Authenticated Vulnerability Scanning with Invicti
Testing websites and applications that require authentication can be a challenge for some automated vulnerability scanners. Invicti features configurable support for modern authentication methods to help you bring accurate and detailed vulnerability scanning to all your web assets.
Your Information will be kept private.
Begin your DAST-first AppSec journey today.
Request a demo
The Importance of Authenticated Scanning
Less advanced dynamic application security testing (DAST) products can struggle with authentication, leading them to skip restricted sections and leave unchecked vulnerabilities in your environment. They might also require risky workarounds, such as scanning with authentication disabled. This is especially dangerous considering that pages which require authentication are precisely the ones that attackers are most likely to target.
Invicti’s extensive support for authenticated scanning means you can test applications in their ready-to-run configuration, including any authentication, both in staging and production environments. Invicti probes the entire application in exactly the same way that a real-life authenticated attacker would. That way, you can have full confidence in your scan coverage and results.
The Challenges of Automating Scanner Authentication
As a black-box vulnerability scanner, Invicti works by checking for vulnerabilities across all accessible parts of a web application. To do this, the scanner first needs to identify the attack surface of the target application by visiting every link it finds in web pages and making requests to all input points in detected web assets. This includes the URLs used to reach these assets.
While crawling web pages that are accessible to all users is relatively easy, password-protected web pages have always posed a challenge for security scanners due to the variety of methods used to authorize page access. Beyond basic login forms, sites may use OAuth, set custom session cookies, require single sign-on (SSO), and so on.
Even with form-based authentication, the login form may, for example, use non-standard form elements, require additional fields (maybe to select a department from a drop-down list), use CAPTCHA verification, or span multiple pages. And if the scanner can’t log in, it can’t test the page for vulnerabilities.
Invicti comes with an easy-to-configure authentication module that allows it to access and scan password-protected web applications and website sections. Credentials are configured without the need to record login macros. Supported authentication methods include Basic, Form-based, NTLM, Digest, Kerberos, Client Certificate, and Smart Card.
Form-Based Authentication
Form authentication is the most common authentication method in today's web applications. However, it is also the most difficult one to support, as developers use many different approaches to secure authentication forms and user data against attackers. In practice, this means that entering a username and password often isn’t enough to authenticate yourself in the system, making it much harder for automated scanners to authenticate and scan restricted web pages.
Invicti supports a variety of form authentication methods to make sure that it can crawl and scan all pages. When the form authentication method is selected, Invicti completes and submits login forms via the DOM structure of the login form page, without the need to record login macros. It automatically detects the login form components, including the user name and password input fields, automatically populates them with preconfigured values, and submits the login form.
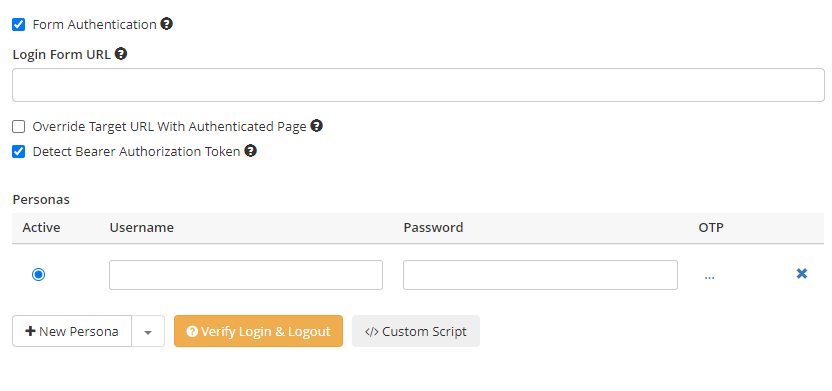
Interactive Login
Sometimes, the login process may not be so straightforward, as many web applications use additional authentication mechanisms (such as CAPTCHA) to enhance user security. Invicti supports these cases using its interactive login feature. If you check the Interactive login box when setting up authentication, Invicti will show a dialog for entering the necessary data.
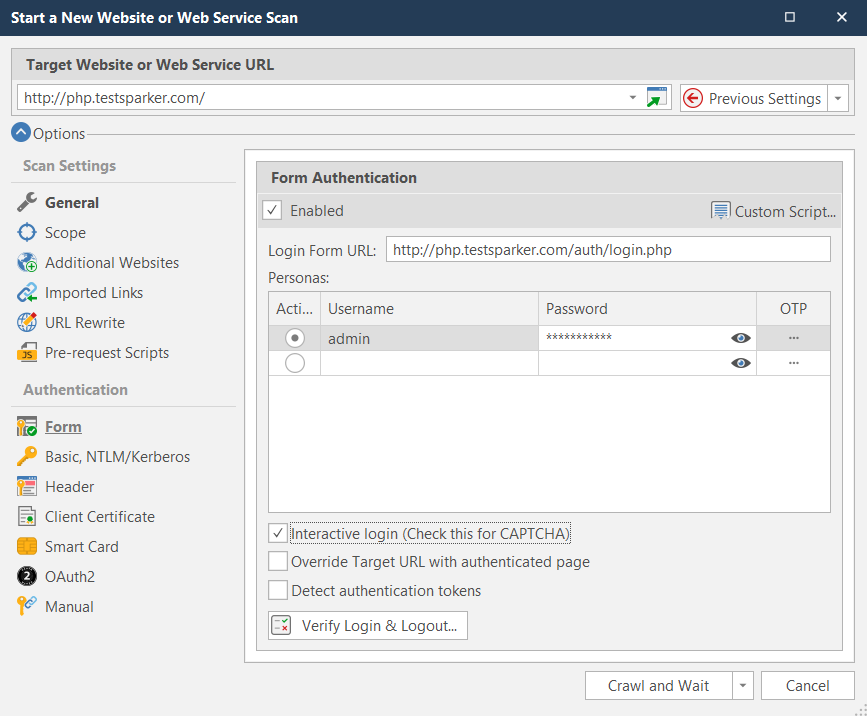
Here are a few scenarios where you may need the interactive login feature:
- When the website requires a CAPTCHA to authenticate the user or authorize access to a particular area.
