The Wait is Over, Netsparker 3.1 is Here with Full HTML5 Support
Netsparker Version 3.1 is a major version update. With this version of the false positive free web application security scanner Netsparker, users can scan and identify security issues in HTML5 web applications. This new version of Netsparker also includes a number of new security checks for Web 2.0 web applications, can inject JSON and XML HTTP requests, reports much more information about the target web application and much more. Read this post for a complete detailed list of what is new and improved in Netsparker 3.1
Netsparker Version 3.1 New Features and Improvements
Everyone in our team is really happy to announce the release of Netsparker version 3.1. As you will see in these release notes, this new version is jampacked with new features, new functionality and new web application security checks. Most of the new security features are targeted to help penetration testers, web application security experts and developers do a better job in uncovering all type of vulnerabilities in all of the web applications they are securing, including modern Web 2.0 and HTML5 web applications.
This new version of Netsparker is also able to extract much more details about the target web application which if unnoticed could potentially help malicious hackers craft malicious attacks against the web application. Such information will enable Netsparker users to better understand the target web application so they can attack it better themselves and uncover all security issues. Following is the list of what is new and improved in Netsparker version 3.1.
JSON & XML Request Parsing and Injection Support
Netsparker is now able to launch advanced web security checks against web 2.0 applications by identifying, parsing and attacking HTTP request bodies which contain JSON and XML data. If the target web application uses JSON as its payload while performing AJAX requests, Netsparker will intercept that and attack each of the property values. A sample attack below shows that Netsparker performs a Command Injection attack to a parameter value in a JSON payload:
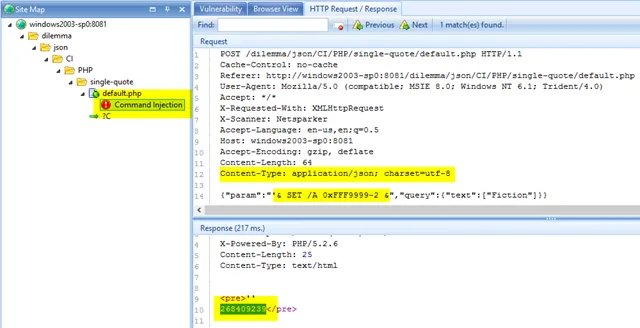
Per Scan Policy Settings
In Netsparker version 3 we introduced Scan Policies, enabling users to specify the type of vulnerabilities a web application should be checked for. In version 3.1 we went a step further by moving most of the global Netsparker settings to the Scan Policy editor. This allows you to create scan policies with different set of settings. For example if a security consultant works with different customers and one of them requires the consultant to connect to a proxy while scanning their websites, the security consultant can create a new Scan Policy specifically for that customer with the required settings and load it up each time he needs to launch a scan, rather than reconfiguring such settings.

HTML5 Support
This new version of Netsparker now fully supports HTML5 web applications. The all new HTML5 engine allows Netsparker to properly crawl HTML5 web applications and identify all attack surfaces that could be susceptible to exploitable vulnerabilities.
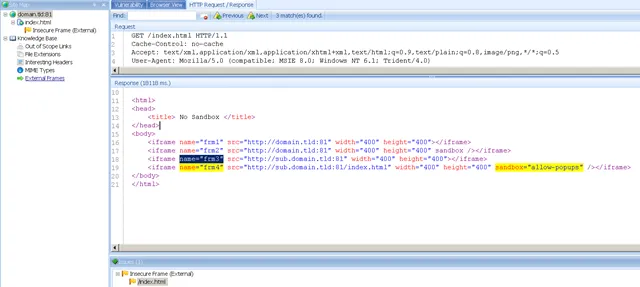
Netsparker also detects improperly sandboxed or insecure inline frames. iframe sandboxing enables a set of extra restrictions for the content in the inline frame. When inline frame is sandboxed, the iframe content is treated as being from a unique origin and sandboxed content is re-hosted in the browser with the following restrictions:
- Plugins are disabled. Any kind of ActiveX, Flash, or Silverlight plugin will not be executed.
- Forms are disabled. The hosted content is not allowed to make forms post back to any target.
