State of Security for Open Source Web Applications 2018
This blog post examines why open source software has proved so popular, examples of how it can go wrong and why Netsparker tests open source software. It also contains statistical findings on the Netsparker yearly scan of open source web applications for 2017, and an infographic.
Your Information will be kept private.
Begin your DAST-first AppSec journey today.
Request a demo
 Each year, we publish a set of statistics summarizing the vulnerabilities we find in open source web applications. Our tests form part of Netsparker’s quality assurance practices, during which we scan thousands of web applications and websites. This helps us to add to our security checks and continuously improve the scanner’s accuracy.
Each year, we publish a set of statistics summarizing the vulnerabilities we find in open source web applications. Our tests form part of Netsparker’s quality assurance practices, during which we scan thousands of web applications and websites. This helps us to add to our security checks and continuously improve the scanner’s accuracy.
This blog post includes statistics based on security research conducted throughout 2017. But first, we take a look at why we care about open source applications, and the damage that can be caused for enterprises when they go wrong.
Why Do Workplaces Use Open Source Software?
The reason for the rise in popularity of open source software in the business world is financial: your enterprise is getting great software for free. Some enterprises resonate with the open source philosophy of collaboration and giving back. This helps explain why big companies like Twitter, Tumblr, Netflix and Pinterest use and advocate for open source.
Netsparker has a natural interest in the security aspect of open source software, and also a very question; since the source code of open source projects is publically available, does that make these applications more or less secure than proprietary or closed software?
What Happens When Open Source Goes Wrong?
The global average cost of a data breach in 2017 was $3.62 million. In May to July of 2017, Equifax suffered a massive cyber-security breach, with attackers accessing hundreds of millions of customers’ personal data. Although they announced this breach in September 2017, Equifax was informed in 2016 that their website was vulnerable, and was even told which vulnerabilities to check.
Hackers exploiting open source Apache Struts vulnerabilities were blamed for the Equifax breach. Although a deserialization vulnerability in the REST plugin of Apache Struts was initially blamed, an OGNL Expression Injection vulnerability in Struts was found to be the cause for the breach.
Even though a vast amount of personal data was being exposed due to the Equifax breach, a significantly higher number of users were potentially affected by another security bug in readily available open source software. ROBOT (Return Of Bleichenbacher’s Oracle Threat) is a type of attack that revives a 19-year old vulnerability. Bleichenbacher’s RSA vulnerability is still very prevalent in the Internet and affected top domains like Facebook and Paypal, along with many other vendors and open source projects. In December 2017, Netsparker released a hotfix version of our web application security scanner that included ROBOT security checks.
Why Does Netsparker Care About Open Source?
One of the best ways to demonstrate the effectiveness of Netsparker web application security scanner is to test it against a wide variety of web applications used on the web. So our security researchers scan a great variety of open source web applications including: shopping carts and e-commerce solutions, social networking web applications, forums and blogs. The complexity of the testing environment increases when you consider the big number of languages used to create web applications, such as: PHP, Java, Ruby on Rails, ASP.NET, Node.JS, Python and other frameworks.
The only reason – aside from an awesome team of dedicated Security Researchers – that we are able to scan so many web applications and detect so many vulnerabilities across such a wide range, is because automation is at the heart of the Netsparker’s web application security scanning technology.
There are a couple of neat side benefits. Open source applications development teams get free security testing, empowering them to write more secure code. If you’d like to conduct your own, free, automated web application security testing, and read more about how we’re huge supporters of the open source community, see our offer of Free Online Web Security Scans For Open Source Projects.
What Did Netsparker Discover About the State of Open Source Security In 2017?
What Is The Most Prolific Vulnerability in Open Source Applications?
The most predominant vulnerability discovered in open source web applications was Reflected XSS. This accounted for almost 70% of the overall number of reported vulnerabilities. All kinds of Cross-site Scripting (XSS) vulnerabilities ranked as number seven in the OWASP Top 10 List for 2017.
How Many Web Applications Did We Scan in 2017?
