WEB APPLICATION SECURITY TESTING FOR TECHNOLOGY & SOFTWARE
Secure your web applications with the only AppSec platform that truly scales
It doesn’t matter how many web apps, sites, and APIs you have. You can secure them all with Invicti.
- Automate everything that can possibly be automated
- Integrate AppSec testing into your existing tools and workflows
- Spend less on manual pentests and bug bounties

“The software is an important part of my security strategy which is in progress toward other services at OECD. And I find it better than external expertise. I had, of course, the opportunity to compare expertise reports with Invicti ones. Invicti was better, finding more breaches.”
Andy Gambles Senior Analyst, OECD
Trusted by technology companies around the world



Automate everything
Save your teams thousands of hours each year by automating all the AppSec work that can possibly be automated.
- Minimize false positives with the only solution that automatically verifies 94% of direct-impact vulnerabilities
- Automatically create, assign, and update tickets in your issue tracker
- Automatically retest fixes so developers can remediate without the back-and-forth
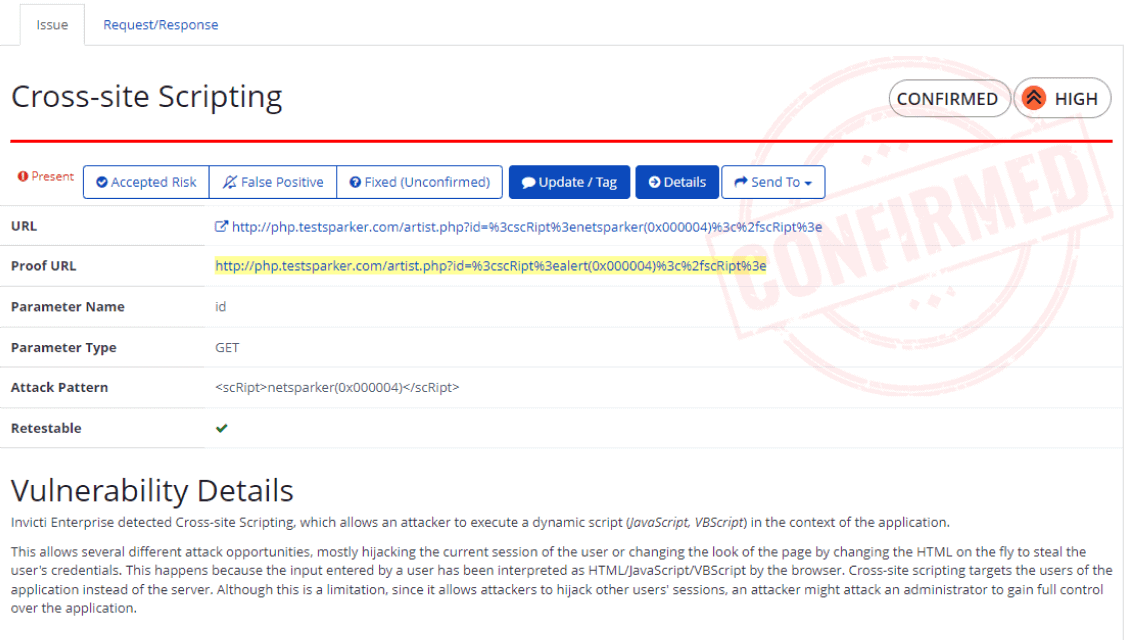
“Consistently finds and validates SQL injection vulnerabilities faster than any scanner we have ever used.”
– Jim Broome, President, DirectDefense
Integrate anything
No other AppSec platform has more integrations than Invicti. Let developers take action on security with the tools they already use with 50+ integrations into:
- CI/CDs
- Issue trackers
- Project management tools
- Single sign-on (SSO) providers
- Web application firewalls (WAF)
- And more
Or connect to anything with a full-feature REST API.
“It is easy to use and set up, generating easy-to-read findings and reports that we can integrate into our workflows, our collaboration suite, and – most importantly – our reporting tools.”
– Henk-Jan Angerman, Founder, SECWATCH
Detect more vulnerabilities. Spend less on bug bounties.
Get broader, deeper coverage with blended DAST + IAST and SCA. So you can detect more vulnerabilities with less reliance on manual pentesting and costly bounty programs.