- Scripts are disabled. JavaScript is disabled and will not execute.
- Links to other browsing contexts are disabled. An anchor tag targeting different browser levels will not execute.
- Unique origin treatment. All content is treated under a unique origin. The content is not able to traverse the DOM or read cookie information.
When the sandbox attribute is not set or its value contains one or more of the below listed values for an external URL, Netsparker will report it:
- allow-same-origin will not force the unique origin for iframe contents.
- allow-top-navigation will allow iframe to navigate parent context. (e.g. change parent.location).
- allow-forms will allow forms submissions from inside iframe.
- allow-popups will allow popups.
- allow-scripts will allow malicious script execution.
Overall Netsparker will report to you anything that is wrong with the embedded iframe and also recommends several remediations.
New Knowledge Base Items
With the release of Netsparker 3.1 we are also introducing 4 new Knowledge Base nodes where Netsparker will report more findings about the target web application. Such information allows web application security professionals to better understand the web application they are scanning thus helping them do a more complete web application security audit. The 4 new Knowledge Base nodes are;
- Out of Scope Links: This node will list all the links which Netsparker skipped during a scan because of several reasons, such as link is matching one of the specified exclude patterns, link is on another domain and so on. A reason will also be listed for all links explaining why they are out of scan scope. This is also your one stop shop to find answers to your "Why did not Netsparker visit that page?" questions.
- Code Comments: In this node Netsparker will populate a list all the HTML, CSS and JavaScript comments extracted from the target website. should the comments contain sensitive keywords such as password, secret, admin, etc they will be highlighted since they might have been left by mistake and might be exposing sensitive data which could be used by malicious hackers to craft a hacking attack. The list of sensitive keyword matching patterns can be customized from settings per your needs.

- External Frames: This node will contain a list the frames identified on the target website which point to external locations. This piece of information would reveal any malicious frames placed on the target website without the knowledge of the author.
- Embedded Objects: This node will report all the embedded objects found in the target website, such as Flash movies, ActiveX objects, Java Applets, etc.
Automatic Detection of Cross-Site Request Forgery Vulnerability
The new version 3.1 of Netsparker will detect possible Cross-site Request Forgery (CSRF) vulnerabilities automatically during a web application security scan.
CSRF is an attack which forces an end user to execute unwanted actions on a web application in which the user is currently authenticated. With a little help of social engineering, for example by sending a malicious link via email or chat, the attacker may trick the victim into executing actions of the attacker's choosing. A successful CSRF attack can compromise end user data and operation in case of normal user. If the targeted victim is the administrator account, this can compromise the entire web application.
Netsparker is also capable of automatically detect forms which are not vulnerable to CSRF attacks, for example search forms, forms with CAPTCHA etc. This detection mechanism will eliminate false-positive cases.
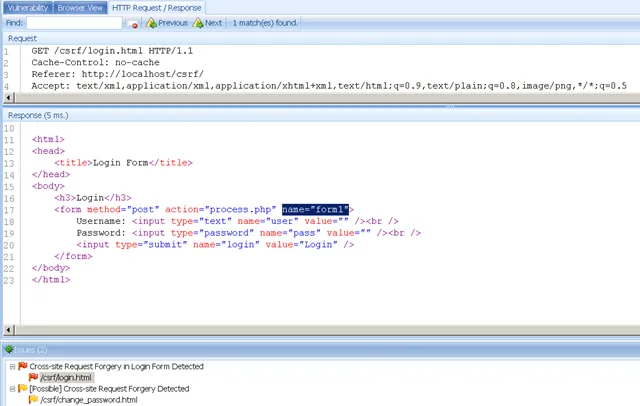
Netsparker differentiates CSRF vulnerability in login forms as a separate issue.
Because the impact of this vulnerability is decreased significantly however it might still be dangerous in certain situations. In this kind of attack, the attacker will send a link containing html as simple as the following in which attacker's username and password is attached.
<form method="POST" action="http://honest.site/login">
<input type="text" name="user" value="h4ck3r" />
<input type="password" name="pass" value="passw0rd" />
</form>
<script>
document.forms[0].submit();
</script>
When the victim clicks the malicious link, the form will be submitted automatically to the legitimate website and exploitation is successful. The victim will be logged in as the attacker and consequences will depend on the website behavior.
