May 2022 update for Invicti Enterprise On-Premises
We’re delighted to announce the release of Invicti Enterprise On-Premises 2.3 (formerly Netsparker Enterprise). The new release rolls together with a wide range of updates and improvements, most notably a new brand identity, Node.js IAST checks, an all-new Software Composition Analysis feature, support for GraphQL APIs, and an improved Authentication Verifier. We have also added many new security checks, improvements, and fixes.
Your Information will be kept private.
Begin your DAST-first AppSec journey today.
Request a demo
Netsparker is now Invicti
We have renamed our flagship product Netsparker to Invicti. To reflect this rebranding, we have updated the user interface. From the login page to the links for getting more information, the application now carries the Invicti brand.

For more information on this important change, see A new era for modern application security: Netsparker is now Invicti.
Node.js sensor for Invicti Shark IAST
We’ve expanded the capabilities of our IAST module by adding a Node.js sensor to deliver additional insights when scanning modern applications with JavaScript on the server-side.
To use the new capability, you simply install a dedicated IAST agent in your Node.js application environment. Once deployed, the agent will provide the main DAST scanner with extra information about application behavior during vulnerability testing.
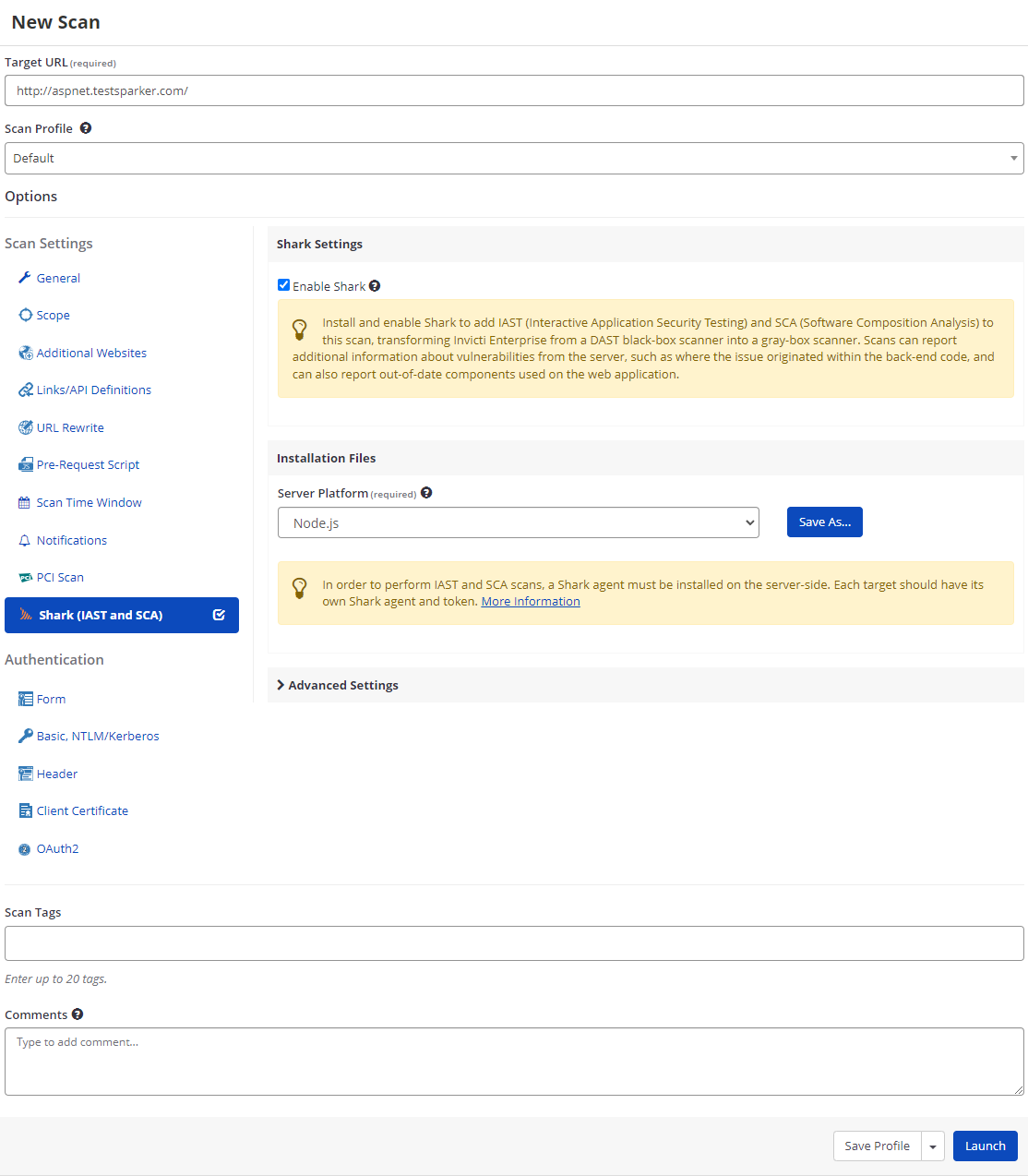
For further information, see Invicti adds IAST support for Node.js. To deploy the sensor, see Deploying Invicti Shark for Node.js.
