Directory listing

What is a directory listing vulnerability?
Directory listing is a web server function that can cause a vulnerability. When enabled, it displays the contents of a directory that has no index file. This function should always be turned off. It is dangerous to leave it enabled because it leads to information disclosure.
| Severity: |
  |
medium severity |
| Prevalence: |
    |
discovered often |
| Scope: |
    |
may appear in all web servers |
| Technical impact: | information disclosure | |
| Worst-case consequences: | sensitive information breach | |
| Quick fix: | disable directory listing in web server configuration |
How does directory listing work?
To start with an example, when a user types www.invicti.com/learn/ in the browser address bar without specifying a file name in the URL (such as index.html, index.php, index.htm, or default.asp), the web server processes this request, returns the index HTML file for that directory (in this case, the /learn/ directory), and the web browser displays the web page. However, if the index file did not exist and directory listing was enabled, the web server would instead return the contents of a directory, like a file manager.
Why do web server administrators turn directory listing on?
Many web server administrators still follow the concept of security through obscurity. They assume that if there are no public links to files in a directory, nobody can access them. This is not true, and it is especially not true when directory listing is enabled and black hat hackers can easily find all the files in a directory (in fact, even search engines can index such directories). This is why directory listing should never be turned on, especially when hosting dynamic websites and web applications, such as WordPress sites.
Another reason why many web servers have directory listing turned on by default is that many older web server releases came with this feature enabled by default for convenience. This was at a time when web security was less of a concern, and access permissions were lax. Nowadays, most web server distributions, both for Linux and Windows, come with directory listing turned off by default.
Directory browsing without directory listing
Even if directory listing is disabled on a web server, attackers might still discover and exploit web server vulnerabilities that let them perform directory browsing. For example, there was an old Apache Tomcat vulnerability where improper handling of null bytes (%00) and backslash (\) made the server prone to directory listing attacks.
Attackers might also discover directory indexes using cached or historical data contained in online databases. For example, Google’s cache database might contain historical data for a target that previously had directory listing enabled, even if the feature is now disabled. Such data allows an attacker to obtain useful information without having to exploit vulnerabilities.
Example of a directory listing attack
A user makes a website request to www.vulnweb.com/admin/. The response from the server includes the directory content of the directory admin, as seen in the below screenshot.

From the above directory listing, you can see that in the admin directory, there is a sub-directory called backup, which might include enough information for an attacker to craft an attack.
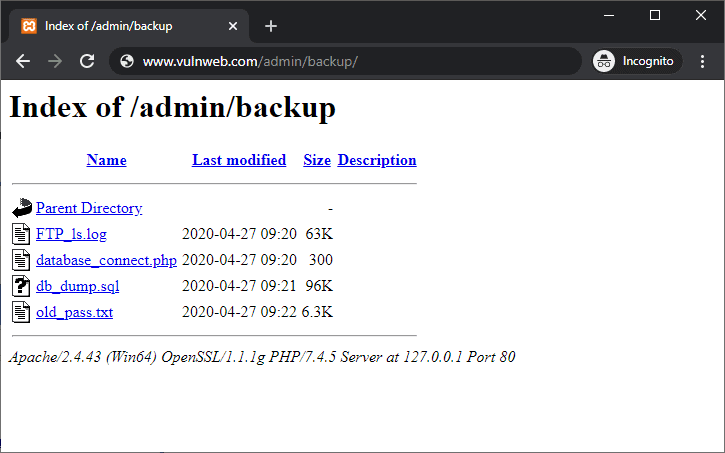
The attacker can display the whole list of files in the backup directory. This directory includes sensitive files such as password files, database files, FTP logs, and PHP scripts. It is obvious that this information was not intended for public viewing.
A web server misconfiguration has caused a file list disclosure and the data is publicly available. Worse still, files like these, such as FTP logs, might contain other sensitive information, potentially including usernames, IP addresses, or the complete directory structure of the web hosting operating system.
How to detect directory listing vulnerabilities?
The best way to detect directory listing vulnerabilities varies depending on whether they are already known or unknown.
- If you only use commercial or open-source software and do not develop software of your own, it may be enough to identify the exact version of the system or application you are using. If the identified version is susceptible to directory listing, you can assume that your software is vulnerable. You can identify the version manually or use a suitable security tool, such as a software composition analysis (SCA) solution for web applications.
- If you develop your own software or want the ability to potentially find previously unknown directory listing vulnerabilities (zero-days) in known applications, you can use a vulnerability scanner tool that can discover web server misconfigurations, including directory listing. Examples of such tools are Invicti and Acunetix by Invicti. We recommend using this method even for known vulnerabilities.
How to mitigate directory listing vulnerabilities?
To disable directory listing and mitigate any vulnerabilities on a specific web server, you need to change the web server configuration. This means you need to have administrator access to that web server.
In the following blog post, you can find practical tutorials on how to disable directory listing for all popular web servers, including Nginx Apache HTTPD, Tomcat, Microsoft IIS, and more: How you can disable directory listing on your web server – and why you should.
Frequently asked questions
What are directory listing vulnerabilities?
Directory listing is not a vulnerability in itself. It is a web server feature that displays the directory contents when there is no index file in a specific website directory. However, leaving this feature active in production leaves your server vulnerable to information disclosure.
See how easy it is to find servers with active directory listing using Google.
How dangerous are directory listing vulnerabilities?
Directory listing may lead to the exposure of very sensitive information, such as backups, database dumps, and more. This information may be directly used against you by malicious hackers, or it may allow for privilege escalation. For example, passwords included in files accessed through directory listing may allow an attacker to follow up with a different attack and ultimately even gain complete control of your systems.
How to avoid directory listing?
To avoid directory listing, you need to manually change the configuration of your web server so it does not display directory content. You can usually do that for all major web servers by using a simple text editor to edit the Nginx conf file, Apache web server .htaccess files, or Tomcat configuration files. For Microsoft IIS, you can turn off directory browsing using the IIS Manager GUI.
Learn how to disable directory listing for all major web servers.
| Classification | ID |
|---|---|
| CAPEC | 127 |
| CWE | 548 |
| WASC | 16 |
| OWASP 2021 | A5 |
Related blog posts
Written by: Tomasz Andrzej Nidecki, reviewed by: Benjamin Daniel Mussler