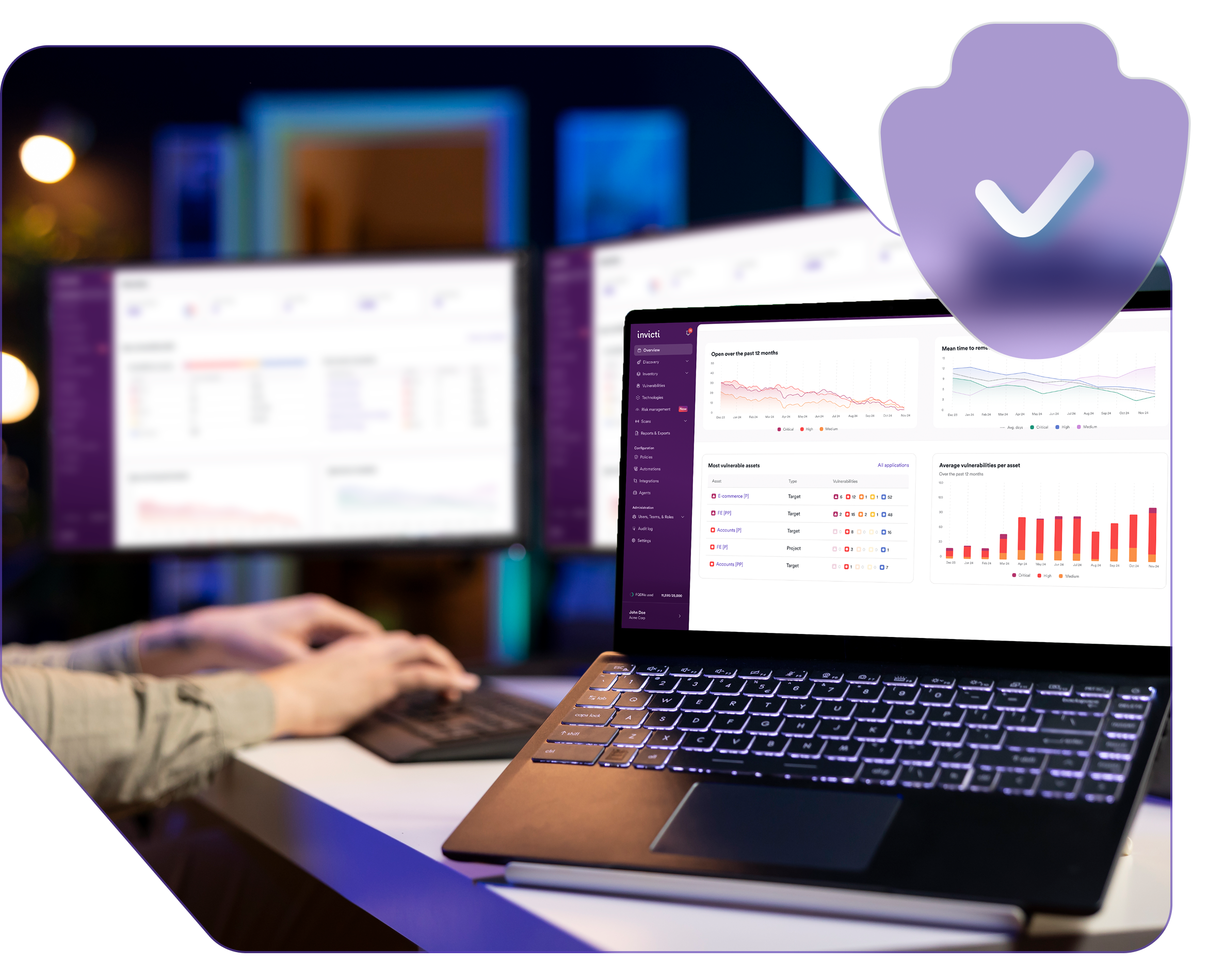
Secure your Magento store with confidence
Invicti scans your live Magento applications to detect and confirm exploitable vulnerabilities across your custom themes, extensions, and APIs.

G2 Awarded
Popular platforms attract persistent threats
Magento powers thousands of e-commerce sites, but its complexity makes it a high-value target. Between custom code, third-party extensions, and evolving integrations, even well-managed stores can harbor hidden vulnerabilities.
Attackers know this. They actively exploit security gaps in Magento plugins, custom themes, and exposed admin endpoints.
