Manage Cloud-Based AppSec
Cloud application security that finds exploitable risk across IaC, containers, APIs, and production apps.

3600+ Top Organizations Trust Invicti
























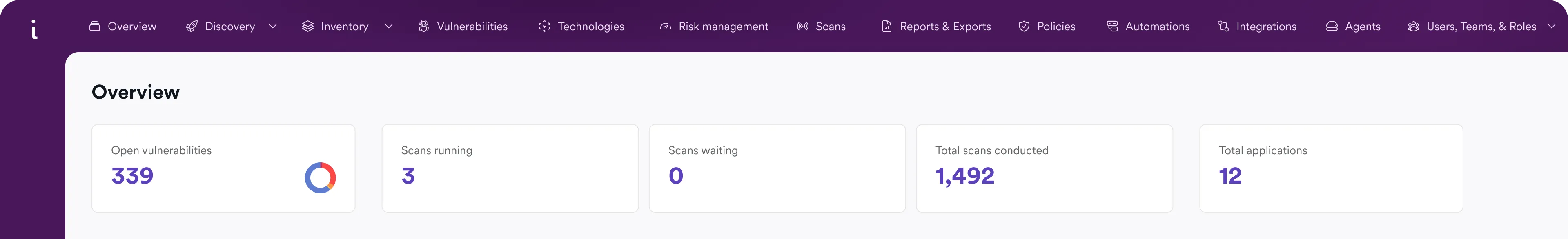
Find, Prioritize, and Secure Cloud App Risk
Cloud-deployed applications create risk across code, containers, APIs, and runtime.
Invicti finds and correlates misconfigs, secrets, and exploits in one clean view of prioritized vulnerabilities for your team to remediate.
Identify Risk Early
Catch security issues in code, configurations, dependencies, and containers before they reach production.
Secure Cloud Apps
Test cloud-deployed applications and APIs for exploitable vulnerabilities as attackers would.
Prioritize Real Risk
Correlate findings across the stack and focus teams on the vulnerabilities that pose real, proven risk.
Catch Issues Before They're Costly
Scan code, configurations, and dependencies during development to reduce downstream risk without slowing delivery.
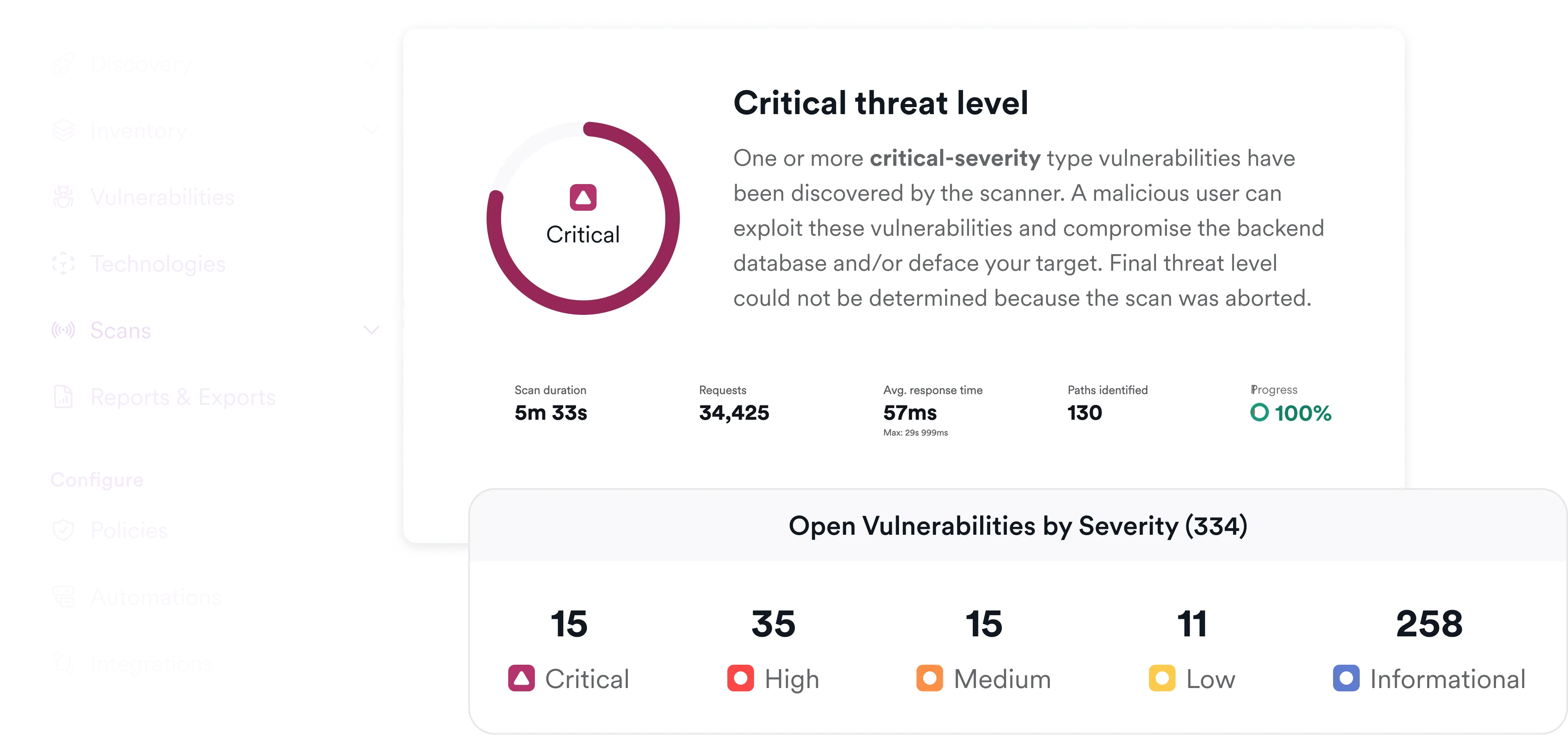
Secure What's Running in Cloud
Test applications as they actually run in the cloud. Find and validate exploitable vulnerabilities attackers can reach.

