Scan and secure your SOAP web services with Invicti DAST
Invicti delivers comprehensive and automated dynamic security scanning built for APIs like SOAP web services, helping you uncover real risks and stay compliant.


3600+ Top Organizations Trust Invicti

















Why SOAP web services need security scanning
SOAP still powers mission-critical applications
Despite the rise of REST, gRPC, and GraphQL, SOAP remains deeply embedded in financial services, healthcare, government, and other highly regulated industries. From legacy systems to modern integrations, SOAP APIs continue to transmit sensitive data, and they must be protected.
Common security risks in SOAP APIs
SOAP services are especially vulnerable to:
- XML and SQL injection
- Broken authentication or session management
- Information exposure via WSDL files
- Unencrypted message transmission
- Improper access controls
These vulnerabilities can lead to data breaches, service disruption, or compliance violations if not addressed proactively.
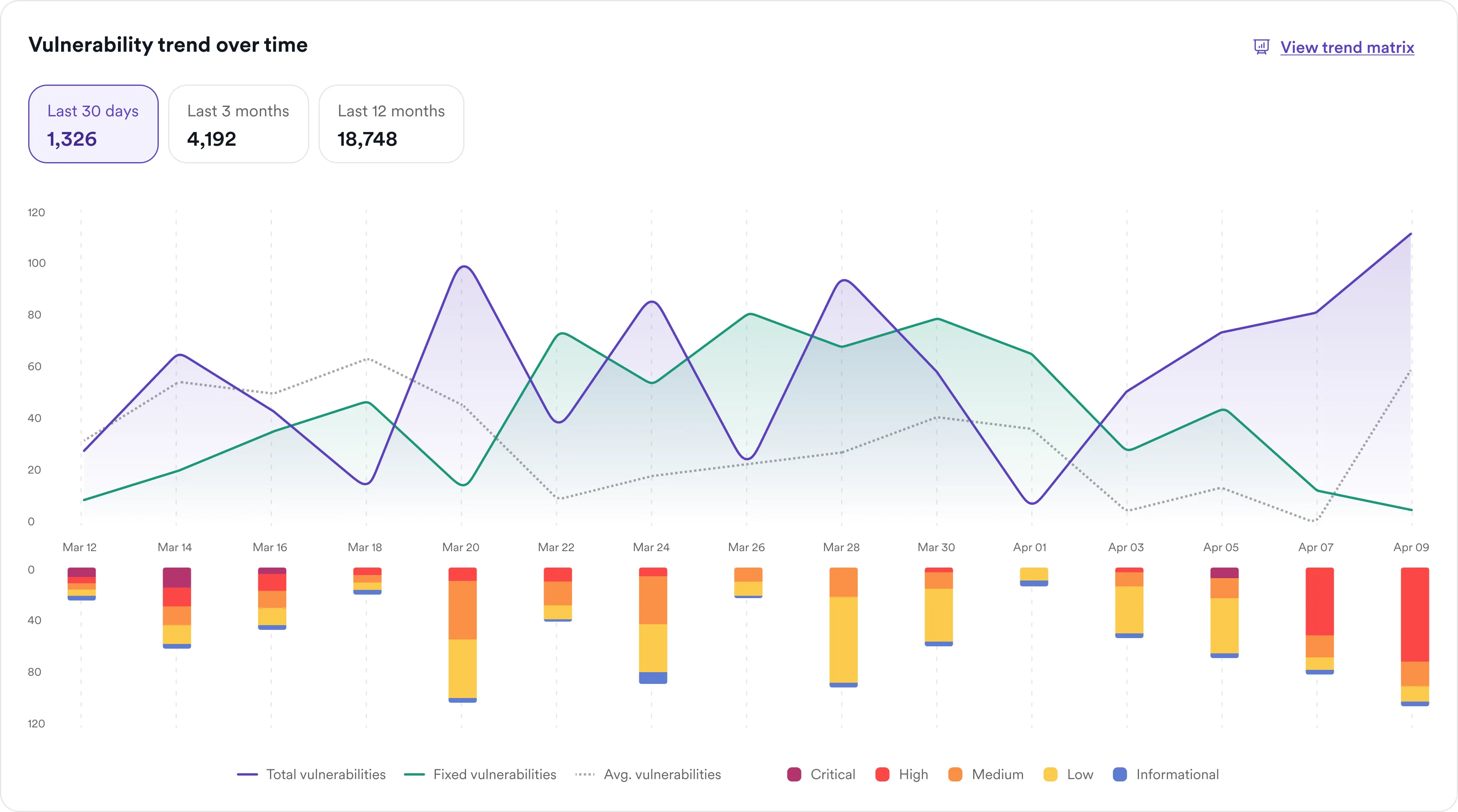
Use cases: Who needs a SOAP scanner?