Most vulnerability scanners struggle with the dynamic nature of Magento environments. They generate long lists of unverified issues, or worse, miss the risks that matter most.
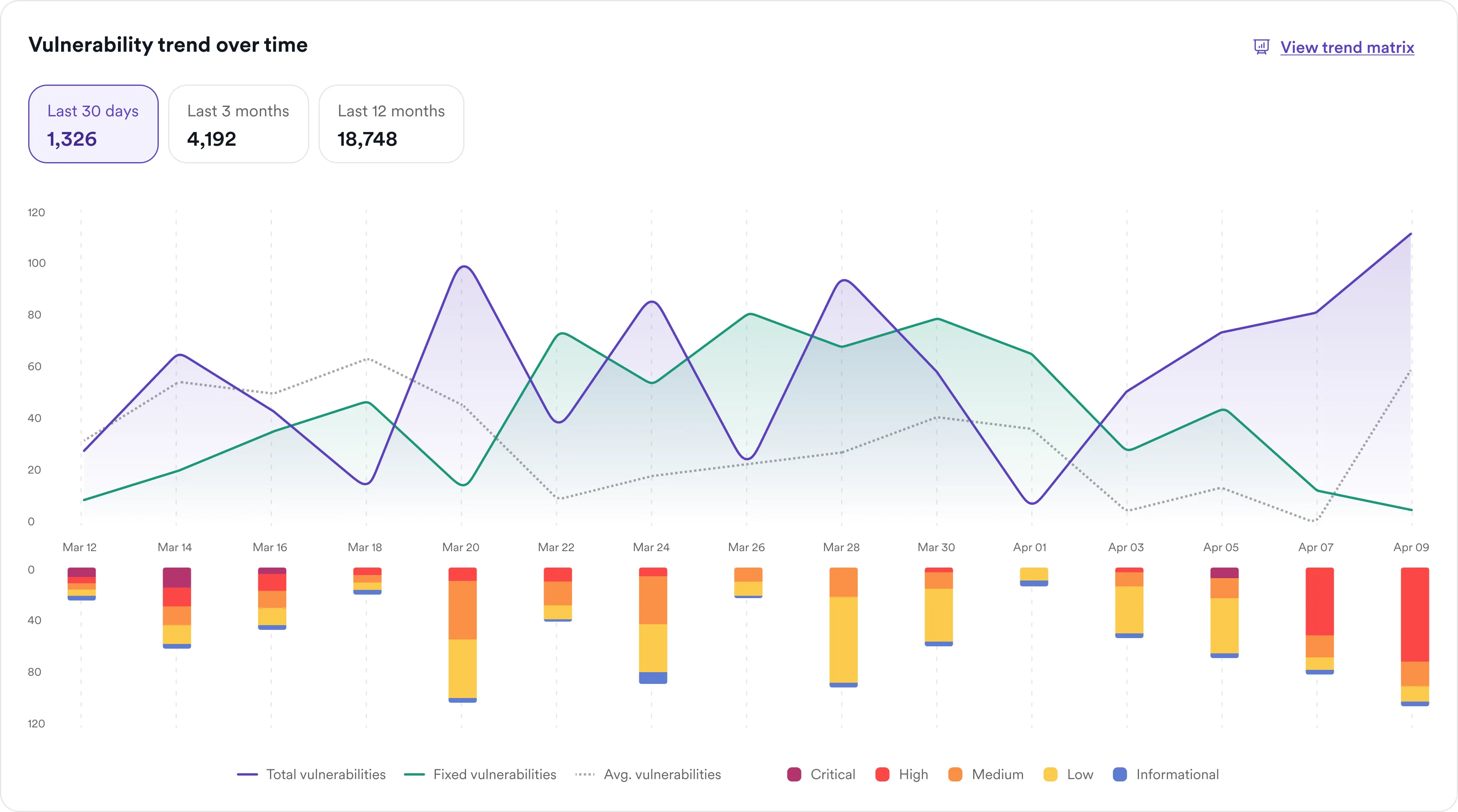
Application-aware scanning built for Magento
Invicti approaches Magento security from an attacker’s point of view. With a DAST-first engine, it scans your live site, just as a threat actor would.
That means full coverage for:
- Known vulnerabilities (CVEs) in core Magento code, plugins, and themes
- New vulnerabilities in customizations and third-party integrations
- API misconfigurations and admin portal exposures
- Entire web environments as deployed, not just isolated code repositories
Every confirmed issue comes with proof of exploitability so you can prioritize real threats and skip the noise.