GARTNER REVIEWS
Superior service
GET A DEMO
See why there’s no better way to scale your application security
Discover the features teams like yours love:
- Flexible deployment options: Cloud, on-prem, or hybrid
- Built-in reporting library with customizable templates
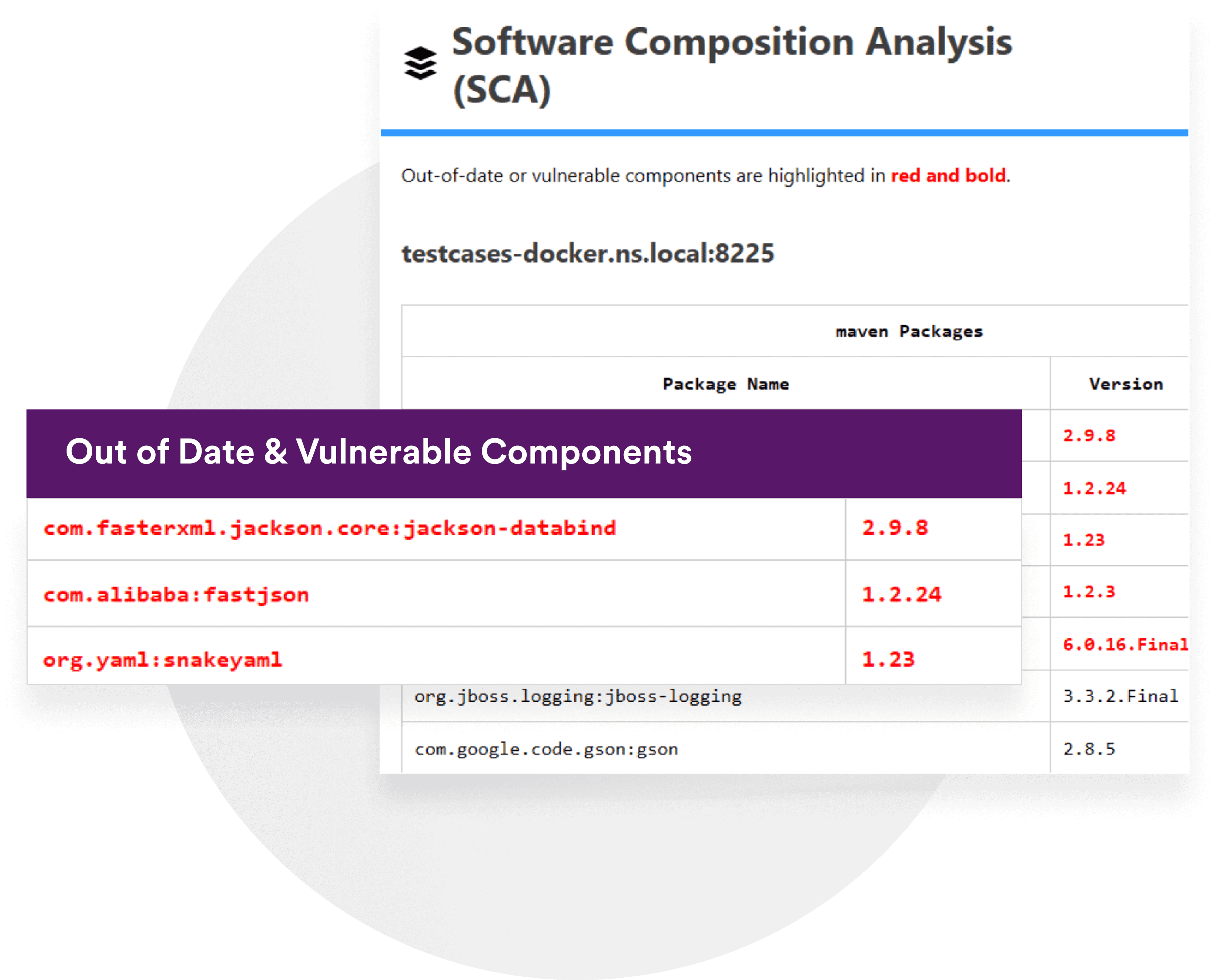
- SCA: Find your vulnerable components
- Blended DAST + IAST: Detect vulnerabilities others miss
- 50+ direct integrations into your CI/CD, ticketing, and other tools
- Full-feature REST API: Connect to anything
- Unlimited users: Add more at any time for free

