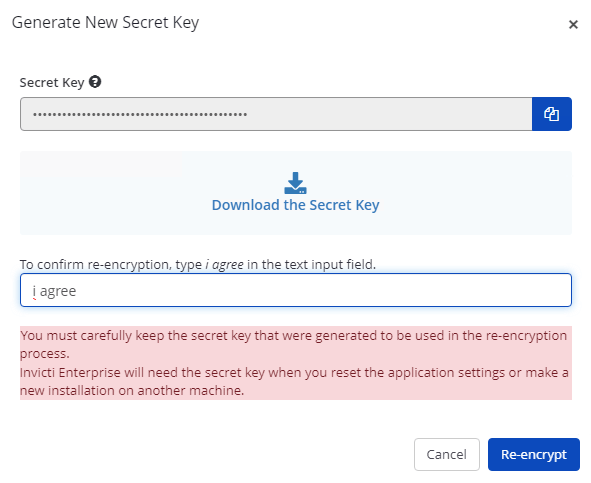
- Select Re-encrypt.
Configuring Invicti Enterprise Web Application Server to a new machine
This instruction explains how to configure Invicti Enterprise Web Application Server with and without using the secret key into a new machine.
How to configure Invicti Enterprise Web Application Server using the secret key
- The first step of the Installation Wizard is configuring the Database connection.
- Complete the fields to enable Invicti to build the necessary database structure and populate it with data. Select Next.
- From the Encryption window, enter your secret key.
- Complete the remainder of the fields, as described in the Configuring Invicti Enterprise Web Application Server Using the Installation Wizard.
- Select Finish to complete the configuration.
How to configure Invicti Enterprise Web Application Server without using the secret key
If you do not enter your secret key, the following data is corrupted, and you must configure these settings again: Account level Single Sign-On (SSO) settings, All Integrations configuration settings, Scan Policy proxy password, All scan Authentication related passwords, User two-factor authentication configurations
- The first step of the Installation Wizard is configuring the Database connection.
- Complete the fields, to enable Invicti to build the necessary database structure and populate it with data. Select Next.
- From the Encryption window, select the Lost the secret key? link.
- From the Reset the Secret Key window, select Reset.
You cannot undo this process. If you select Reset, Invicti Enterprise generates a new secret key and encrypts your data with this new secret key.
- Complete the remainder of the fields, as described in the Configuring Invicti Enterprise Web Application Server Using the Installation Wizard.
- Select Finish to complete the configuration.
FAQ
Question: What if Invicti Enterprise On-Premises cannot access your configuration file that includes your secret key?
- In this case, after logging in to Invicti Enterprise On-Premises, it displays the Encryption step in the installation process and requires you to enter the secret key. You can enter your secret key to continue using the application.