Bridge URL and Shark token support for Invicti Shark IAST
In addition to the Node.js support, we have also added support for a bridge URL and Shark tokens in Invicti IAST.
- Shark tokens are now used to secure communication between the Invicti scanner and the IAST agent. A unique token is automatically generated for each installation of the Shark agent. The token is mandatory for using Invicti Shark IAST.
- The IAST bridge is used to relay information from the Shark agent to the Invicti scanning engine. Specifying a bridge URL is mandatory for the Java, .NET, and Node.js sensors. You can use the default URL or install your own bridge. For more information, see Deploying Shark (IAST) in Netsparker Enterprise On-Premises.
Software Composition Analysis (SCA)
We’ve added the ability to run software composition analysis from Invicti Enterprise. With the Shark IAST agent installed, Invicti can now detect components and technologies used in your web application. It tracks their use and reports any problems, such as whether any of the technologies are out-of-date or whether a specific version has known issues.
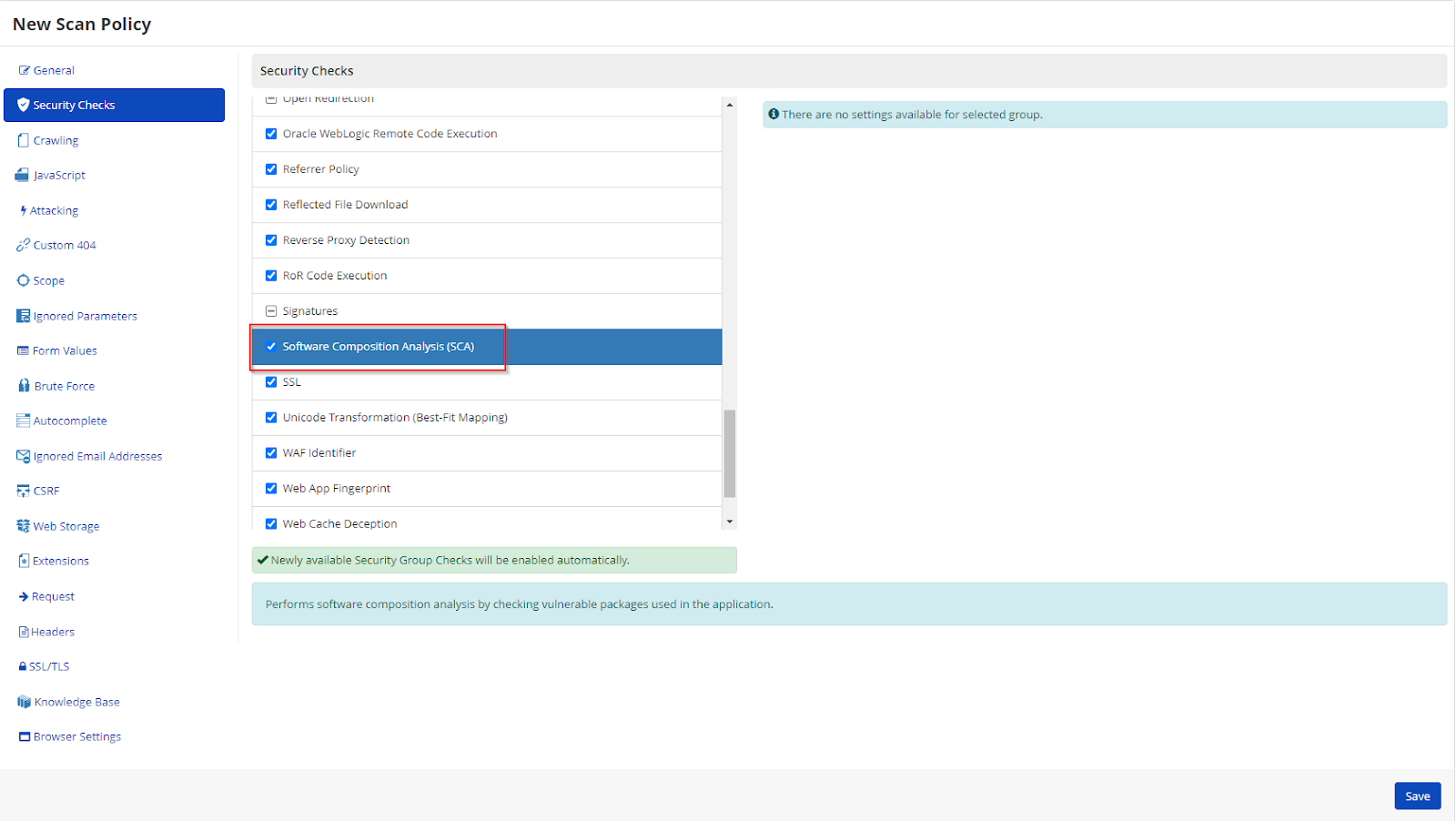
For further information, see Analyzing software composition with Invicti Shark (IAST).
Support for scanning GraphQL APIs
We now have support for scanning GraphQL-based application programming interfaces (APIs). You can import a GraphQL schema into Invicti Enterprise and scan it to identify vulnerabilities.
Originally developed by Facebook in 2012 and publicly released in 2015, GraphQL was designed to provide a database-like query language for APIs. Having a query language makes it easier and quicker to get specific data from a server to a client via a single API call. Despite some built-in data validation and type-checking, GraphQL still has its security shortcomings that attackers can exploit to access sensitive data.
