WordPress vulnerability scanner: Secure your site with Invicti
Identify over 10,000 known vulnerabilities in WordPress and its plugins and actively scan for thousands more.

G2 Awarded
WordPress powers more than 40% of all websites, making it the most widely used content management system (CMS) on the internet. Its ease of use, rich plugin ecosystem, and flexible architecture make it the go-to platform for blogs, e-commerce sites, corporate portals, and everything in between. But this widespread adoption also makes WordPress a top target for attackers.
Security risks in WordPress stem not only from core software vulnerabilities but also from themes, plugins, and configuration oversights. And with frequent content and plugin updates, maintaining a secure posture requires more than just occasional manual checks. This is where Invicti’s dynamic vulnerability scanner delivers real value—offering accurate, automated, and continuous protection for any WordPress deployment.
What is a WordPress vulnerability scanner?
A WordPress vulnerability scanner is a tool designed to detect security flaws in WordPress websites. These flaws can exist in the core platform, installed plugins or themes, or custom code. While traditional scanners often rely on static checks or known signature databases, these approaches can miss context-sensitive issues or fail to detect vulnerabilities in complex, dynamic environments.
Invicti, by contrast, uses dynamic application security testing (DAST) to run active security checks in addition to identifying known vulnerable components. It scans WordPress websites in their running state, analyzing real traffic and behavior to uncover actual, exploitable security risks—providing far more reliable results.
How Invicti secures WordPress websites
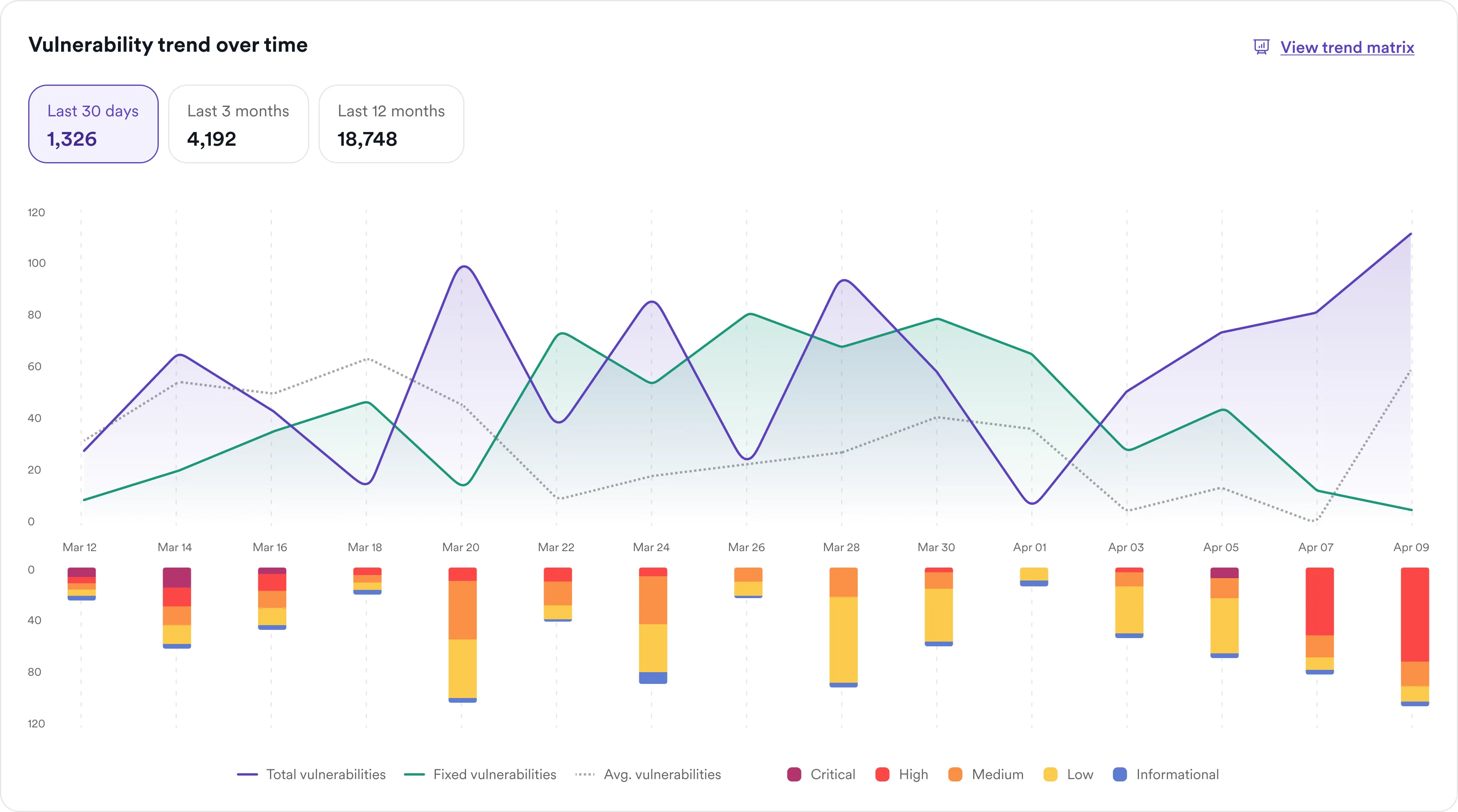
Invicti is built to scan live WordPress installations in depth and at scale using a dual approach. By fingerprinting WordPress components and plugins, Invicti can identify over 2,000 CVEs specific to WordPress and over 8,000 known vulnerabilities in WordPress plugins. On top of checking for known issues, Invicti actively and safely simulates attacks to reveal how your site would respond under real-world threat conditions.
Whether you’re working with a simple blog or a complex enterprise multisite setup, Invicti adapts to your environment. It tests public pages, restricted content, and custom functionality to ensure your entire site is secure—including your WordPress instances.
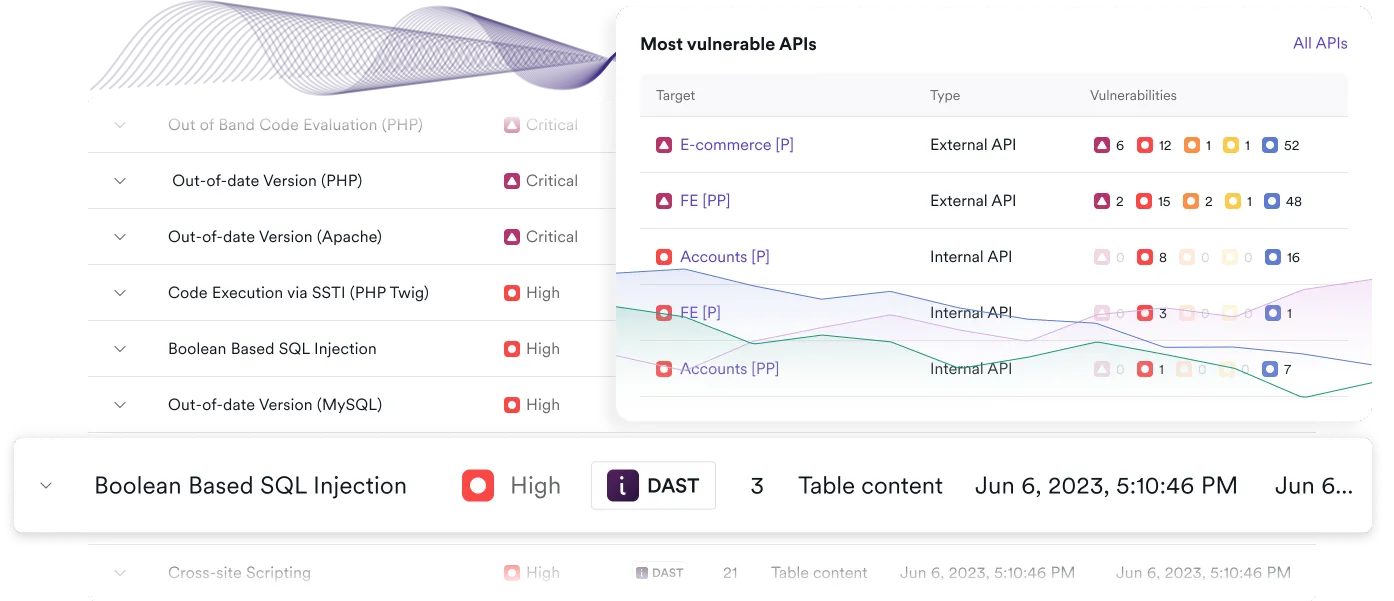
Invicti scans for a wide array of security risks—including SQL injection (SQLi), cross-site scripting (XSS), cross-site request forgery (CSRF), remote code execution (RCE), file inclusion vulnerabilities, and more. These tests cover both the WordPress core and the extensive ecosystem of plugins and themes, which are often overlooked by less sophisticated tools.
