How Invicti Reports Inform Vulnerability Management
Invicti provides reports that give users information on the nature, severity, frequency, and other attributes of detected vulnerabilities. This blog post explains the purpose and layout of the main reports and report types available in Invicti: detailed scan reports, executive summary reports, comparison reports, and compliance reports.
Your Information will be kept private.
Begin your DAST-first AppSec journey today.
Request a demo
How Does Invicti Reporting Work?
Invicti works by scanning your target web applications to detect which vulnerabilities could be exploited and how. Following scans, you can view and download many types of reports. There are detailed reports that provide developers with essential information to enable them to prioritize, understand and fix issues; summary reports that are useful for managers and team leaders to monitor progress; comparison reports that help track progress over time; and compliance reports that give compliance officers information on where the gaps are. These reports are referred to as Report Templates. Security professionals work in a collaborative environment which brings challenges among developers to find the right balance between producing software and addressing detected vulnerabilities urgently. Invicti’s comprehensive and actionable reports help developers to tackle the most urgent detected issues first and hone their skills to produce software that is secure by design.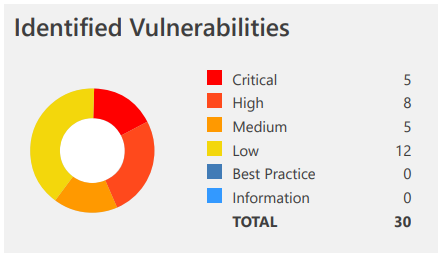
Detailed Scan Reports: Comprehensive and Easy to Understand