With this update, you can specify your GraphQL schemas in scan profiles to identify GraphQL vulnerabilities.
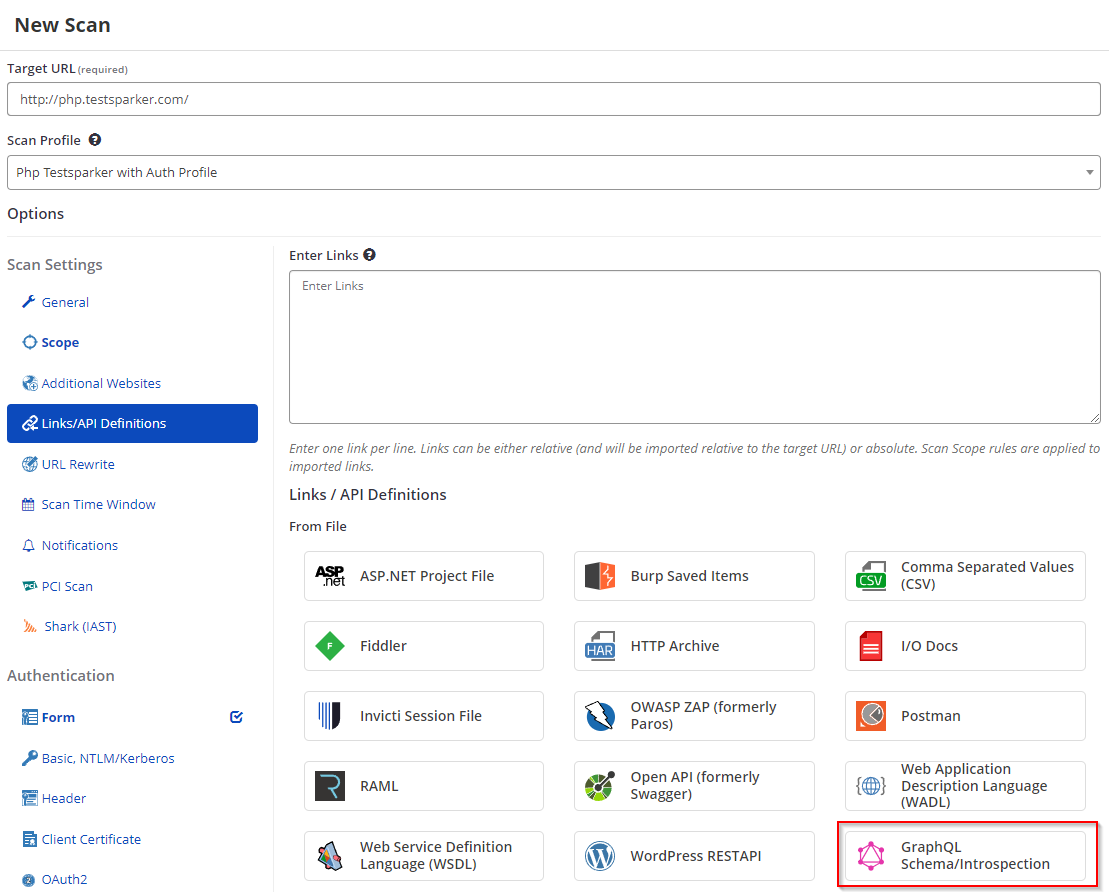
For further information about GraphQL and its attack vectors, see our blog post Introduction to GraphQL API security. For support information on setting up GraphQL scans, see Scanning a GraphQL API for vulnerabilities.
Improvements to the Authentication Verifier agent
We have improved the Authentication Verifier agent. The new version provides improved performance for single-page applications, is less resource-intensive, and comes with an auto-update feature. You can now also install multiple verifier agents.
Using the new version of the Authentication Verifier requires re-installation. If you have older versions in your environment and wish to install the new, improved version, you will need to remove the old versions first.For further information, see Authentication Verifier Settings
Please note that the authentication verifier agent is an optional component. If you are scanning a website that requires form-based authentication, it is recommended that you download and install an authentication verifier agent. This internal agent assists in the authentication process to ensure that you can run authenticated scanning in your network.
New OWASP reports
We have added two new OWASP reports: OWASP API Top Ten Report and OWASP Top Ten 2021.
OWASP API Top Ten
The Open Web Application Security Project (OWASP) API Top 10 2019 is a list of top security concerns specific to web Application Programming Interface (API) security.
APIs are a critical part of modern mobile apps, Software as a Service (SaaS) products, and web applications. Because APIs directly expose application logic and sensitive data, they have become a prime target for attackers. While general web application security best practices still apply to APIs, the OWASP API Security project has prepared a list of top 10 security risks specific to web API security.
