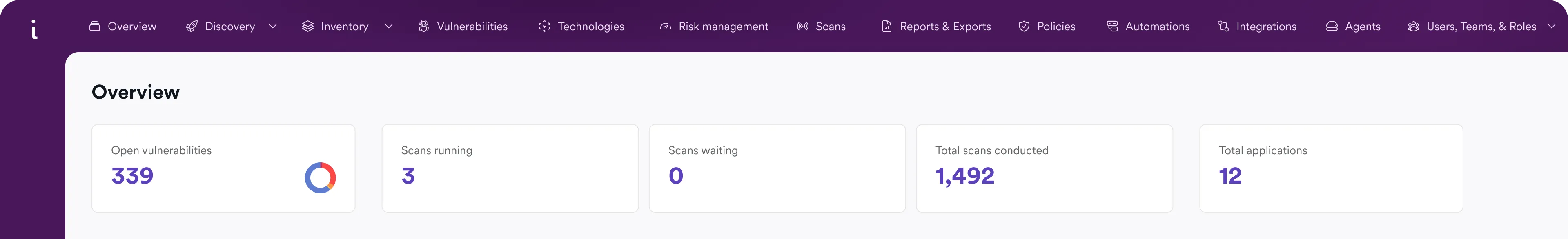
Manage all vulnerabilities in one intelligent platform
Invicti unifies all security testing tools and manual processes under one platform. AppSec leaders see test results in a single view, developers get automated remediation workflows, and organizations track risk with clear KPIs.
Thank you!
We received your message and contact details.
AppSec challenges we solve with Invicti ASPM
Testing noise and fragmentation
Scanners floods teams with duplicate CVEs and siloed results. Without deduplication and normalization across AST tools, teams can’t see real risk.
Manual triage and remediation
Security teams waste hours manually assigning issues and chasing duplicates across disconnected pipelines. Weak automation, validation, and integration = slow remediation.
KPIs and benchmarking
Most tools stop at reporting, leaving leaders in the dark on their actual security posture. Without remediation guidance and integrated training, vulnerabilities keep coming back.