Invicti’s comprehensive technical reports are designed for those dealing with fixing vulnerabilities. Technical staff can employ them to easily grasp how Invicti has proved that the vulnerability can be exploited. To illustrate, technical reports such as the Detailed Scan Report provide a comprehensive security overview of the target web application. Written in a clear and accessible format, this report includes a summary that presents straightforward numerical and graphical information.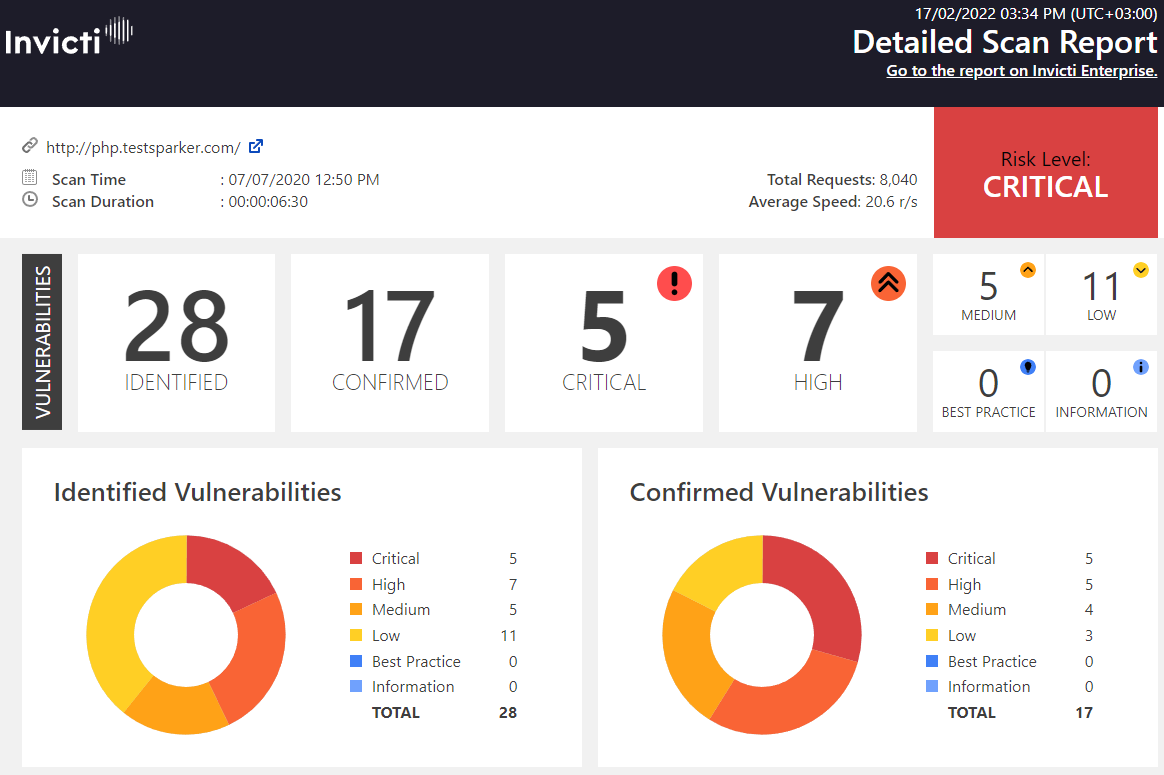
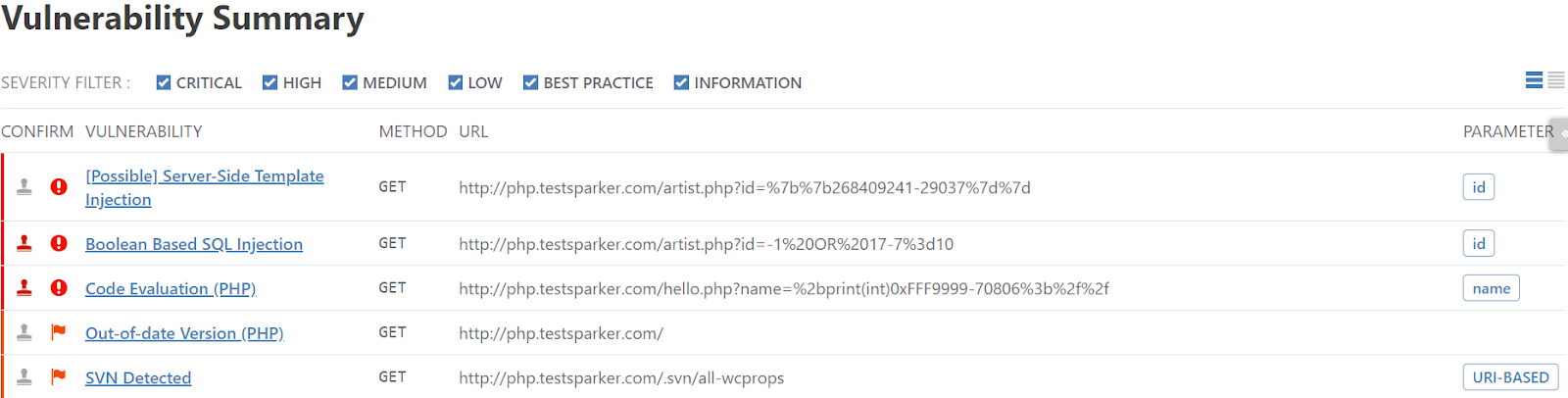
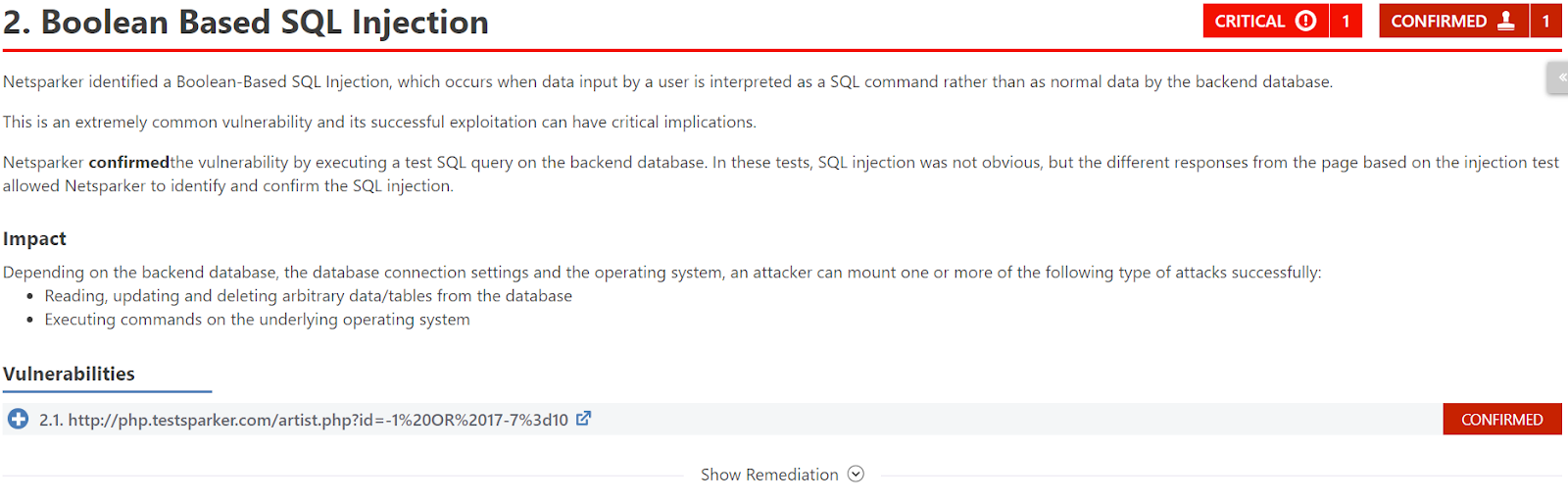
Executive Summary Reports: Concise Overviews for Management
