Enhancing AppSec through Fuzzing in CI/CD Pipelines
Learn more about how integrating fuzzing into your CI/CD pipeline can help you to uncover vulnerabilities and enhance your application security.

In this blog, we are going to take a closer look at the concept of fuzzing, using Go, and how to integrate it into your CI/CD pipeline. As a quick primer, fuzzing is an automated testing technique that involves feeding random, unexpected, or invalid data to a program or API to uncover bugs and vulnerabilities. The core idea is to expose the program to inputs that developers may not have anticipated, thereby revealing flaws such as crashes, memory leaks, and security vulnerabilities.
Fuzzing in Go
Fuzzing capabilities are directly baked into the Go programming language (as of Go 1.18) itself. They offer a streamlined way to add fuzz testing into your development workflows. Leveraging Go's native tools and idioms, they make it easy and accessible for Go developers to adopt fuzzing techniques without a steep learning curve.
Integrating it into CI/CD Pipelines
Integrating fuzzing into CI/CD pipeline ensures that your code is continuously tested for unexpected inputs which could lead to vulnerabilities. Here is how you can integrate it into GitHub and GitLab:
Using GitHub Actions
Create a .github/workflows/go-fuzz.yml file in your repository:
Using GitLab CI/CD
Add the following in .gitlab-ci.yml in your repository:
How Fuzzing Helps
Let’s take a look at how fuzzing can help you to identify security issues. As an example, we can use fuzzing to uncover an existing vulnerability (GO-2022-0211) within the net/url package. Specifically, the url.Parse function in this package accepts URLs with malformed hosts, allowing arbitrary suffixes in the Host field. These suffixes don’t appear in either Hostname() or Port(), potentially leading to authorization bypasses in certain application versions, as illustrated in the following examples:
Example Code
Fuzz Test Code
Running the Fuzzer
To run the fuzzer, simply use the following command:
go test -fuzz=FuzzURLParse -fuzztime=60s
Fuzzing for APIs
In a previous blog we demonstrated how continuous fuzzing can increase the overall robustness and quality of your code. We also integrated ParseRequestURI logic and a related fuzzing test into the test code. The result was the following unicode error:
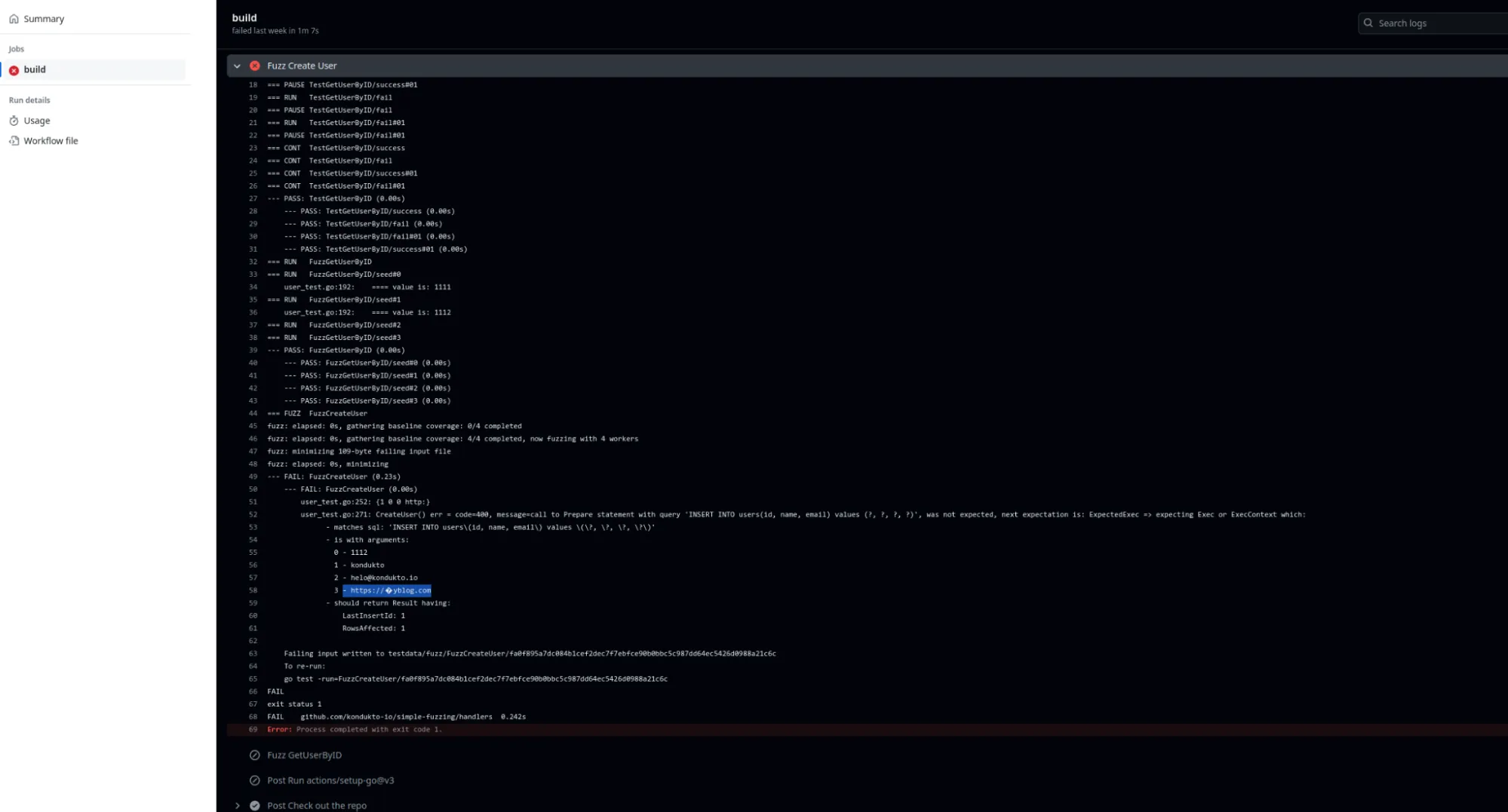
What Happened?
The fuzz test showed that a database operation failed because the output of ParseRequestURI being unicode which is fed by the fuzzer.
Further analysis shows that ParseRequestURI only checks for a certain range of ASCII code. Unlike Python’s urllib.parse library, which has Unicode checks and states that input validation is required while using it, the Go documentation does not mention anything similar. It only says that it assumes that URL was received in an HTTP request. This may lead to situations where developers use ParseRequestURI thinking that it performs the required checks for validating the URLs.
Conclusion
Integrating fuzzing into your CI/CD pipelines can significantly enhance application security by continuously testing for unexpected inputs that could lead to vulnerabilities. For applications written in Go, its native fuzzing capabilities can be easily adopted for this technique. This proactive approach helps identify and mitigate potential security issues early in the development process, ensuring more robust and secure applications.
References
- https://www.invicti.com/blog/web-security/how-to-integrate-continuous-api-fuzzing-into-cic
- https://go.dev/doc/security/fuzz/
- https://pkg.go.dev/vuln/GO-2022-0211
- https://www.cve.org/CVERecord?id=CVE-2019-14809
- https://osv.dev/vulnerability/GO-2022-0211
- https://go.googlesource.com/go/+/61bb56ad63992a3199acc55b2537c8355ef887b6


