Measure and improve any KPI with trustworthy data
Make informed security decisions with comprehensive metrics, dashboards and reports that give you full visibility into the state of your security programs.
3600+ Top Organizations Trust Invicti
























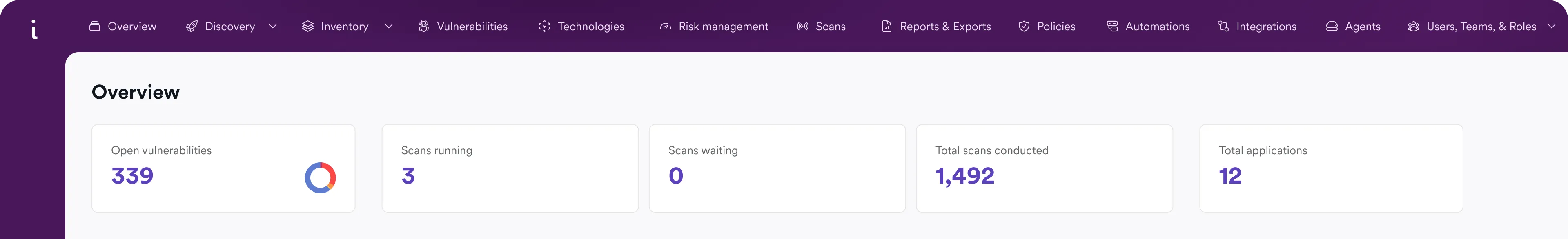
Better measurement, better risk management
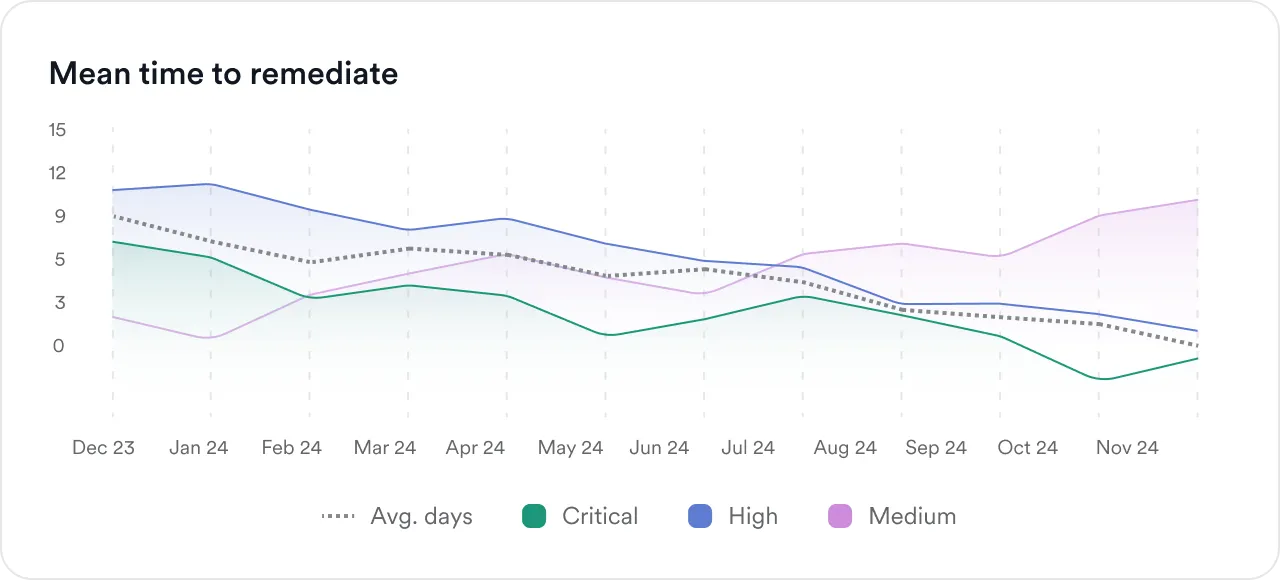
Optimize triage and remediation
Track remediation and triage efficiency by measuring how long it takes developers to resolve issues and security engineers to triage vulnerabilities. Identify bottlenecks, set improvement goals, and use automation to accelerate both processes over time.