An Executive Summary Report is produced following every web application security scan. It contains numerical and graphical information that presents an overall summary of the target web application’s security status. The format of this report allows less technical users to quickly see how many issues were detected and which need urgent attention. They can also see the business impact of the scan, and therefore prioritize and manage the required remediation work.
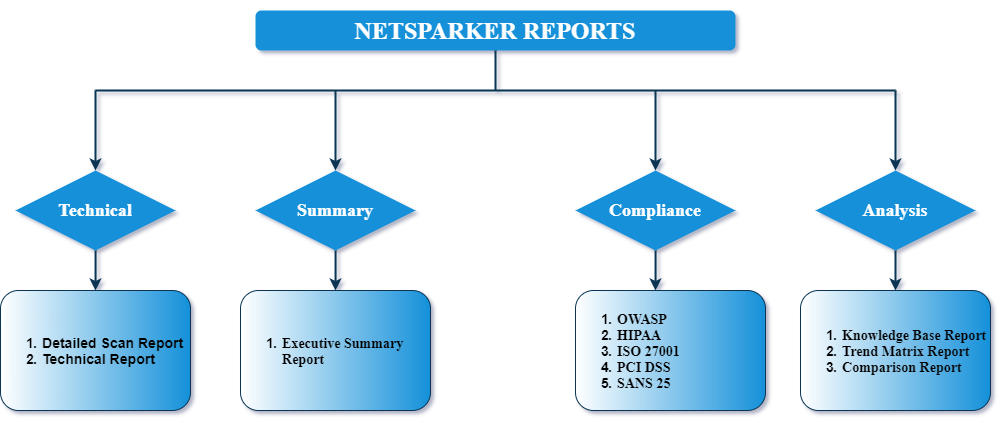
Compliance Reports Classify Vulnerabilities with Precision
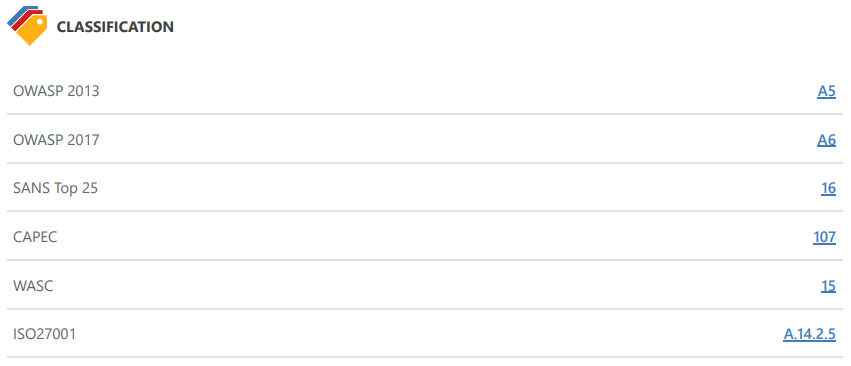
Invicti reports list vulnerabilities based on Vulnerability Severity Levels. If Invicti labels a vulnerability as critical, it lists it at the top. However, if you want to restrict the report to view only vulnerabilities that are based on specific classifications or