Triggering Netsparker Desktop Scans Remotely With Windows Management Instrumentation
This article explains how to remotely trigger Netsparker Desktop web application security scanner on a Local Area Network (LAN). This enables you to connect to the remote machine via WMI in order to run Netsparker on it.
This article explains how to remotely trigger Netsparker Desktop web application security scanner on a Local Area Network (LAN). This enables you to connect to the remote machine via WMI in order to run Netsparker on it.
- Adding the Netsparker File Path to the Environment Variables
- Triggering Netsparker Web Security Scans Remotely
- Security Best Practice
Adding the Netsparker File Path to the Environment Variables
First, you must add the Netsparker file path to the PATH system variable.
How to Add the Netsparker File Path to the Environment Variables
- In Windows Startup, enter 'environment'.
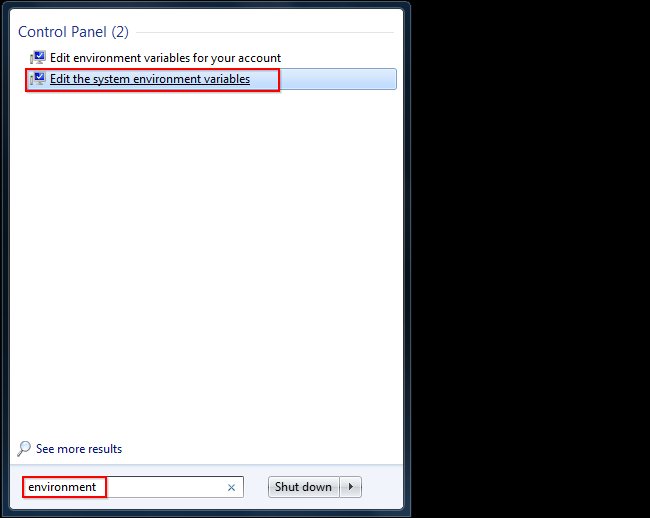
- Click Edit the system environment variables to edit your System PATH variable. The Environment Variables dialog is displayed.
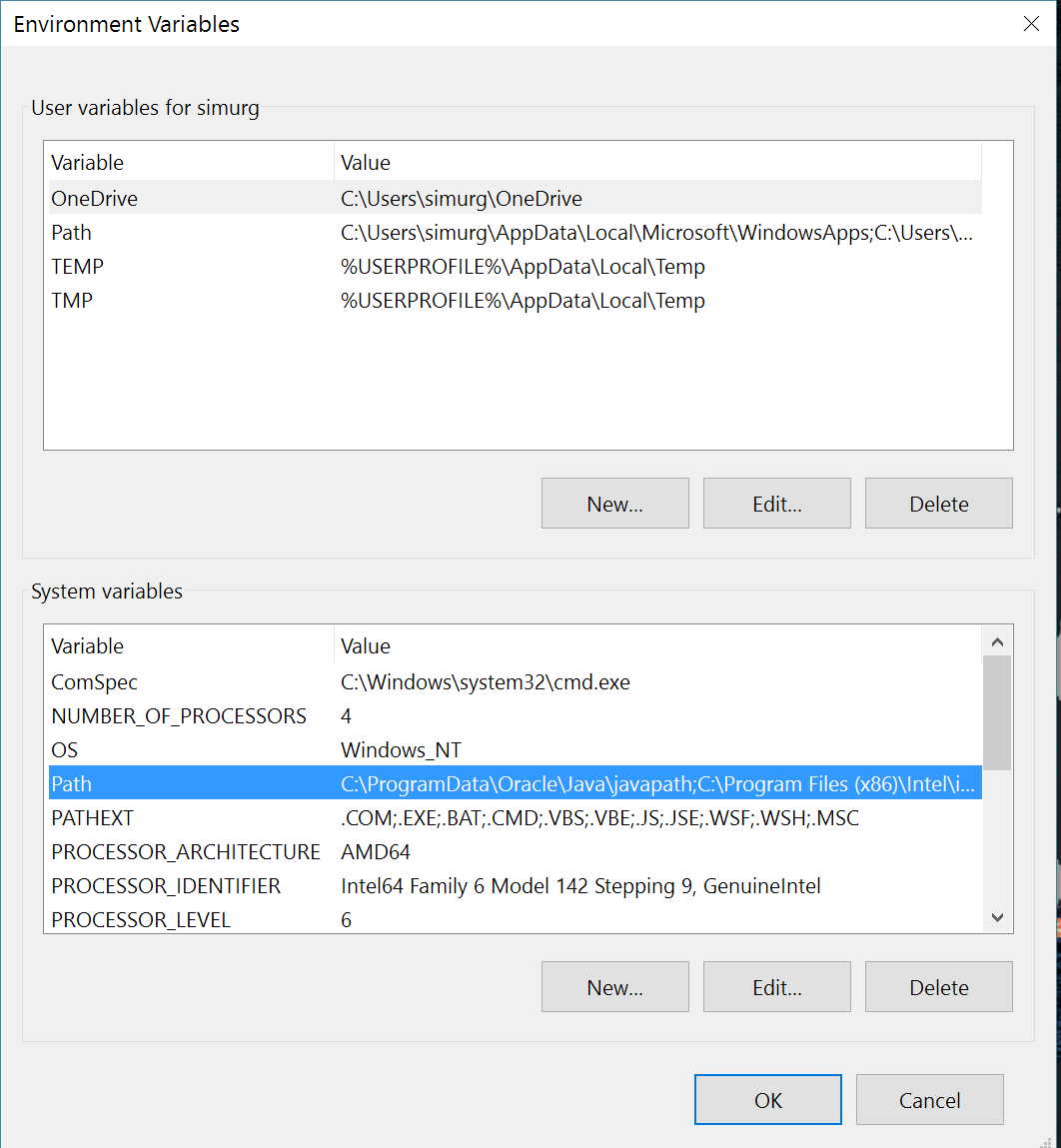
- In the Environment Variables dialog, in the System Variables section, click Path. The Edit environment variable dialog is displayed.