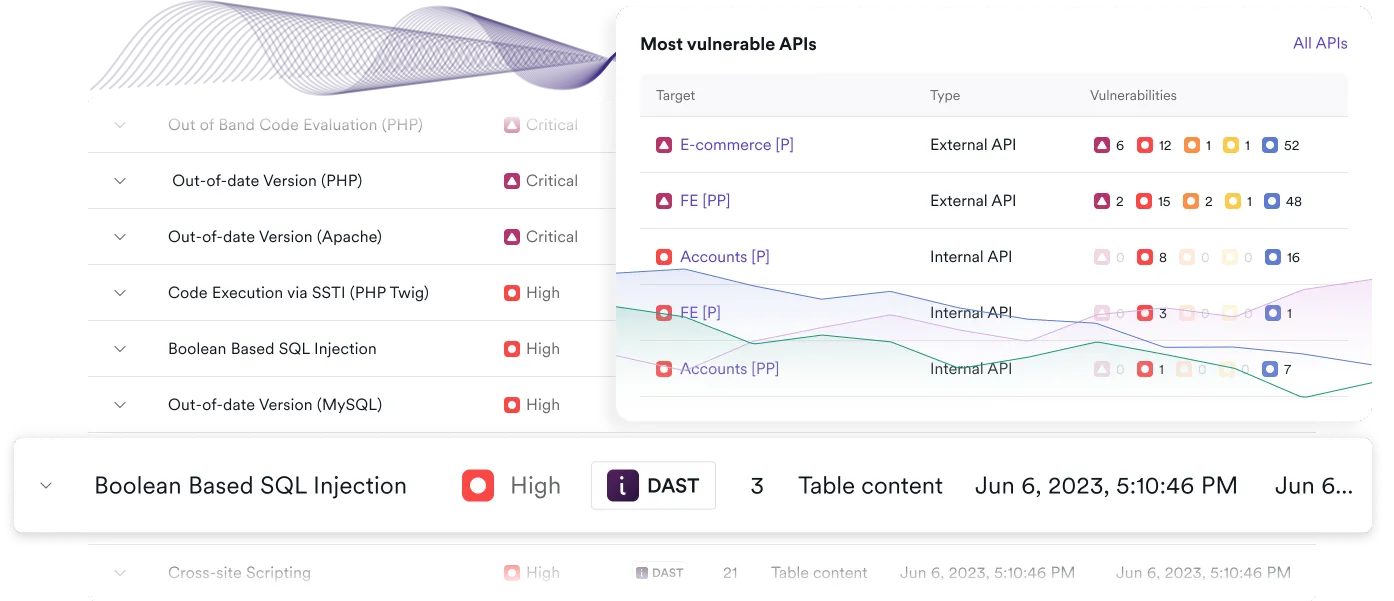
Magento security coverage you can trust
- DAST engine tailored for web apps: Scan Magento storefronts and admin panels using real browser-based crawling for full dynamic coverage.
- Plugin and extension vulnerability detection: Identify insecure third-party plugins and outdated customizations, with coverage for 200+ known Magento CVEs.
- API and backend exposure checks: Find unprotected endpoints, debug panels, and hidden admin paths that attackers can abuse.
- Authenticated scanning: Crawl behind login forms and session-based carts to uncover logic flaws in shopping and checkout flows.
- Proof-based validation: Confirmed vulnerabilities include proof-of-exploit, helping you triage faster and remediate smarter.