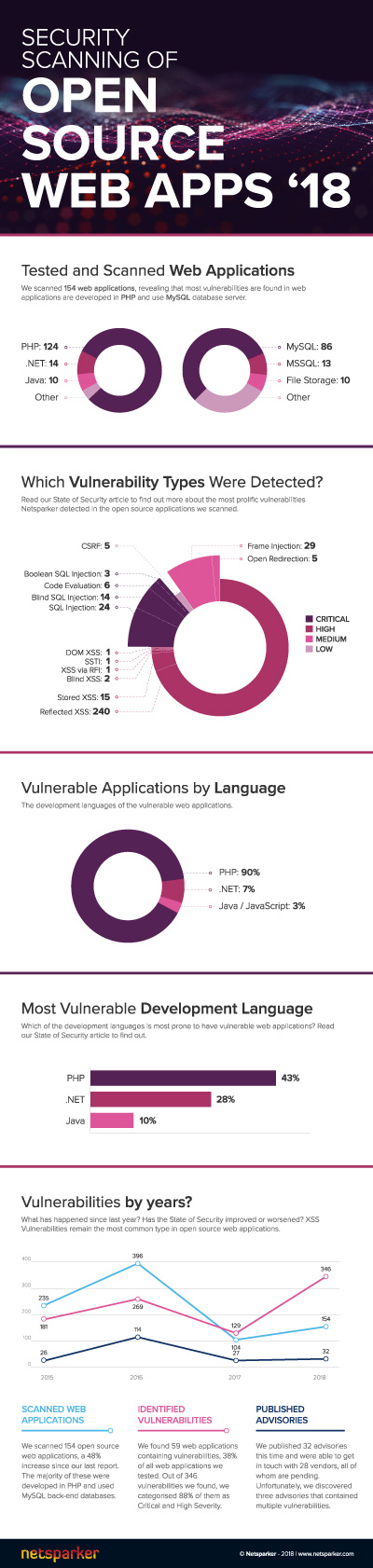
- The total number of web applications we tested and scanned in 2017 was 154, an increase of over 48% from our last report
- The most popular web application frameworks or languages in which scanned apps were developed are PHP (124), .NET (14) and Java (10)
- The most popular back-end database servers used by these scanned applications were MySQL (86), Microsoft SQL Server (13)

What Were the Vulnerability Findings for 2017?
Below are some numbers and statistics about our 2017 findings after scanning 154 open source web applications.
- The number of vulnerable web applications was 59. This is over 38% of all the web applications we tested.
- The total number of vulnerabilities Netsparker identified in these open source sites was 346.
- We scanned 124 PHP web applications, of which 53 were vulnerable. Therefore almost 43% of the PHP web applications we scanned had vulnerabilities in them.
- We scanned 14 .NET web applications and found vulnerabilities in 4 of them. That means that 28% of the scanned web applications built with .NET were vulnerable.
- We scanned 10 Java web applications and only one was vulnerable. That means that 10% of the web applications built with Java were vulnerable.
Which Vulnerability Types Were Detected?
The web application vulnerabilities Netsparker discovered are listed in the table below.
| Vulnerability Name | Total Occurrences | Severity Level |
| Reflected Cross-site Scripting (XSS) | 240 | High Severity |
| Frame Injection | 29 | Medium Severity |
| SQL Injection | 24 | Critical Severity |
| Stored Cross-site Scripting (XSS) | 15 | High Severity |
| Blind SQL Injection | 14 | Critical Severity |
| Code Evaluation | 6 | Critical Severity |
| Cross-Site Request Forgery (CSRF) | 5 | Low Severity |
| Open Redirection | 5 | Medium Severity |
| Boolean SQL Injection | 3 | Critical Severity |
| Blind Cross-site Scripting (XSS) | 2 | High Severity |
| Cross-site Scripting (XSS) via Remote File Inclusion (RFI) | 1 | High Severity |
| Server Side Template Injection (SSTI) | 1 | High Severity |
| Document Object Model Cross-site Scripting (DOM XSS) | 1 | High Severity |
Around 88% of the total vulnerabilities were either of Critical or High Severity. For more information on how Netsparker defines severity levels, see Web Application Vulnerabilities Severities Explained.

Which is the least secure development language?
Based on our findings:
- 43% of the scanned PHP web applications were vulnerable
- 28% of the scanned .NET web applications were vulnerable
- 10% of the scanned Java web applications were vulnerable
Does this mean that PHP is the least secure development language? While many developers and security professionals would agree to such statement, it is not so easy to make such comparison because:
- We scanned much more applications that are built with PHP than with any other language (90% of scanned applications)
- PHP is the most commonly used language for open source web applications
- PHP is the easiest language to learn from all three so it attracts new developers, which are prone to making a lot of mistakes.
How Has the State of Web Application Security Changed Since 2016?