Measure security at every business level
Define organizational hierarchies to track and aggregate vulnerability data across projects, products, business units, or the entire company. Use custom labels to categorize projects and filter reports and dashboards for deeper insights.
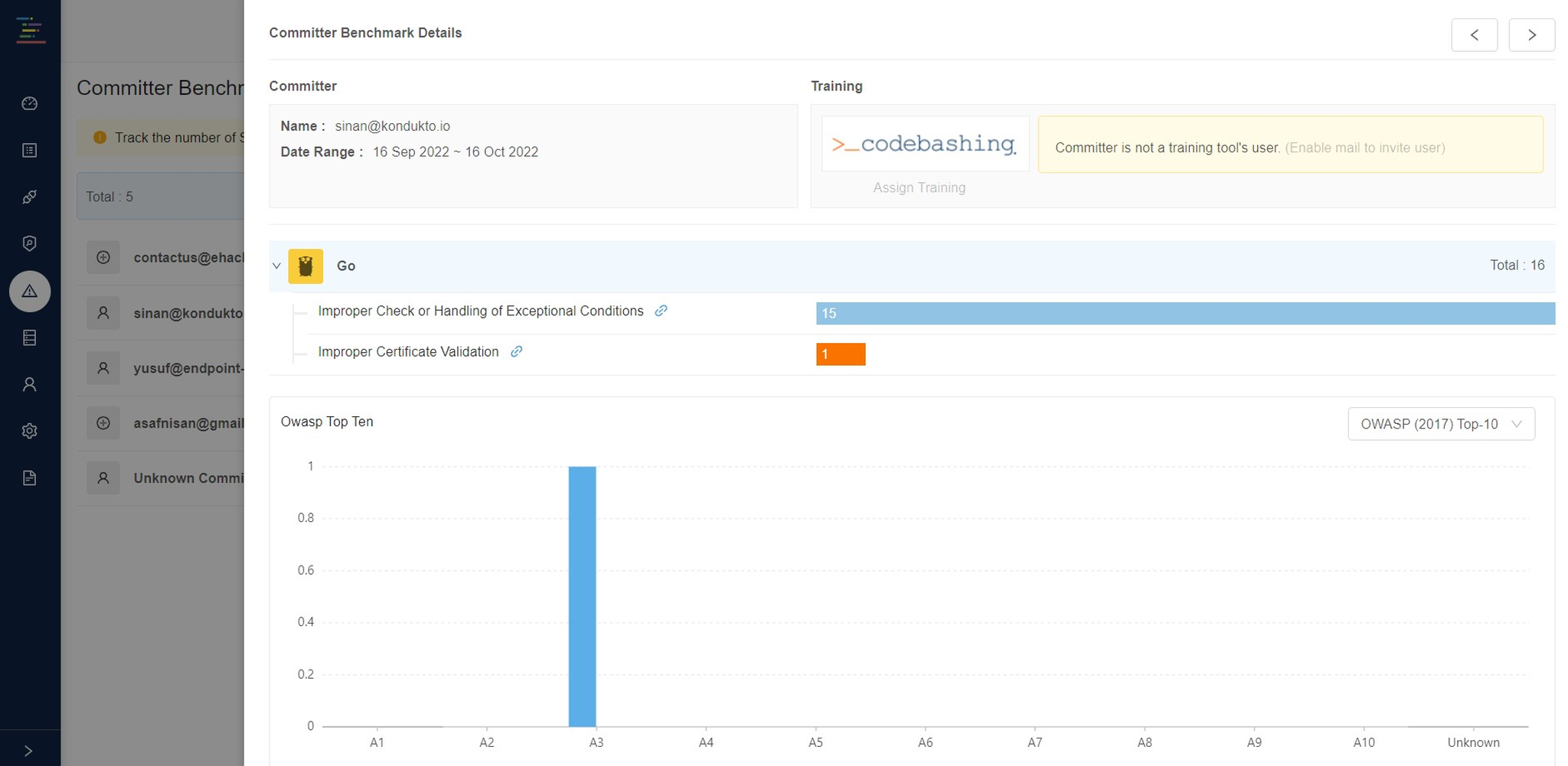
Improve secure coding with data
Improve developers’ secure coding skills by analyzing the vulnerabilities they introduce, identifying needed training, and integrating with platforms like Secure Code Warrior and SecureFlag to deliver personalized learning programs.
