The secret to getting results, not noise, from your DAST solution
Products for dynamic application security testing (DAST) vary widely in quality and capabilities. A low-quality tool that merely ticks a box will do little to improve security and may generate more work than it saves. But a mature, high-quality solution can bring measurable security improvements and serve as a solid foundation for your entire AppSec program, as our infographic shows.
Your Information will be kept private.
Begin your DAST-first AppSec journey today.
Request a demo
Scanning is easy – getting good results is not
A generic product pitch for your average DAST tool will tell you that it is an amazing solution because it can run security tests automatically and scale to any number of scans in the cloud. But as any security engineer and penetration tester will tell you, automating security checks is easy – you just write a script that sends your test payloads however many times you need. Spinning up additional workloads on demand is a fundamental feature of cloud environments, so there’s nothing mysterious about scaling scanning, either. The real challenge lies elsewhere. Vulnerability scanners have been around since the mid-2000s, so the basic concepts involved are well known in the industry. The web has changed greatly since then, however, and it is now a very different place in terms of technologies, application usage, and the sheer scale of web development. Instead of a handful of static websites, organizations can have hundreds of dynamic sites, applications, web services, and APIs. The key thing to ask today is not whether a dynamic application security testing product can run automatic tests because they all do that by design. You need to ask if it finds real vulnerabilities and gets actionable results to the right people in time to make a difference – and this is where legacy solutions fall short.Filtering the noise out of vulnerability scanning
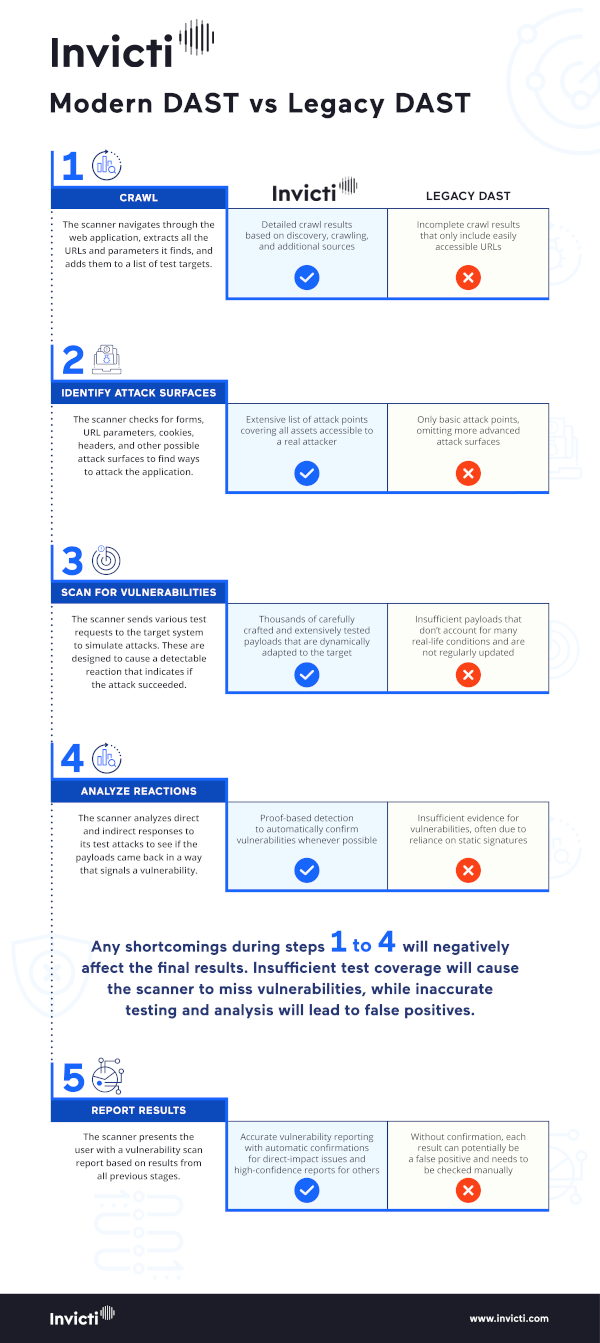
Automation can be a real game-changer, but it is always a double-edged sword – if done badly, what should be a force multiplier merely becomes a work multiplier. Vulnerability scanning consists of multiple stages, and without expert care and attention, every single one can introduce noise that builds up into a flurry of vague signals and false positives. We’ve prepared a detailed infographic to show this, but here are the main steps in a nutshell:- Crawl: Find all the URLs for testing
- Identify attack surfaces: Find all the different places to test for each URL from Step 1
- Attack: Run security checks on surfaces identified in Step 2
- Analyze reactions: Decide which test attacks from Step 3 have uncovered vulnerabilities
- Report results: Present data from Step 4 to the user