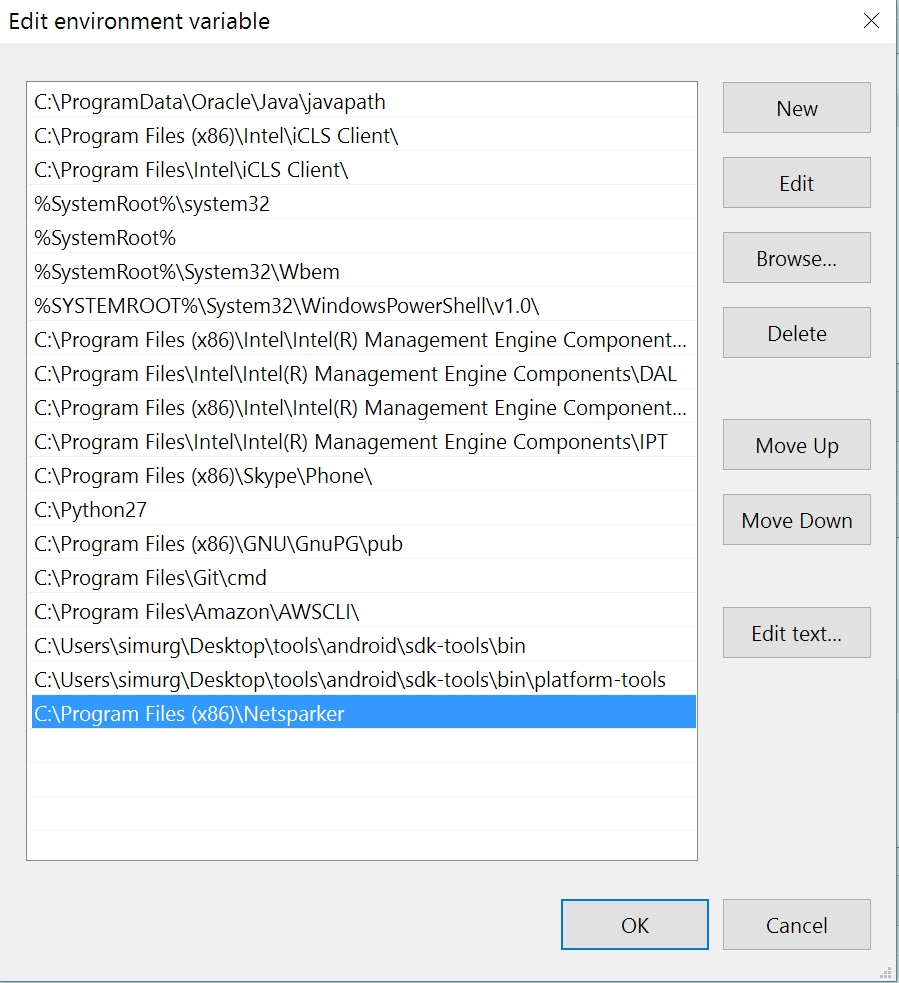
- In the Edit environment variable dialog, click New to add Netsparker’s file path. Enter the file path, and click OK.
Triggering Netsparker Web Security Scans Remotely
There are two ways to trigger web security scans remotely. In these examples, scans are initiated remotely using default settings. If you want to scan a website using non-default configuration, see Netsparker Desktop Command Line Interface and Arguments.
How to Trigger Web Security Scans Remotely (First Method)
These commands run with the authority of the currently logged-in user. They allow Netsparker to run on a remote machine and to scan the target with a default policy via WMI.
- Open PowerShell or CMD and enter this code:
wmic /node:"REMOTE_COMPUTER_NAME or IP Address" process call create 'cmd /c Netsparker /a /url http[s]://TARGET_URL /rt "REPORT TYPE" /r "YOUR_REPORT_FILE_PATH"'
Command Example With User Information
wmic /node:"192.168.244.125" process call create 'cmd /c Netsparker /a /url http://php.testsparker.com /rt "Detailed Scan Report" /r "C:\Users\Sparker\Desktop\report_phptestsparkercom.html"'
How to Trigger Web Security Scans Remotely (Second Method)
These commands run with the authority of a different user. They will run Netsparker on a remote machine in order to scan the target with a default policy via WMI.
You should use a built-in WMI program for triggering the process on a remote machine, as in the First Method. WMI is a built-in program in Windows OS. It is used to create a remote connection in the command line. We use WMI for triggering a command in the remote connection.
- Open PowerShell or CMD and enter this code:
wmic /node:"REMOTE_COMPUTER_NAME or IP Address" /user:YOURDOMAIN\USERNAME /password:"USERPASSWORD" process call create 'cmd /c Netsparker /a /url http[s]://TARGET_URL /rt "REPORT TYPE" /r "YOUR_REPORT_FILE_PATH"'
Command Example With User Information
wmic /node:"192.168.244.125" /user:Net\Sparker /password:"LongLiveTheSparkers!" process call create 'cmd /c Netsparker /a /url http://php.testsparker.com /rt "Detailed Scan Report" /r "C:\Users\Sparker\Desktop\report_phptestsparkercom.html"'
Security Best Practice
You could define a user with fewer privileges on your domain. This makes it easier for you to follow the processes in the network. They can still connect to remote machines using the defined user account, and run scans without defining the username and password in the command (First Method).
The user you will define might have Domain User authority, though you only need to have Admin privileges on the local machine to run web security scans.