Example of CSRF Attack in Search History
Many sites allow their users to opt-in to saving their search history and provide an interface for a user to review the personal saved search history. Search queries may contain sensitive details about the user's interests and activities and could be used by the attacker to craft an attack against the user to steal the user's identity, or to spy on the user. Since the victim logs in as the attacker, the victim's search queries are then stored in the attacker's search history, and the attacker can retrieve the queries by logging into his or her own account.
Example of CSRF Attack in Shopping Websites
Merchant sites allow their customers to save the credit card details in their online profile. In a login CSRF attack, when the user funds a purchase and enrolls the credit card, the credit card details might be added to the attacker's account should the CSRF attack be successful.
Other Notable New Features in Netsparker 3.1
- Added support for parsing cookies which are set by HTML meta tags.
- Ability to generate multiple reports using different templates from a scan result when using the command line interface.
- Vulnerability database updates such as version checks of the latest web application or web server can now be installed without the need to update the Netsparker installation.
- Significant improvements to the JavaScript / AJAX simulation result in faster and more accurate execution of code on pages with lots of HTML elements and JavaScript interaction.
- Scan Summary Dashboard now includes additional information while crawling and attacking pages. For example whether it is doing a HTTP request at the moment or analyzing the response. Attacking activity items now also include the current attack pattern that is being issued along with the scanning engine. The numbers next to engine and pattern names denotes the current and the total number of engines and patterns for this scan. Another enhancement in this area is Re-Crawling and Extra Confirmation phases will also show the current activity on this dashboard.
- In version 3.1 you can configure Netsparker to log all the HTTP requests and responses sent and received during a web security scan. These logs can be exported to Fiddler to further analyse the scan results and to get a better understanding of the web application behaviour.
Improvements in Netsparker 3.1
- Attack possibility calculation is improved
- Rendering in severity bar chart in scan summary dashboard is improved
- Added late confirmation support for Blind Command Injection engine
- DOM parser print dialog prevention improved
- Browser View tab now shows XML responses in a tree view
- Tweaked sleep tolerance value of time based engines
- Improved the impact sections of most of the vulnerability templates
- Improved LFI Exploitation which now is capable of better file content extraction and highlighting on text editor
- Form inputs listed under knowledge base are now grouped by their types
- Improved PHP Source Code Disclosure pattern
- Improved DOM parser to extract textarea elements
- Improved LFI Exploitation to cover case where LFI vulnerable page contains extra HTML tags
- Improved LFI confirmation patterns
- Improved XSS confirmation for Full URL and Full Query String attacks
- Optimized XSS confirmation phase to skip redundant patterns
- Improved binary response detection
- Added limit controls to the knowledge base items to prevent performance degradation of excessive amounts of items
- Default user agent string is set to the one used in IE8
- Improved the importers, manual proxy and Form Authentication Configuration wizard to support JSON, XML and multipart/form-data requests
- Improved multipart/form-data request parsing
- Knowledge base user interface improved
- Improved form value pattern for URL inputs
- Add vulnerability database version information to related vulnerability templates
- Configure Form Authentication wizard clears persistent cookies when started
Bug Fixes in Netsparker
Apart from the above noticeable changes that will definitely allow you to be more productive and detect more vulnerabilities in your modern web applications, Netsparker version 3.1 contains a lot more changes and bug fixes which are listed in the Netsparker Web Application Security Scanner change log.
Download 15 Day Trial of Netsparker
Netsparker makes web application security an easy task! It only takes a couple of minutes to launch a security scan with Netsparker and identify vulnerabilities and security issues in your web applications. Download the 15 Day trial edition of Netsparker today and see for yourself!
Upgrading your Netsparker
If you are already using Netsparker Web Application Security Scanner, a pop up window with the upgrade details will pop up the next time you run Netsparker. Alternatively you can always click on Check for Updates from the Help drop down menu to force manual updates as well.
If you have any queries, get in touch with our awesome support team on support.invicti.com


