March 2020 Update for Invicti Standard 5.7
This blog post announces the March 2020 update for Invicti Standard 5.7. The highlights of this release are form validation errors in the knowledge base, CVSS 3.1 support, and query-based navigation in the Scan Policy Editor. Other new features are three new security checks, hash crawling support and an improved BREACH Attack template.
Your Information will be kept private.
Begin your DAST-first AppSec journey today.
Request a demo
We’re delighted to announce the release of Netsparker Standard 5.7. The highlights of this release are:
- Form Validation Errors in Knowledge Base
- CVSS 3.1 Support
- Query-Based Navigation in the Scan Policy Editor
Form Validation Errors in Knowledge Base
During the scanning process, Netsparker Standard successfully validates web forms as part of the crawling stage. However, due to validation errors, some web forms were unable to be submitted, meaning that they were not displayed in scan reports. With this update, all validation errors that are encountered during the scan will be listed in a new Form Validation Errors node in the Knowledge Base section of scan reports.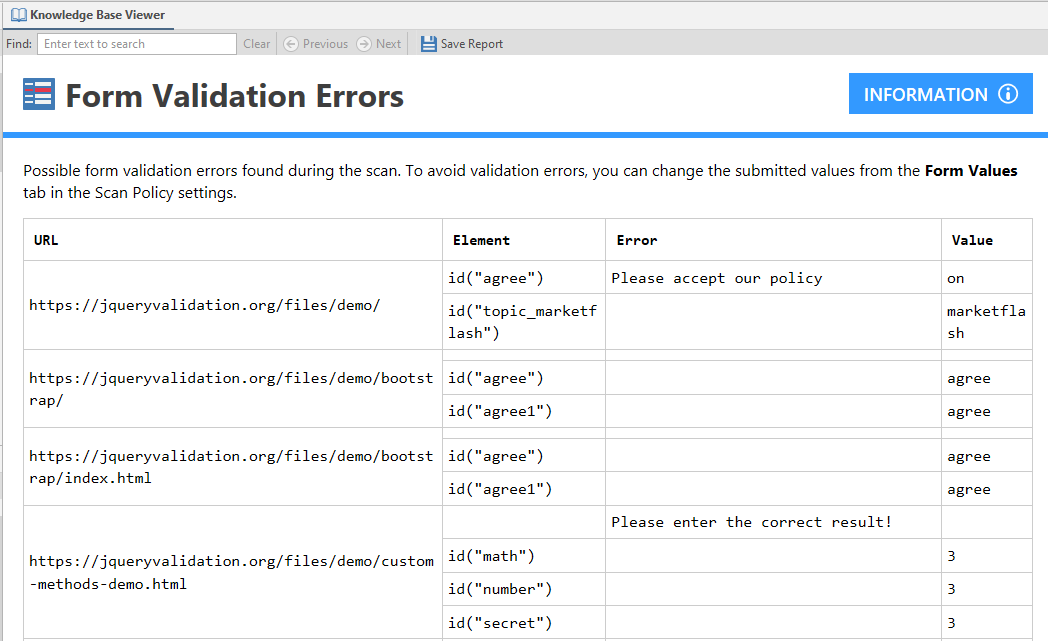
CVSS 3.1 Support
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing security staff managing detected issues to prioritize responses and resources according to the potential threat. We have added version 3.1 scores to vulnerabilities reported by Netsparker.

For further information, see Vulnerability.
Query-Based Navigation in Scan Policy Editor
We have added a new Enable Query-based Navigation checkbox to the Crawling tab of the Scan Policy Editor for Query-parameters only. Parameters used for navigation can be Query parameters in GET requests or POST parameters in the body of POST requests. This new option captures the navigation in Query parameters only; parameters in POST requests are not considered navigation parameters during scans. This option is disabled by default.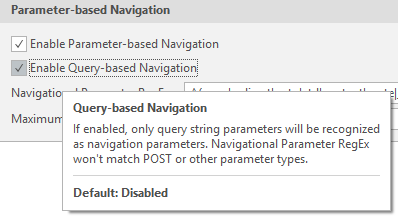
New Security Checks
We have added three new security checks:- Login Page Identified
- Content Delivery Networks
- Reverse Proxies
Login Page Identified
This security check will report Information level vulnerabilities where a web page containing a login form is encountered during a scan. This allows organisations with lots of websites to determine which of them require Form Authentication configuration.
Content Delivery Networks (CDN)
These new security checks are passive checks that have been added into the Signatures security check group. They detect whether the scanned website is using any known CDN services to speed up the loading of source files or images.
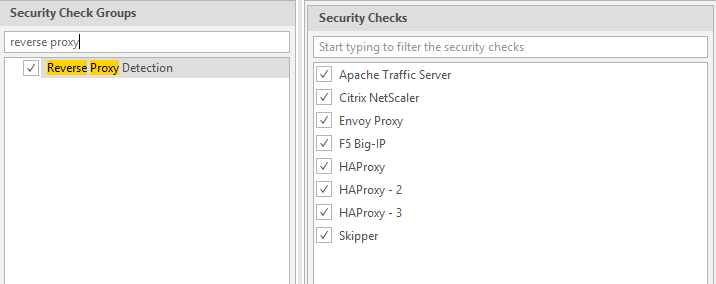
Reverse Proxy Detection
This new security check detects where any reverse proxies are being used in the scanned website.They are reported as Information level vulnerabilities.