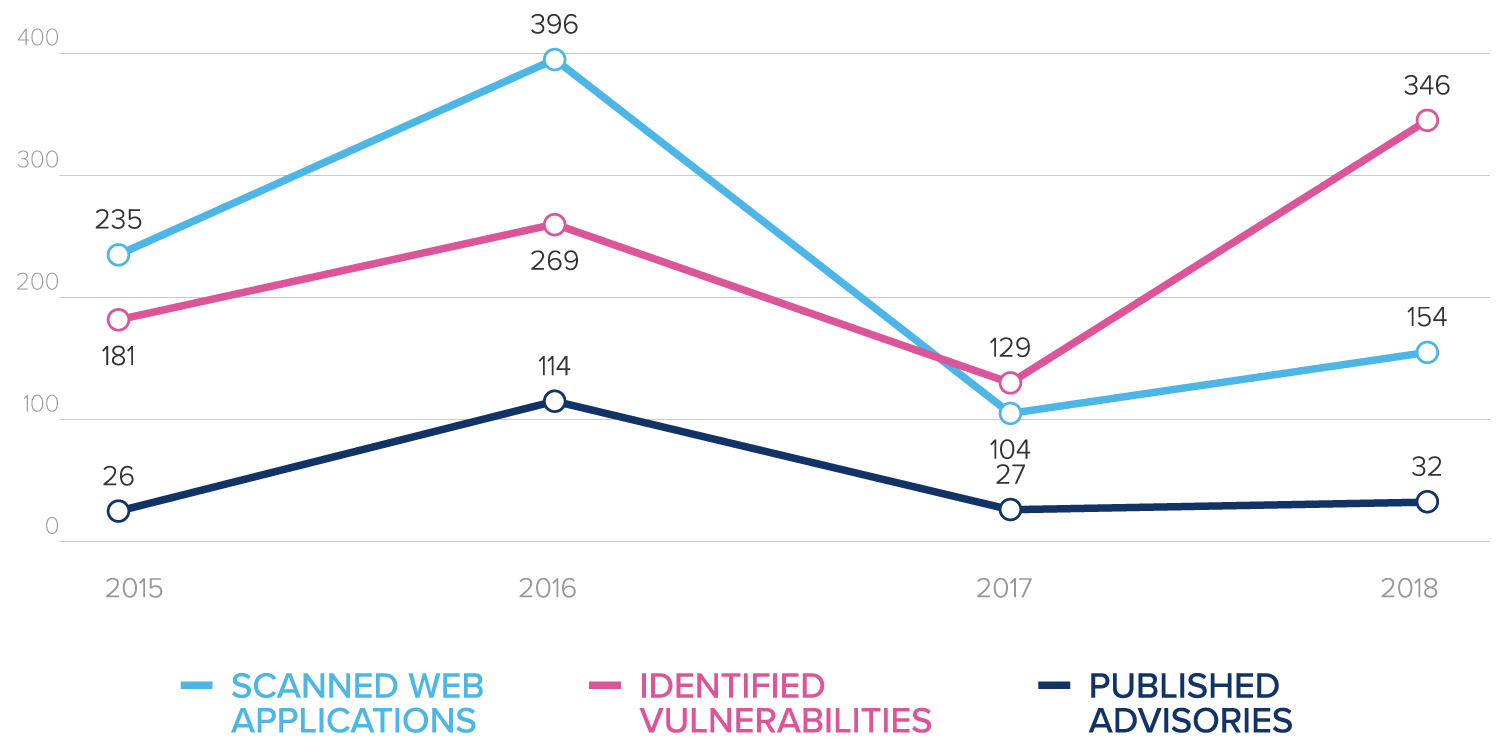
Compared to our findings from last year’s open source testing (see our previous Statistics About the Security State of 104 Open Source Web Applications), it’s clear that XSS vulnerabilities remain, by far, the most common type of vulnerability to be found in open source web applications. The reason for this is that developers who are keen to provide rich interaction in modern web applications use JavaScript in the client-side.
Whereas last year SQL Injection vulnerabilities came in second place, this year Frame Injection vulnerabilities have replaced them. The top development languages, frameworks and database servers remains the same.
What Action Did the Open Source Applications Take?
If you consult our Web Application Advisories by Netsparker list, you can see that we published 32 advisories in 2017. In addition, there are 28 in pending mode. Of these 32, 28 vendors were contacted. Out of the 59 reported web applications with vulnerabilities, only six were fixed. The number of advisories with multiple vulnerabilities was three.
Would Your Open Source Project Benefit From Free Web Vulnerability Scans?
Based on our latest statistics, a randomly-selected web application may include an average of 2.25 vulnerabilities. Developers could eliminate many of these by taking security best practice into account during the SDLC.
Does your team have time to conduct penetration testing to find them all? And, do you know what to do, to remove the vulnerability, and determine whether it is gone? Would you like to have access to an automated web application security scanning solution that would detect them all – and offer remediation recommendations?
Netsparker offers Free Online Web Application Security Scans for Open Source Projects. This is our token of appreciation to all the developers in the open source community and Netsparker’s way of giving back to you. Open source projects such as OpenCart have already used our free, automated web application security scans with great success. Why not you, too?
Useful Resources
Web Application Vulnerabilities Index
Web Application Advisories by Netsparker
State of Open Source Web Applications