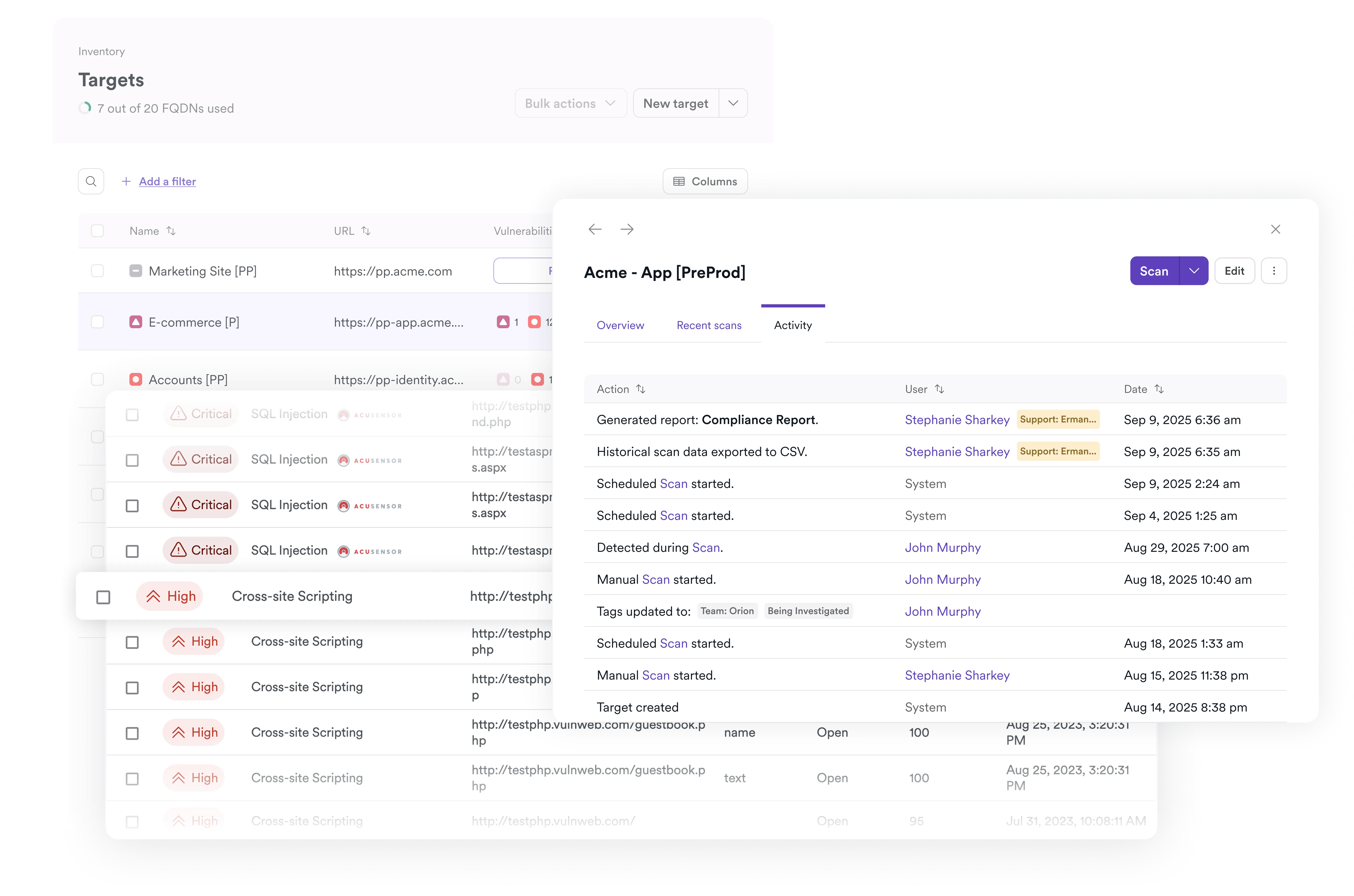
Aggregate and consolidate vulnerabilities
Automatically fetches vulnerabilities from all connected security tools, removing the need for engineers to manually consolidate thousands of findings.
Deduplicates overlapping vulnerabilities that point to the same issue in the source code, reducing noise and the total number of items to triage.
Manual imports (e.g., pen test findings) become first-class items in the same workflows and dashboards.
Cross-branch consolidation so one action propagates through your Git flow (avoid duplicate work on the “same” vuln).
SBOM locator to aggregate component usage and instantly see all apps affected by a vulnerable dependency.
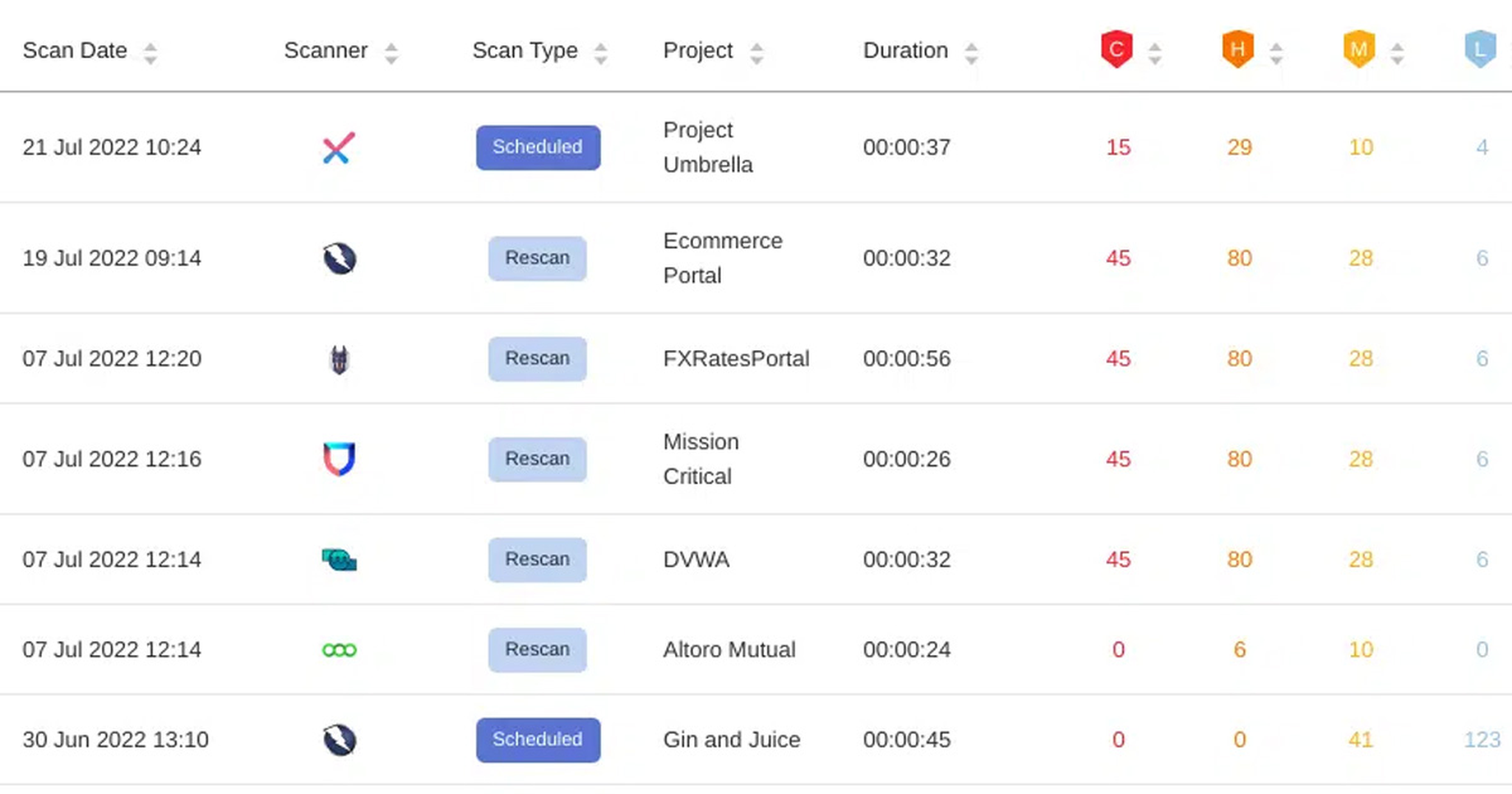
Vulnerability management for DevSecOps
Unified view across all scanners (commercial + open source) with automatic normalization and deduplication.
Threat intelligence enrichment to adjust risk scores centrally before teams triage.
Hierarchical rollups (org → business unit → product → project) for posture at every level.
Developer/owner views and code-owner mapping to consolidate issues by who introduced them.
110+ native integrations plus “bring your own data” to ingest findings from anywhere (APIs, CI/CD, bug bounty, issue trackers).

Contextual data for all stakeholders with RBAC
Role-based access control (RBAC) ensures users only see data relevant to their role.
Context-specific dashboards and permissions for developers, AppSec engineers, team leads, and managers.
Isolated data views prevent unnecessary noise and protect sensitive vulnerability details.
SSO integration with Azure AD for automated user and team provisioning.
Consistent user management across on-prem, private cloud, and SaaS deployments.