- When the website requires you to enter a dynamic token value like a 2FA PIN during authentication.
- If you are unable to configure Invicti to complete the login form automatically and want to manually perform authentication.
You can also mix and match the interactive login functionality with the automatic login capability and custom scripting support. In these cases, you can configure the credentials and also enable the Interactive login option. Invicti will first submit the regular login form details and then will prompt you for the interactive login details, such as a 2FA PIN.
To make sure that the information you entered can be used by Invicti to authenticate, you can click the Verify Login & Logout button to see for yourself. After you click it, Invicti will open a window and replay the authentication process.

Invicti can not only authenticate itself but also detect any logouts during scanning and log itself back in again. In the Verify Form Authentication window, you can configure the logout detection type to use. If needed, Invicti can automatically exclude authentication-related pages (login, logout, etc.) from the scan.
Configurable Authentication with the Custom Script Editor
Occasionally, you may need to modify Invicti’s automatic authentication so that it is suited to your website or application. Custom scripting support enables you to automate your specific form authentication process.
Custom scripts can be written in JavaScript. Invicti executes the code in the context of form authentication pages, where you can access and manipulate the page DOM. The code is executed after the page is fully loaded. To locate and complete login form controls, you can use any HTML API that modern browsers support. The custom script editor helps to automatically generate JS code for authentication page elements.
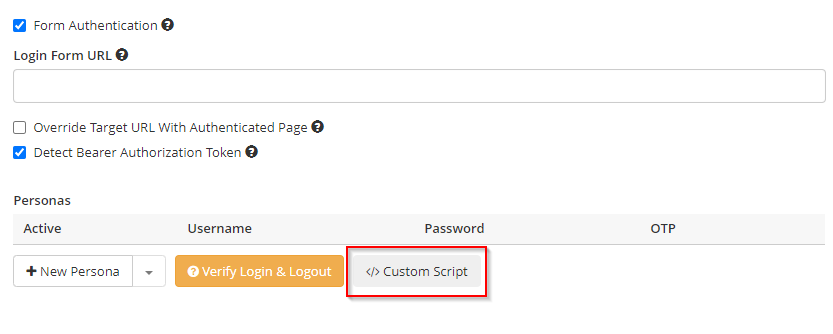
Privileged Access Management
Traditional form-based authentication requires you to explicitly provide a username and password. But what if you have a privileged access management (PAM) solution in your environment? Invicti provides out-of-the-box integrations with CyberArk and HashiCorp Vault so you can perform authenticated scanning without manually entering sensitive credentials. This also means you can change login credentials as often as you need without reconfiguring Invicti or affecting its ability to scan your applications and detect vulnerabilities.
HTTP Authentication
Invicti provides the same flexible and configurable authentication support for HTTP authentication. While form authentication can be cumbersome, HTTP authentication is much more straightforward. It is also done at the web server level, whereas form authentication is done at the web application level.
Invicti supports Basic, Digest, NTLM/Kerberos, and Negotiate HTTP authentication mechanisms. You can also set up support for authentication headers.
Smart Card and Client Certificate Authentication
In addition to form-based and HTTP authentication, Invicti supports smart card and client certificate authentication. A client certificate is a digital certificate that is used by client systems to prove their identity to the remote server. A smart card performs a similar role but is a physical device that enables users to authenticate with the system. Note that you can’t configure both client certificate authentication and smart card authentication at the same time.
OAuth2 Support
OAuth is an open standard for access delegation that allows Internet users to share their authorization status across websites and applications without exchanging plain-text credentials. In the beginning, Twitter, Google, and other companies supported this framework. It was formalized as an open standard in 2010 in RFC 5849 and quickly became widely adopted.
The OAuth2 authorization mechanism in Invicti supports all grant types that are defined in RFC-6749:
- Authorization code grant
- Client credentials grant
- Implicit grant
- Resource owner password credentials grant
In addition to OAuth2 flows, Invicti also has a custom flow that is used for token-based authentication.

Manual Authentication
In addition to all these automated authentication methods, you can also use manual tools to configure advanced local authentication in Invicti. With the manual authentication features, you can import requests from various file formats, such as Postman and Fiddler, and replay them at the beginning of a scan to perform authentication. You can also configure logout detection to have Invicti replay these requests if a logout occurs while a scan is in progress.
For more information and FAQs related to the authentication methods available in Invicti, see our support page on authentication.