Apart from active security checks, Invicti can also detect over 2,000 WordPress CVEs and over 8,000 known vulnerabilities in WordPress plugins. While only a small part of Invicti’s overall scanning capabilities, this covers much of the functionality of specialized WordPress scanners.
Once set up with authentication, Invicti’s crawler intelligently navigates both the public and admin sections of your WordPress site. It maps the structure of your application, discovers hidden inputs and forms, and ensures no attack surface is left untested. This includes login-restricted content, custom post types, and AJAX endpoints.
One of Invicti’s standout features is proof-based scanning. When a vulnerability is found, Invicti automatically confirms it with a safe, non-destructive proof of exploit. This unique capability drastically reduces false positives and streamlines the remediation process—saving valuable time for security and development teams.
WordPress authentication flows can vary, especially with custom login pages, multi-role setups, or membership-based access. Invicti handles these seamlessly, maintaining sessions, managing CSRF tokens, and testing permissions across user roles. You get full visibility into vulnerabilities that only appear behind the login screen.
For teams embracing DevOps or running frequent WordPress updates, Invicti integrates directly into CI/CD workflows. You can automatically scan each deployment for regressions or new risks, ensuring continuous security coverage with minimal manual overhead.
Why Invicti is ideal for enterprise WordPress security
Invicti is purpose-built for dynamic, real-world web environments—making it a natural fit for WordPress. It’s trusted by agencies managing multiple client sites, enterprises running large-scale content platforms, and internal security teams seeking consistent results across complex setups.
With a DAST-first approach, Invicti prioritizes the vulnerabilities that matter most: those that attackers can actually exploit. Rather than flooding you with alerts, it focuses your attention on confirmed, actionable issues.

Scan and secure your WordPress site with Invicti
From popular plugins to custom themes, WordPress websites come with a wide range of potential security gaps. Invicti helps you close them with powerful dynamic scanning, automatic vulnerability validation, and deep integration into your existing workflows.
Ready to strengthen your WordPress security? Start a free trial or request a demo to see how Invicti helps protect your websites from the inside out.

3600+ Top Organizations Trust Invicti

















Save your security team hundreds of hours with Invicti’s web security scanner.