- Enterprises with legacy SOAP infrastructures: Invicti makes it easy to secure long-running applications without retrofitting them for REST-based tooling.
- Compliance-conscious organizations: Meet the demands of PCI DSS, HIPAA, SOX, and other frameworks by regularly testing SOAP APIs for vulnerabilities.
- Security and DevOps teams with mixed APIs: Use a single solution to test SOAP, REST, GraphQL, and more—reducing tool sprawl and ensuring full API coverage.
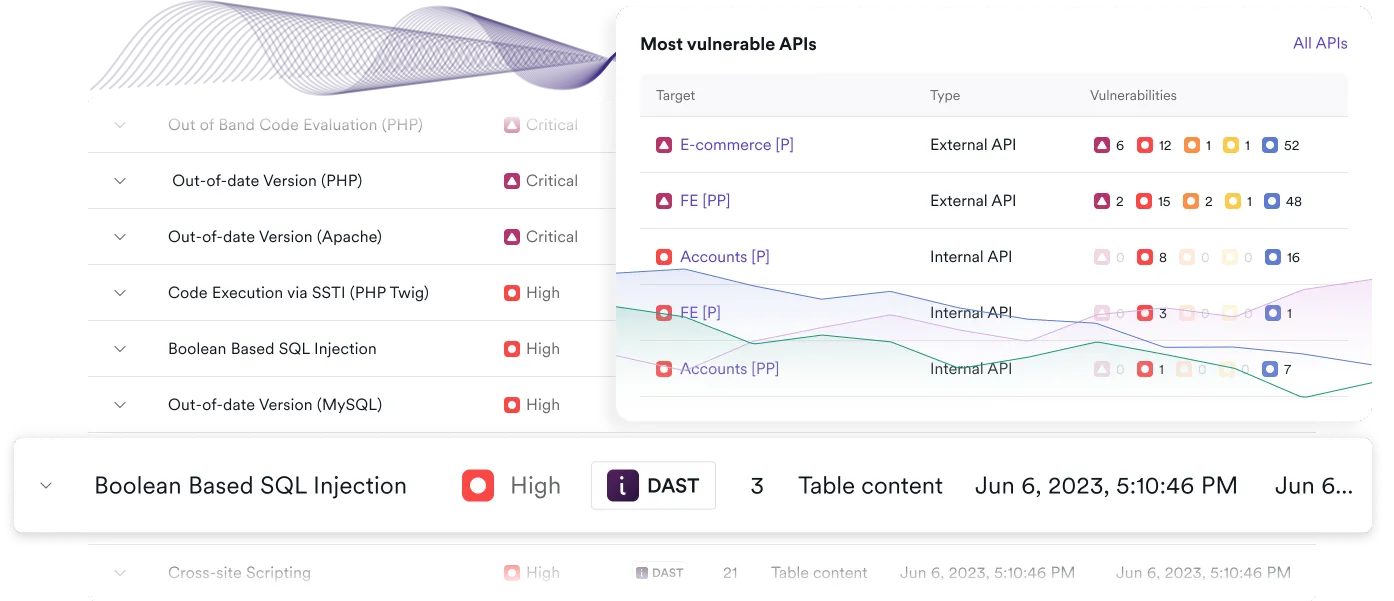
How Invicti stands out for SOAP vulnerability scanning
Unlike more basic vulnerability scanners, Invicti performs SOAP scanning using its proven DAST engine—and unlike point solutions for API security, it also scans your entire application, not just its SOAP APIs. Whether your web services are hosted publicly or behind auth, Invicti brings:
- Robust WSDL interpretation
- Real-time attack simulation
- Customizable testing logic
- Automated coverage, no scripting required
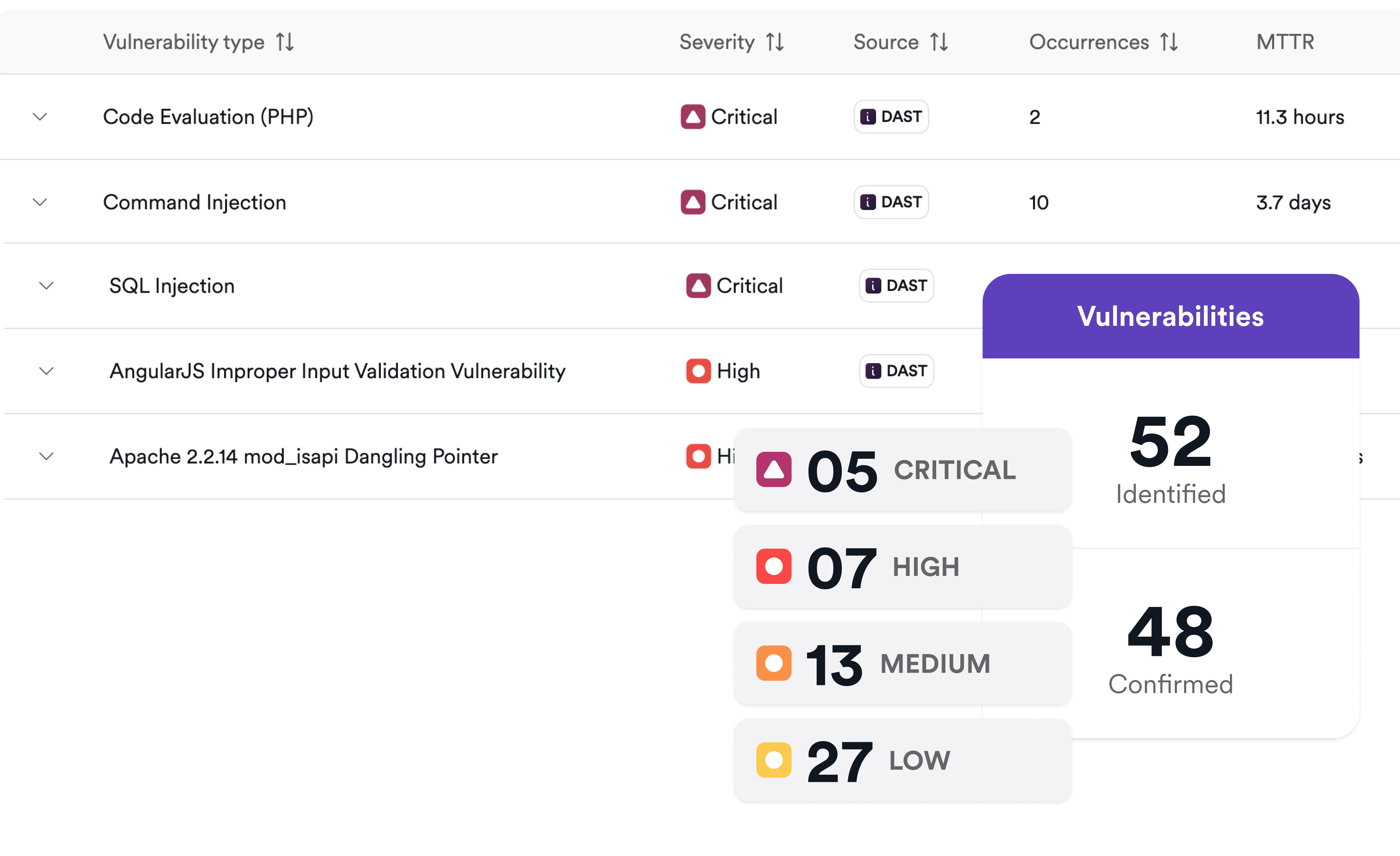
Invicti’s SOAP scanner: DAST for APIs and web services
G2 Awarded
Invicti’s SOAP scanner: DAST for APIs and web services
Invicti intelligently parses WSDL (Web Services Description Language) files to fully understand your SOAP API’s operations, parameters, and message structures with a minimum of manual configuration.
Secure even your protected endpoints. Invicti supports Basic, NTLM, Digest, Bearer Token, and custom authentication mechanisms, preserving session state to test all operations thoroughly.