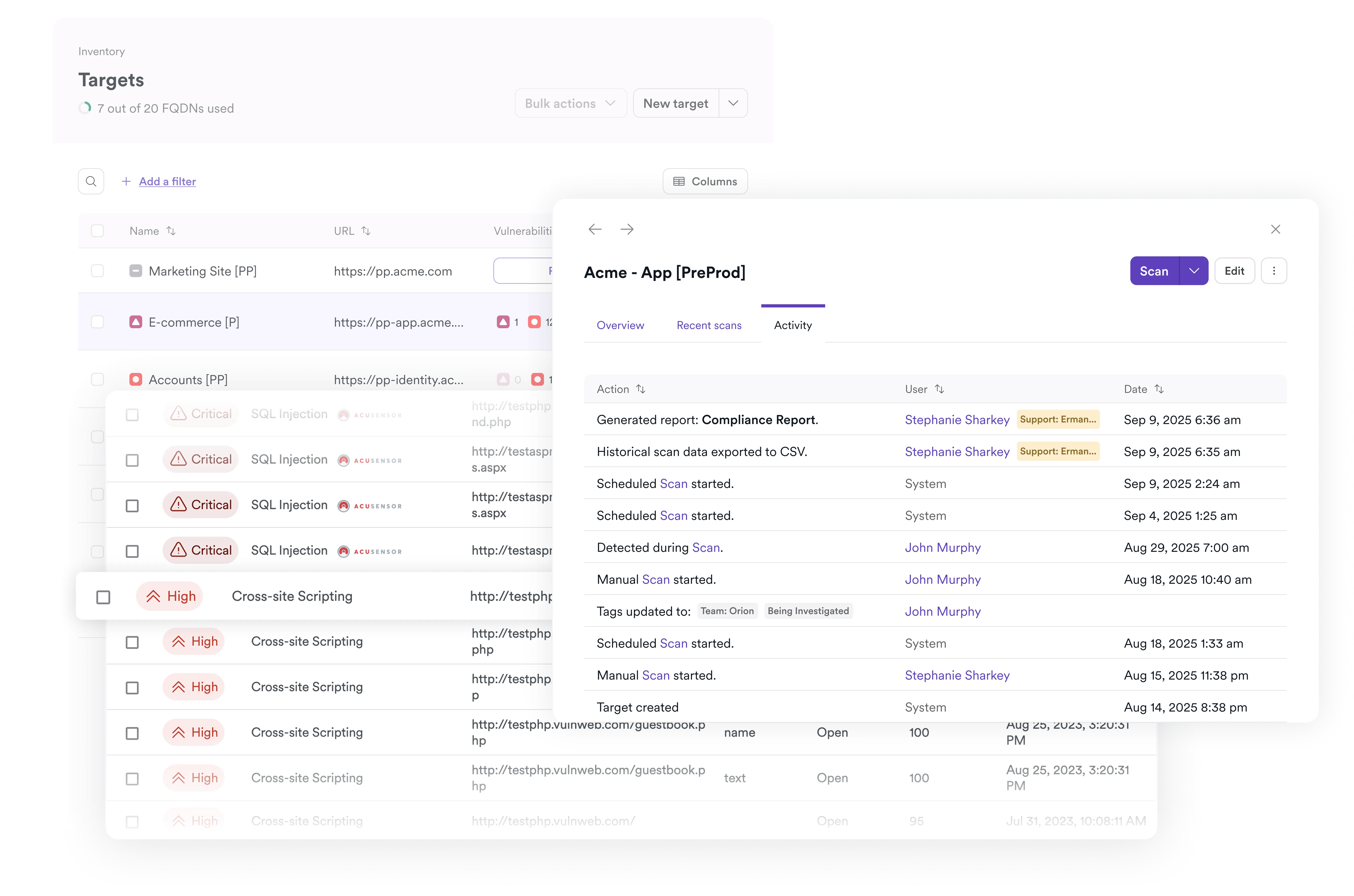
Improve triage efficiency
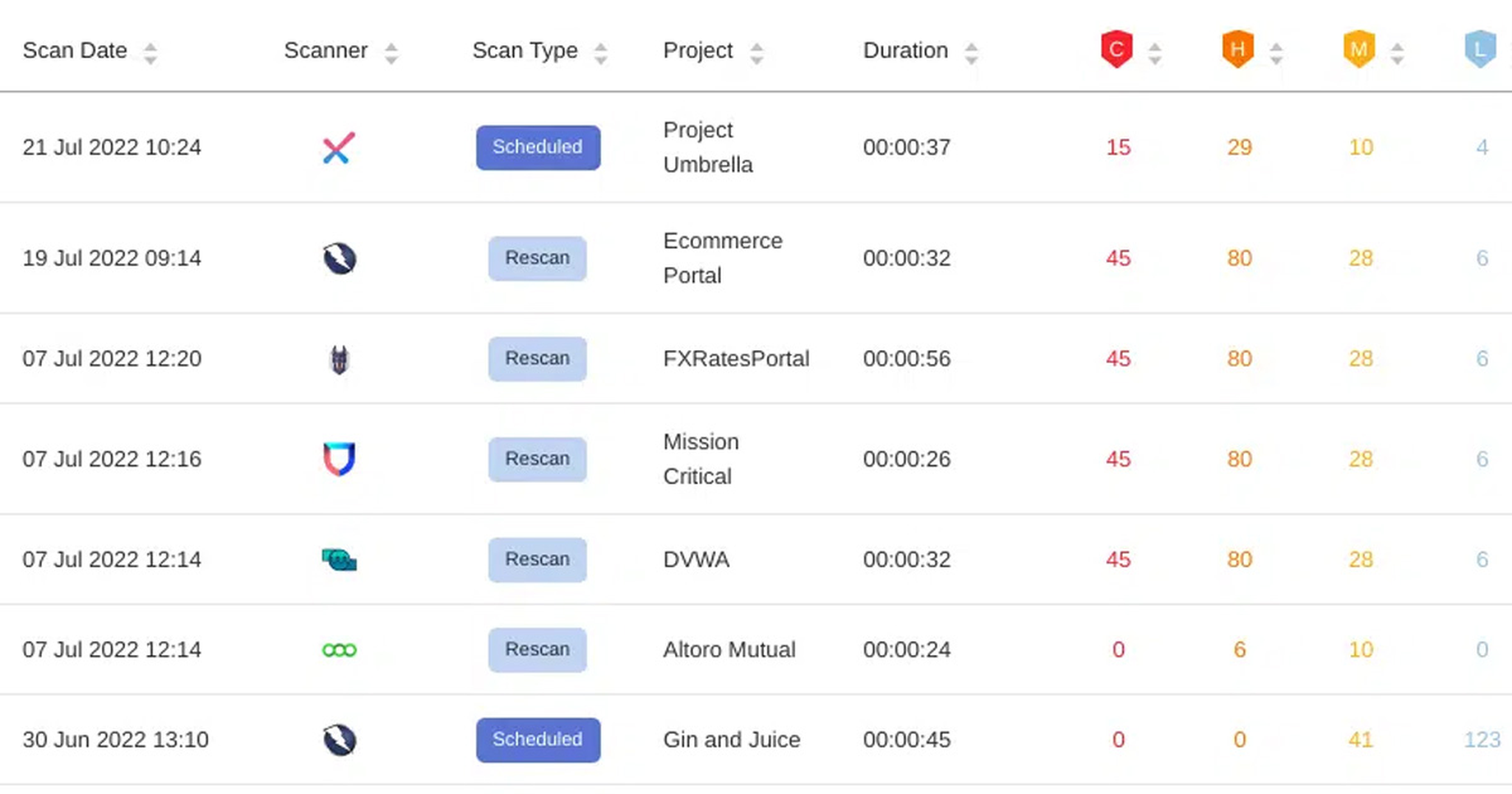