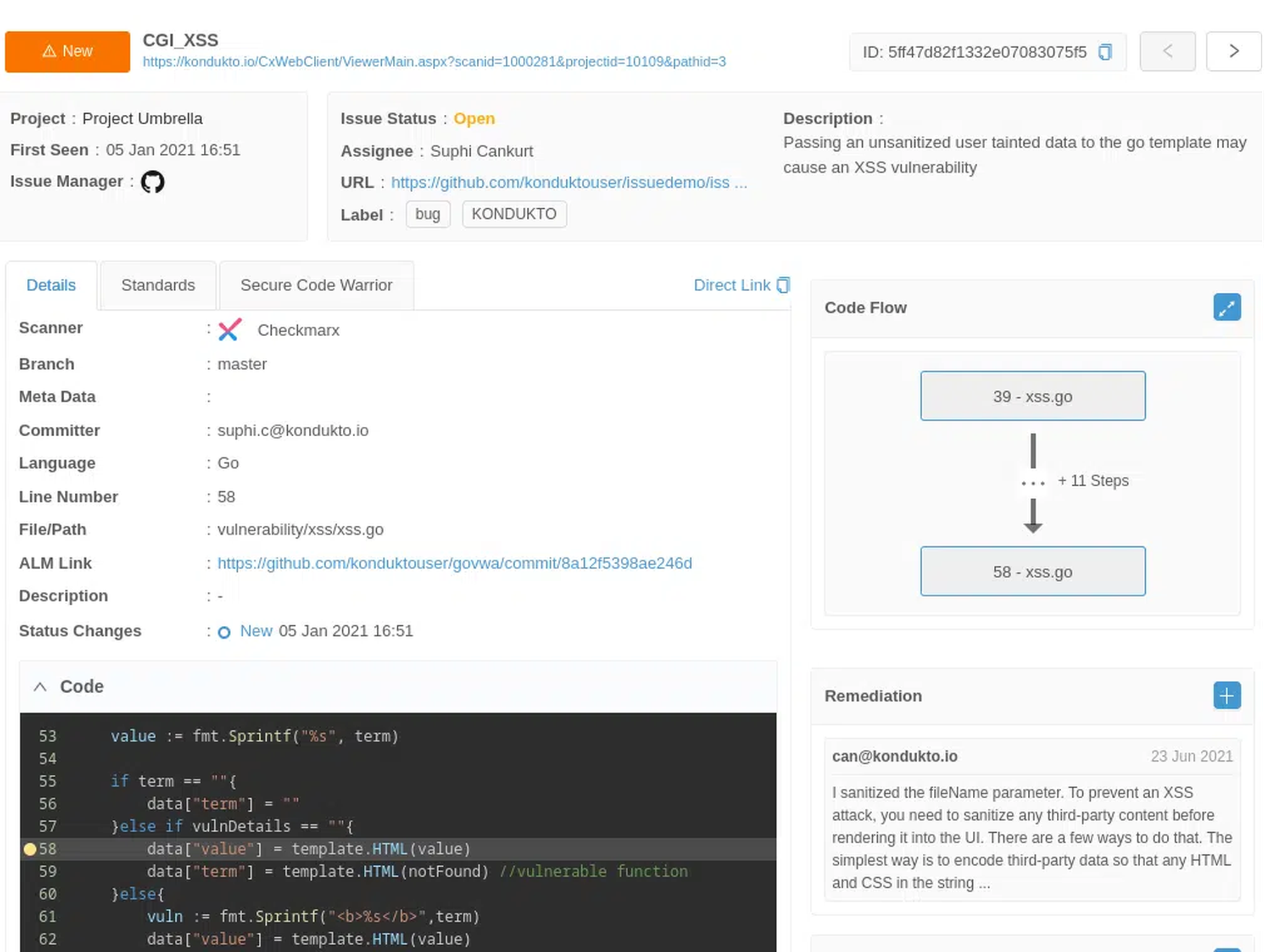
Corporate memory
Centralized Vulnerability DB preserves all historical scan data across tool changes.
Maintains a continuous record of vulnerabilities, triage actions, and remediation history.
Prevents data loss when replacing or deprecating scanners, CI/CD tools, or issue trackers.
Retains developer and project-level context, even when team members leave.
Ensures audit readiness by keeping logs and reports accessible for compliance reviews.
Integrated with the tools you already use
What customers say

“For more websites, we now don’t need to go externally for security testing. We can fire up Invicti, run the tests as often as we like, view the scan results, and mitigate to our hearts’ content. As a result, the budget we were spending every year on penetration testing decreased by approximately 60% almost immediately and went down even more the following year, to about 20% of our initial spending.”

“Invicti detected web vulnerabilities that other solutions did not. It is easy to use and set up...”

“I had the opportunity to compare expertise reports with Invicti ones. Invicti was better, finding more breaches.”

“Invicti is the best web application security scanner in terms of price-benefit balance. It is a very stable software, faster than the previous tool we were using and it is relatively free of false positives, which is exactly what we were looking for.”
Featured resources
Get single-pane visibility, automatic remediation, and measurable results.
Centralized risk dashboard across all applications
Workflow automation to accelerate fix cycles
Proof-based scanning to eliminate false positives
Continuous asset discovery across environments