compliance requirements, such as HIPAA, ISO 27001, OWASP, PCI DSS, and SANS, there is a series of reports among the Report Templates that enable you to do so. If your organisation processes identifiable health information, you are expected to abide by the US Health Insurance Portability and Accountability Act (HIPAA) standards. Here is an example of a HIPAA Compliance Report.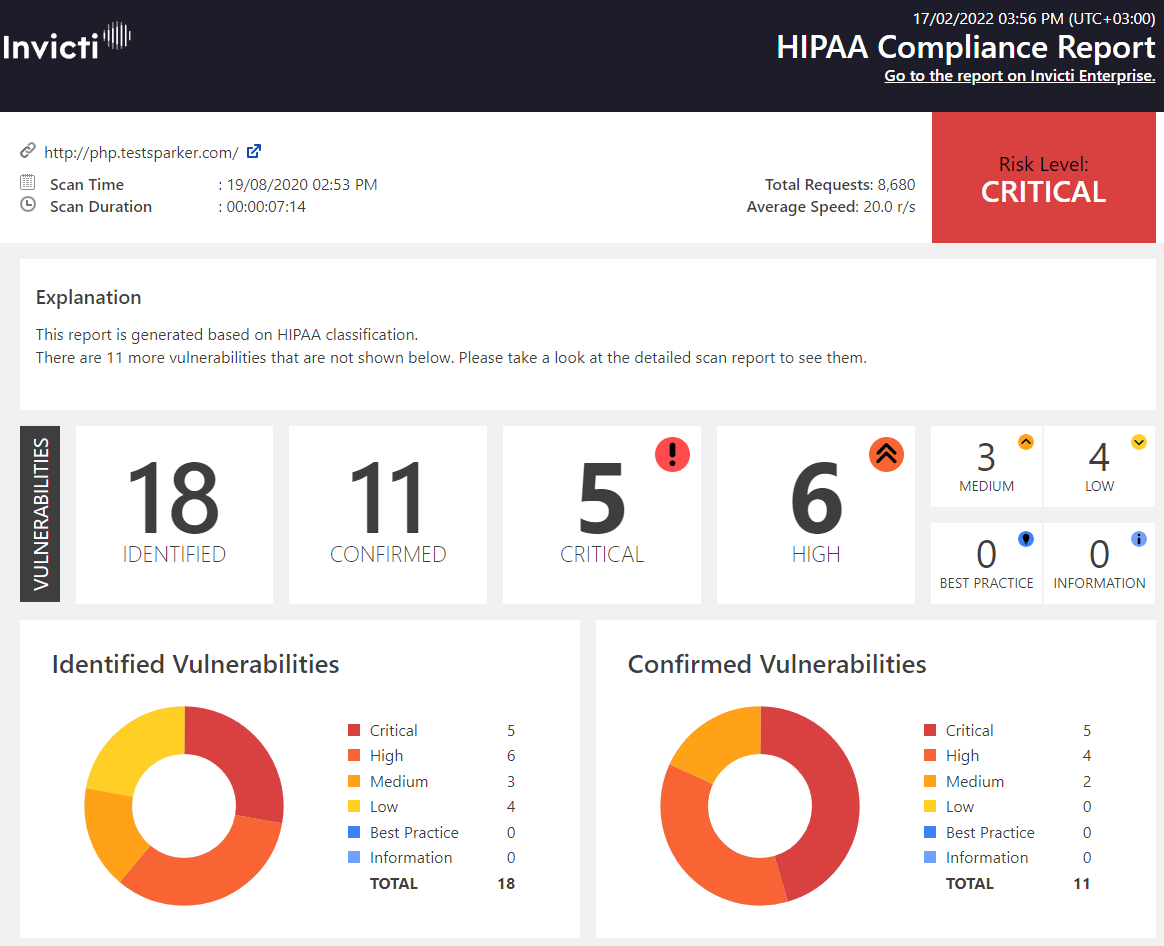
Knowledge Base Reports: Information About Additional Risk Factors
The Knowledge Base Report – unlike the Detailed Scan Report that developers rely on to list all vulnerabilities – lists additional information about the scan via a series of Knowledge Base Nodes. Reported issues include, for example, AJAX/XML HTTP Requests, CSS Files, External Scripts, Google Web Toolkit, Interesting Headers, and Web Pages With Inputs.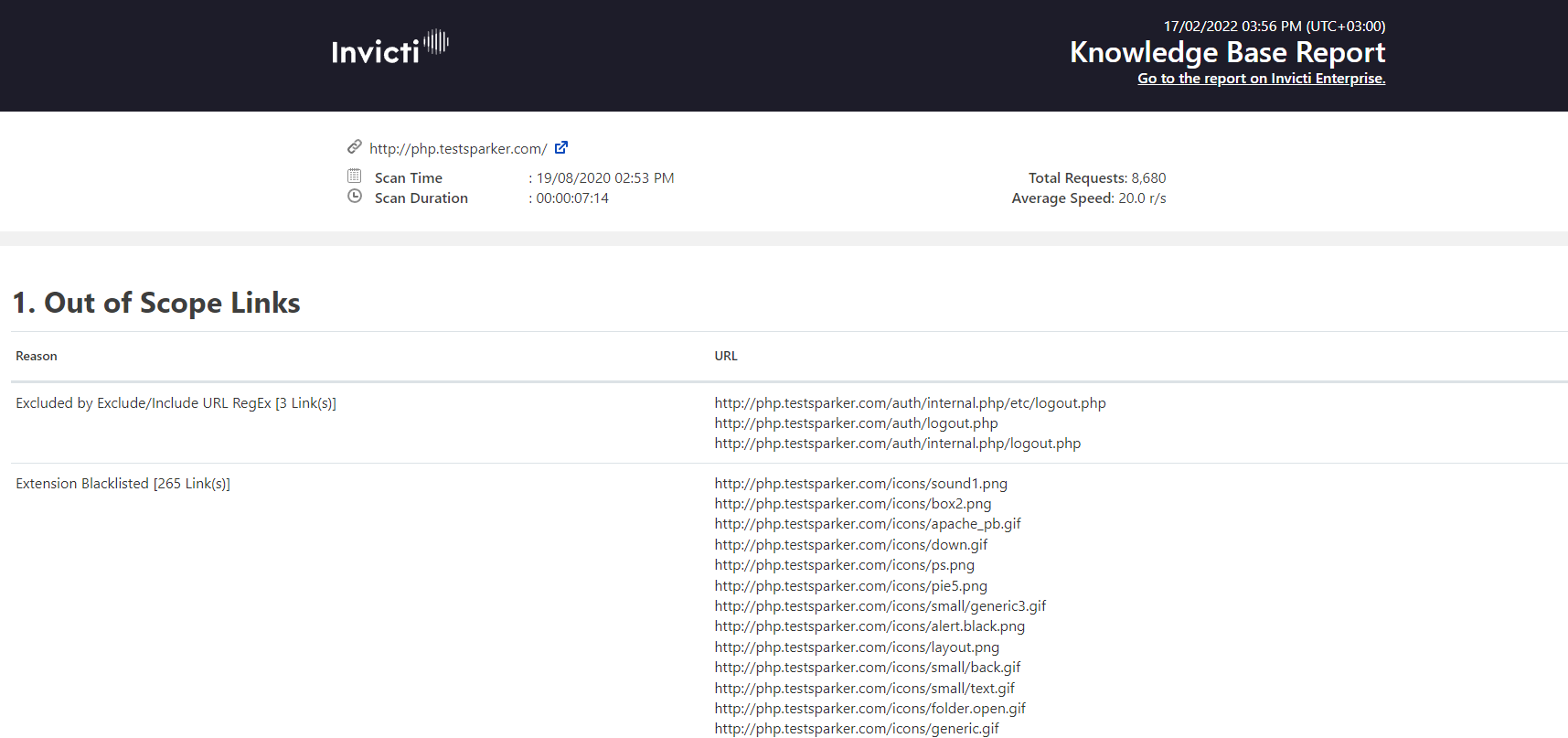