Optimize remediation

Eliminate workflow friction
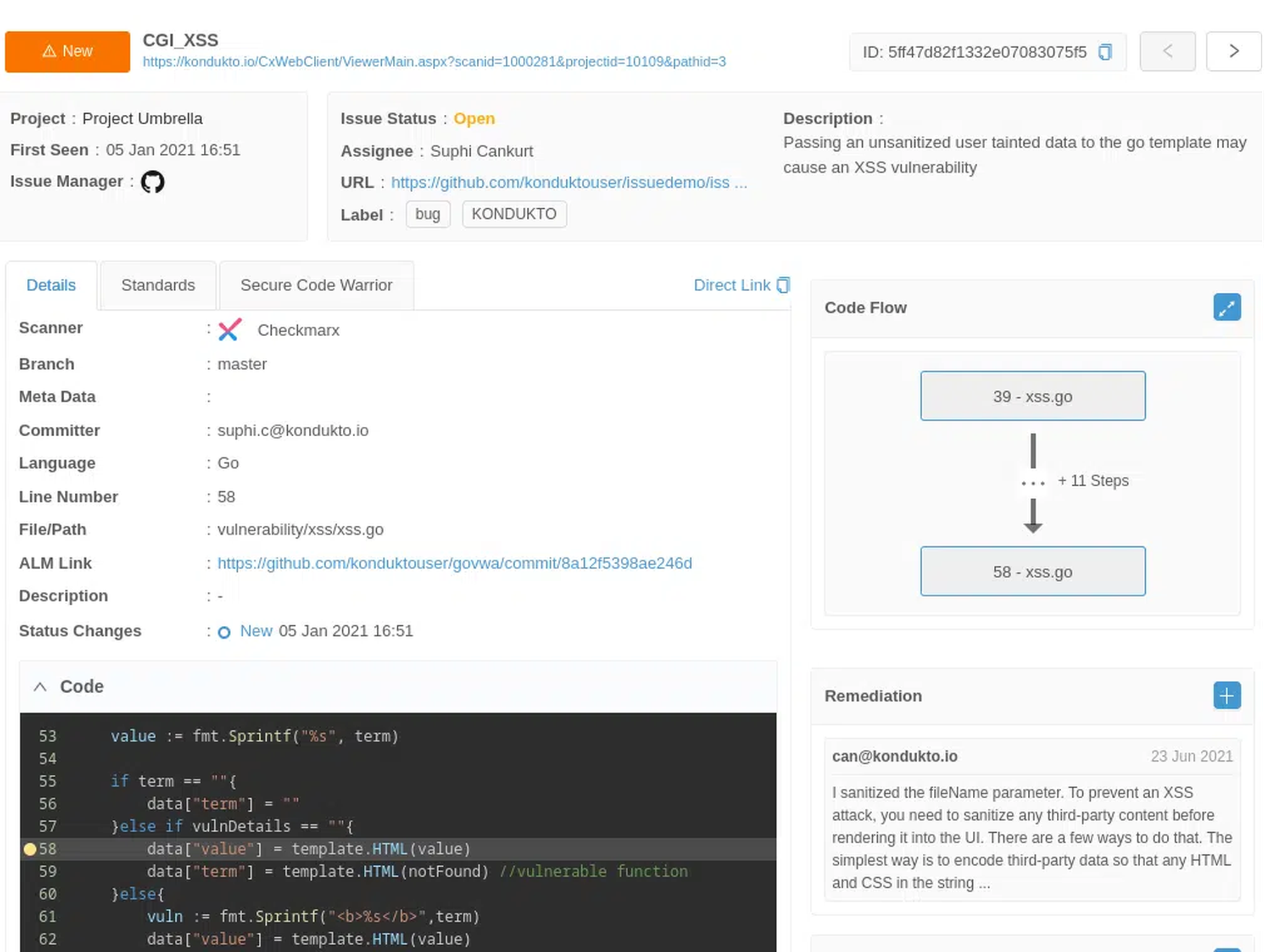
Secure dev practices
Unite stakeholders
Integrated with the tools you already use
Measure and improve AppSec metrics with proof