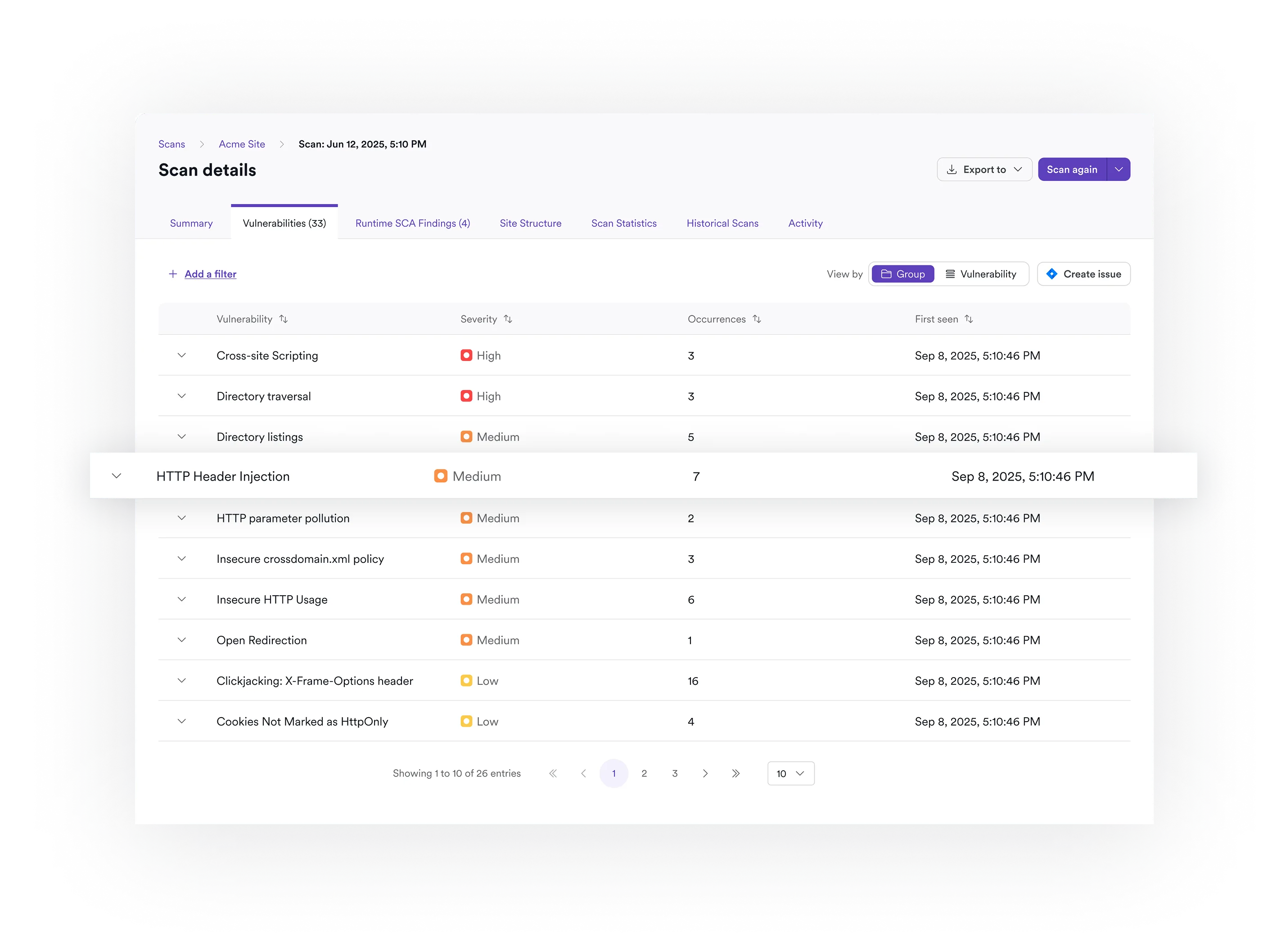
Correlate and Prioritize Risk in a Single View
Correlate and prioritize risk across your entire attack surface. One clean view shows your team what's exploitable and what needs to be prioritized.

Frequently Asked Cloud AppSec Questions
Cloud-based AppSec focuses on securing applications and APIs running in the cloud. It tests how real attackers can exploit your live apps, regardless of where they’re hosted.
Invicti supports common IaC formats such as Terraform, CloudFormation, and Kubernetes manifests, enabling early detection of risky cloud configurations in CI/CD pipelines.
IaC scanning prevents insecure configurations before they’re deployed, while CSPM monitors cloud environments after deployment. Invicti focuses on early prevention and application-layer risk—not continuous cloud account monitoring.
CSPM tools monitor live cloud infrastructure for configuration and compliance issues like IAM, storage, and network settings. Invicti focuses on application-layer risk: scanning code, dependencies, APIs, and running applications to find exploitable vulnerabilities.
Invicti secures everything from code and configurations to containers and running applications. This includes IaC, open-source dependencies, container images, APIs, and production runtime behavior.
Yes. Invicti identifies vulnerable open-source dependencies and base images used in cloud-native applications, helping teams manage software supply chain risk.
Silence Noise and Remediate Application Vulnerabilities in the Cloud