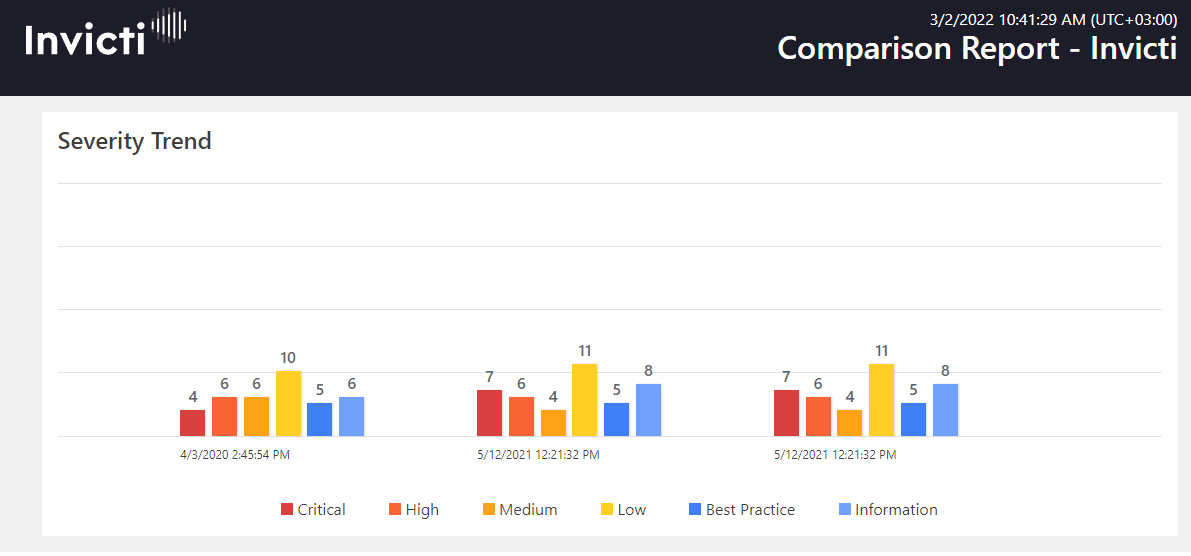
Comparison Reports: Track Your Web Application’s Security Status
The Comparison Report, available in the Invicti Standard edition, can be used to monitor progress in fixing security vulnerabilities. If you run more than one scan on a target web application, you can subsequently use the Comparison Report feature in Invicti Standard to compare results and review progress. (In Invicti Enterprise, the Trend Matrix Report provides access to similar information.) In a quick, accessible format, you can see which vulnerabilities are fixed, new, revived, and not fixed. This report allows you to see the progress made in securing the web application over time.