Stop Secret Exposure Before Production
Invicti finds and surfaces exposed API keys, passwords, encryption keys, and tokens before hackers get the chance to exploit them.

3600+ Top Organizations Trust Invicti
























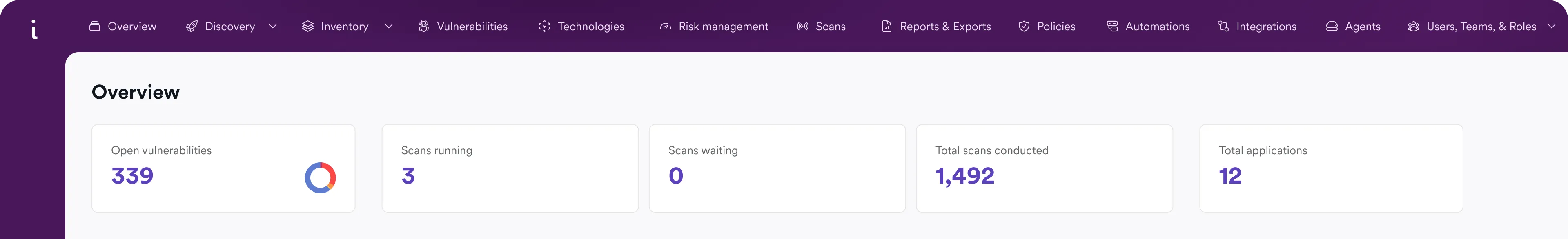
Scan, Find, and Prioritize Secret Exposures
Secrets like API keys, tokens, and credentials are frequently exposed in source code, configuration files, and repositories. Invicti helps teams detect exposed secrets early and manage them in context to reduce real risk without overwhelming developers.
Find Secrets Early
Find and fix secret exposures introduced during development.
Prioritize Real Threats
Filter noise and rank exposed secrets by severity and context.
Deliver Impactful Reports
Measure secrets remediation and track clear progress for leadership.
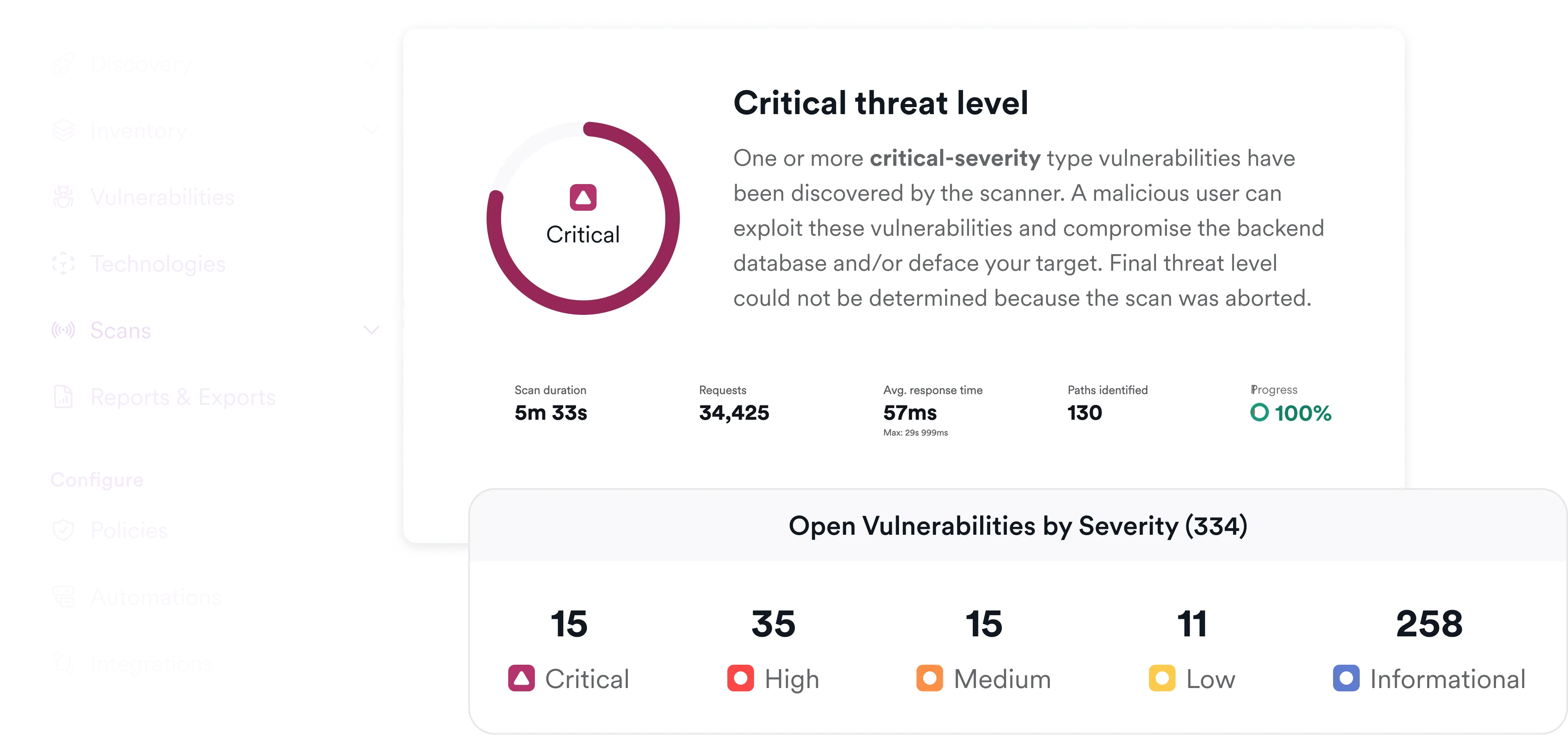
Catch Issues Before They're Costly
Invicti detects exposed secrets early in the development lifecycle, helping teams address issues before applications are deployed.
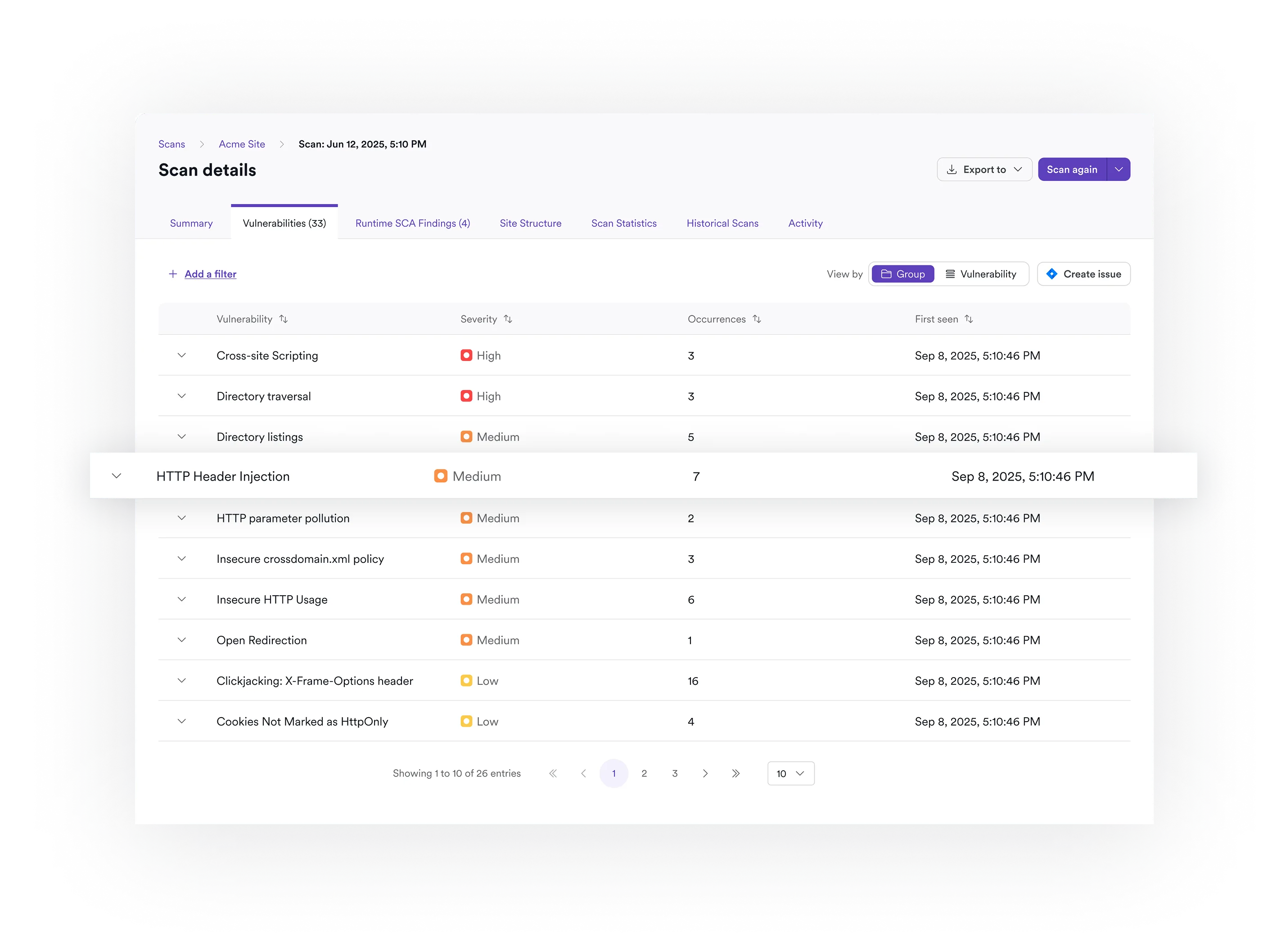
Focus on Real Risk
Focus your team on real risk by reducing noise and prioritizing exposed secrets that require action.

Manage and Report Secrets With Context
Prove that secret risks are being properly triaged.

Frequently asked Secrets questions
Invicti detects exposed credentials such as API keys, tokens, passwords, and other sensitive values embedded in source code and configuration files.
Invicti helps teams identify exposed secrets early in the development lifecycle so issues can be addressed before applications are deployed. Prevention depends on how teams choose to act on findings within their development workflows.
Secrets scanning is enabled automatically in Invicti AppSec Core, with no manual configuration required to get started.
Invicti identifies exposed secrets using pattern-based detection combined with additional heuristics to distinguish likely secrets from non-sensitive values.
Invicti applies deduplication, suppression, reachability, and business intelligence to reduce noise from values that resemble secrets but do not pose real risk.
Secrets scanning is part of Invicti’s code security capabilities and integrates into a centralized view of application risk, alongside application, API, and runtime vulnerabilities.
Find and Remediate Exposed Secrets