Stop IaC Vulnerabilities Before Production
Detect misconfigurations early, enforce security policies in CI/CD, and track IaC risk alongside code and runtime findings.

3600+ Top Organizations Trust Invicti
























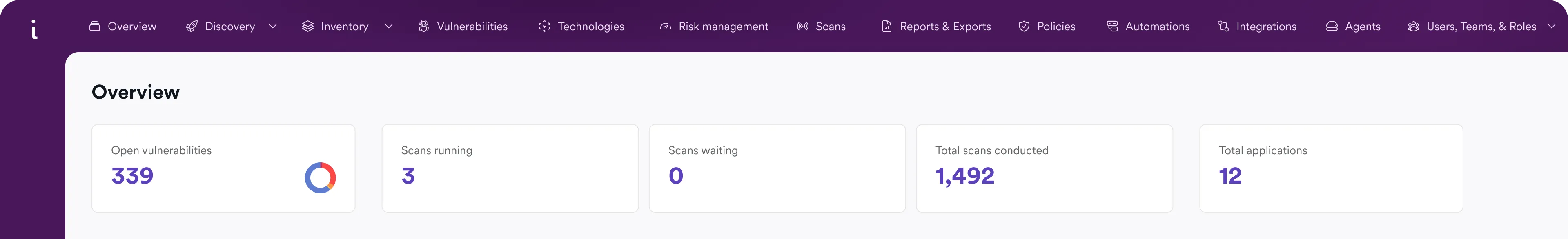
IaC Security at the Speed of DevOps
Secure cloud infrastructure before deployment by orchestrating IaC security checks across your pipelines and managing risk in one place.
Remove False Positives
Cut noise and surface only meaningful security findings.
Prioritize Real Threats
Focus teams on the risks that matter most.
Deliver Impactful Reports
Show leaders clear, measurable risk reduction.
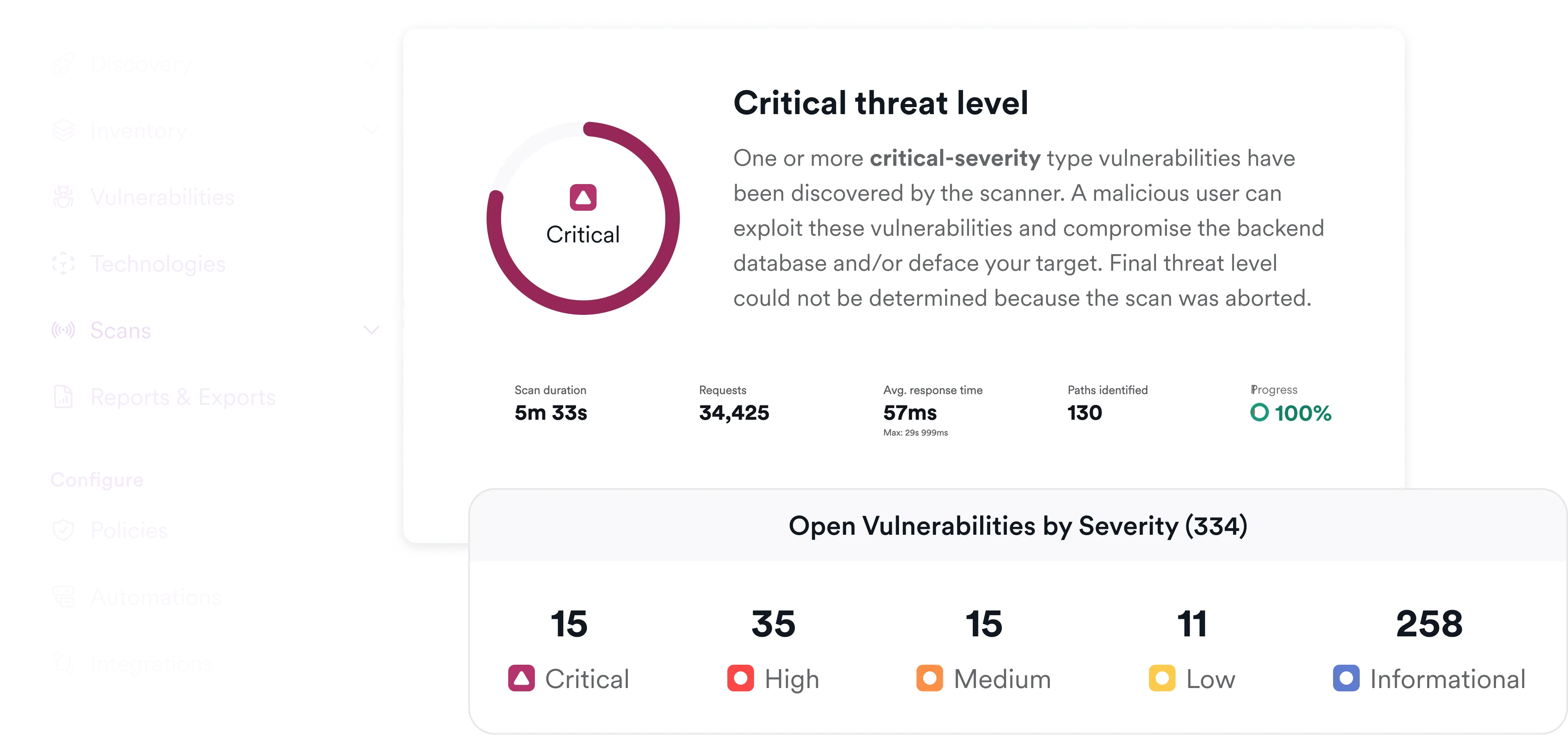
Orchestrate and Correlate IaC Scans
Trigger Infrastructure as Code security checks and correlate findings with runtime exposure.
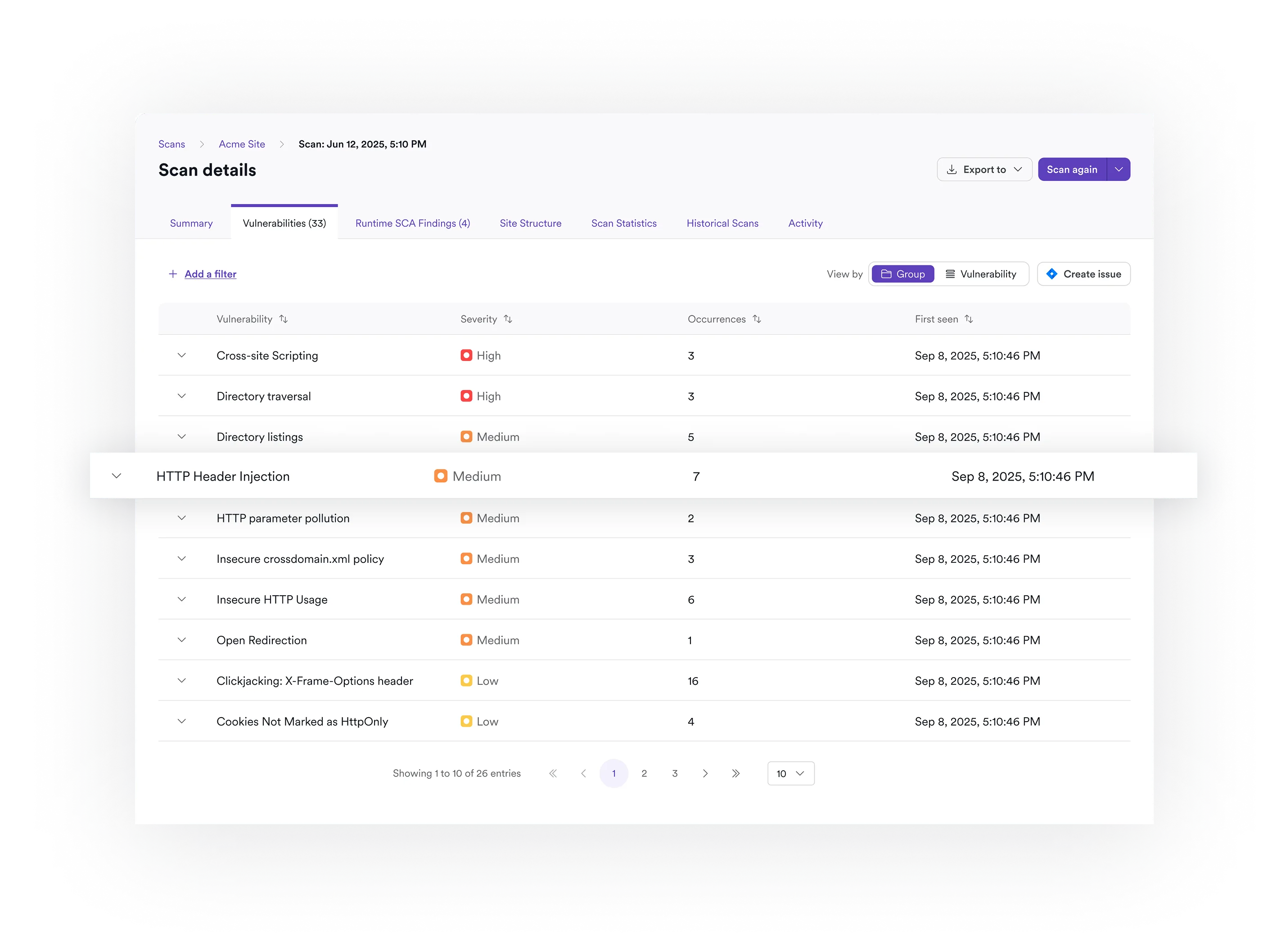
Focus on Real Risk
Cut through misconfiguration noise and prevent risky infrastructure changes from reaching production.

Track IaC Security Over Time
Prove that infrastructure risk is being managed.

Frequently asked IaC questions
Infrastructure-as-Code (IaC) scanning analyzes infrastructure definition files—such as Terraform, CloudFormation, and Kubernetes manifests—for risky configurations before they are deployed. Scanning IaC early helps prevent insecure defaults, cloud exposure, and access misconfigurations from becoming live attack paths in production.
Invicti integrates IaC security checks directly into CI/CD pipelines by orchestrating scans during pull requests, builds, or pre-deployment stages. IaC findings are collected, normalized, and evaluated against policy so teams can stop risky infrastructure changes before they reach production.
Invicti orchestrates industry-standard scanners to support common frameworks including:
- Terraform
- CloudFormation
- Kubernetes manifests
- Helm charts
- Cloud infrastructure templates
This allows teams to apply consistent IaC security controls regardless of the tools or formats they use.
The open-source IaC scanners Invicti orchestrates are designed to run quickly in CI/CD environments. Invicti helps teams control when and how scans run so IaC security checks don’t introduce unnecessary pipeline delays.
Protect IaC at the Speed of DevOps