Our dynamic scanner simulates actual attack scenarios by sending crafted SOAP requests to your endpoints. This allows Invicti to identify vulnerabilities that static analysis tools or basic scanners can’t detect.
Embed SOAP scanning into your development and deployment workflows. Invicti integrates with Jenkins, GitHub Actions, Azure DevOps, and other pipeline tools to ensure every release is secure.
FAQ: SOAP scanner
Yes. Simply provide a WSDL schema file or URL, and Invicti will parse the structure, enabling automated and targeted scanning. Invicti can also automatically add any WSDL schemas it finds while crawling your application.
Absolutely. Invicti supports Basic Auth, NTLM, tokens, and custom header-based authentication.
Yes, SOAP scanning on the Invicti platform supports full DevSecOps integration with popular CI tools and automation pipelines.
Most typical application vulnerabilities can also be detected via SOAP APIs, including injection flaws, authentication issues, insecure communications, access control failures, and more.
SOAP is a standardized protocol that uses structured XML and WSDL contracts, which requires advanced parsing and protocol handling. REST is a looser API architectural style that uses HTTP methods as operations and (usually) JSON as its data format. Invicti provides native parsing and scanning both for strictly defined SOAP schemas and for application-dependent REST specifications.
Save your security team hundreds of hours a year with Invicti’s web vulnerability scanner.