For further information, see OWASP API Top Ten 2019 Report.
OWASP Top Ten 2021
OWASP Top Ten 2021 Report helps you test for the most dangerous web application security weaknesses.
Since the first edition in 2003, the list of top ten application security risks reflects industry trends, web technologies, and the threat landscape. Thanks to the OWASP Top Ten 2021 Report, you can identify common weaknesses that could be present in your web application environment and exploited by malicious attackers.
For further information, see OWASP Top Ten 2021 Report.
FIPS compliance
We’ve updated the .NET Framework version used by Invicti Enterprise from 4.7.2 to 4.8. With this change, Invicti has become compatible with the Federal Information Processing Standard (FIPS) 140-2.
In practice, this means you can now smoothly run Invicti on machines where the FIPS policy is enabled. More specifically, when you run or install Invicti on a machine with the FIPS policy enabled, the policy does not interfere in any way with the running state of the software. Additionally, no error event log entries are recorded.
For further information, see Invicti’s approach to FIPS.
WCAG compliance
At Invicti, we have adopted the Web Content Accessibility Guidelines (WCAG) 2.1 Level AA as our standard and goal. This enables greater innovation, easier collaboration, and a much more inclusive work environment.
As one of few AppSec testing tools with WCAG 2.1 AA compliance, we’re committed to investing the time and resources necessary to maintain that standard. This means making sure we build accessibility into all of our new Invicti Enterprise product features and consistently monitoring the W3C for updates.
For further information, see Invicti Enterprise achieves WCAG 2.1 accessibility compliance.
Further information
For a complete list of what is new, improved, and fixed in this update, refer to the Invicti Enterprise Changelog.