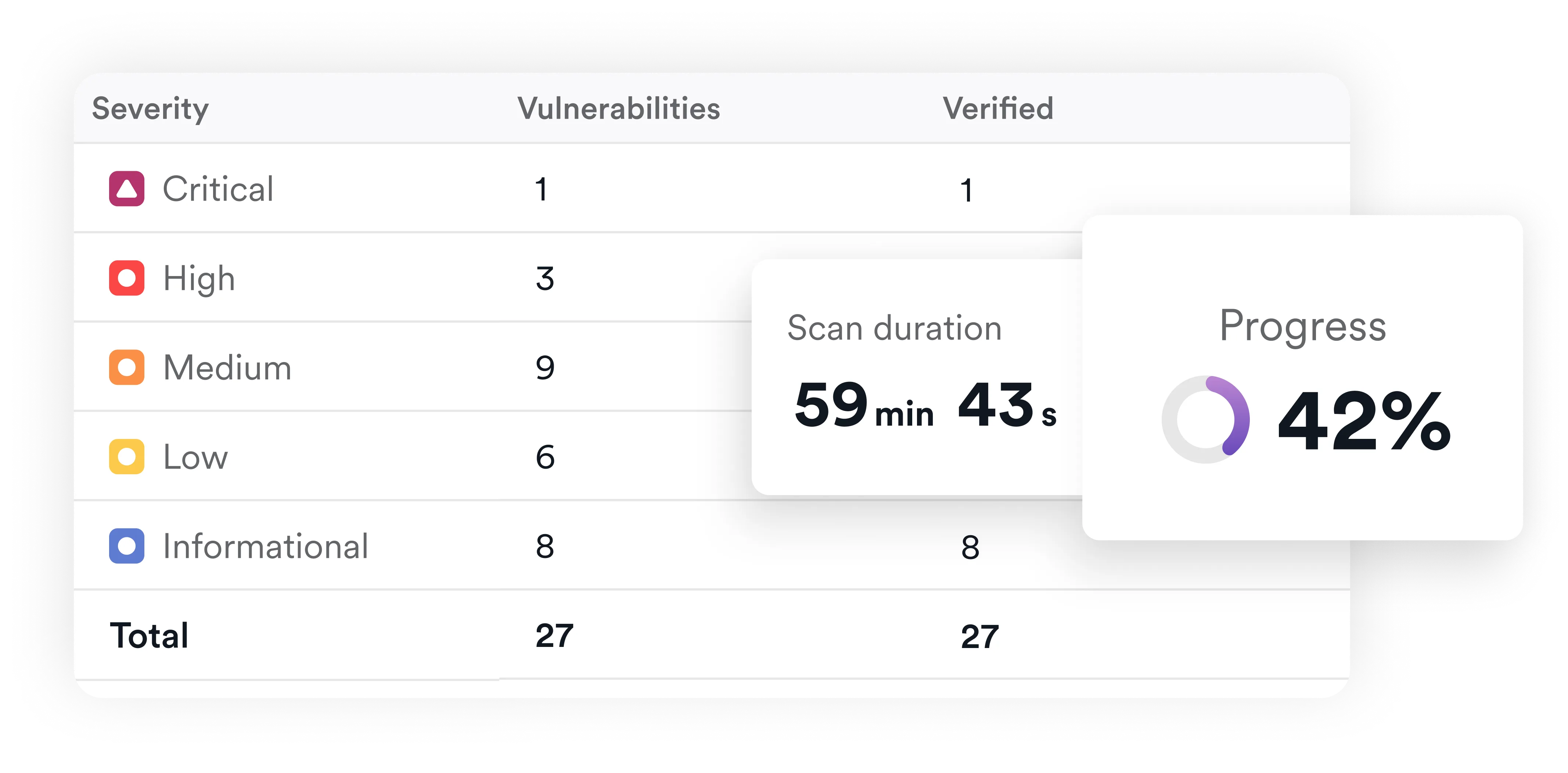
Magento vulnerability scanner FAQ
A Magento vulnerability scanner is a security tool that checks your live Magento store for weaknesses in code, plugins, themes, APIs, and configurations. On top of finding known CVEs, Invicti goes further by running active security checks and then confirming which vulnerabilities are actually exploitable, helping you focus on real threats, not false positives.
Yes. Invicti supports authenticated scanning, which means it can crawl and test behind login forms, user sessions, and dynamic shopping cart or checkout pages—critical for identifying vulnerabilities in customer-facing workflows.
Absolutely. Invicti detects both known vulnerabilities (CVEs) in third-party Magento plugins and insecure custom code or configurations. This includes outdated extensions, improper access controls, and common misconfigurations.
Invicti uses proof-based scanning to safely exploit and confirm vulnerabilities during scanning. Every confirmed issue comes with a proof-of-exploit payload, eliminating guesswork and helping developers prioritize actual risks.
Yes. Invicti supports PCI DSS requirements by offering detailed vulnerability reports, remediation guidance, and audit-friendly reporting. Its automated scanning also helps maintain continuous compliance for e-commerce businesses.
Yes. Invicti integrates into CI/CD pipelines, so you can run scans automatically during development, deployment, or on a set schedule, keeping your Magento store secure without manual overhead.
3600+ Top Organizations Trust Invicti

















Save your security team hundreds of hours with Invicti’s web security scanner.




.png)

