PCI ASV scanner to simplify PCI DSS compliance
Ensure fast and confident PCI DSS compliance on Invicti’s DAST-first AppSec platform with integrated PCI ASV scanning services.

G2 Awarded
Simplify PCI DSS compliance with approved scanning vendor support
Meeting PCI compliance requirements is critical for safeguarding cardholder data and protecting against data breaches. As one prerequisite to achieve this, organizations must regularly perform external scanning and provide documented proof to their acquiring bank and other stakeholders. Invicti supports this need by seamlessly integrating its DAST-first AppSec platform with official PCI ASV scan services provided by Clone Systems – a PCI-approved scanning vendor that uses Invicti vulnerability scanning as part of its audit process:
- Scans align with PCI DSS v4.0 requirement 11.3.2 for quarterly external vulnerability scans (11.2.2 in earlier versions)
- Get validated PCI scan results with minimal manual effort
- Access comprehensive PCI DSS compliance reports, including all necessary scan details
- Combine Invicti’s DAST with approved scanning vendor services to simplify the PCI scanning process
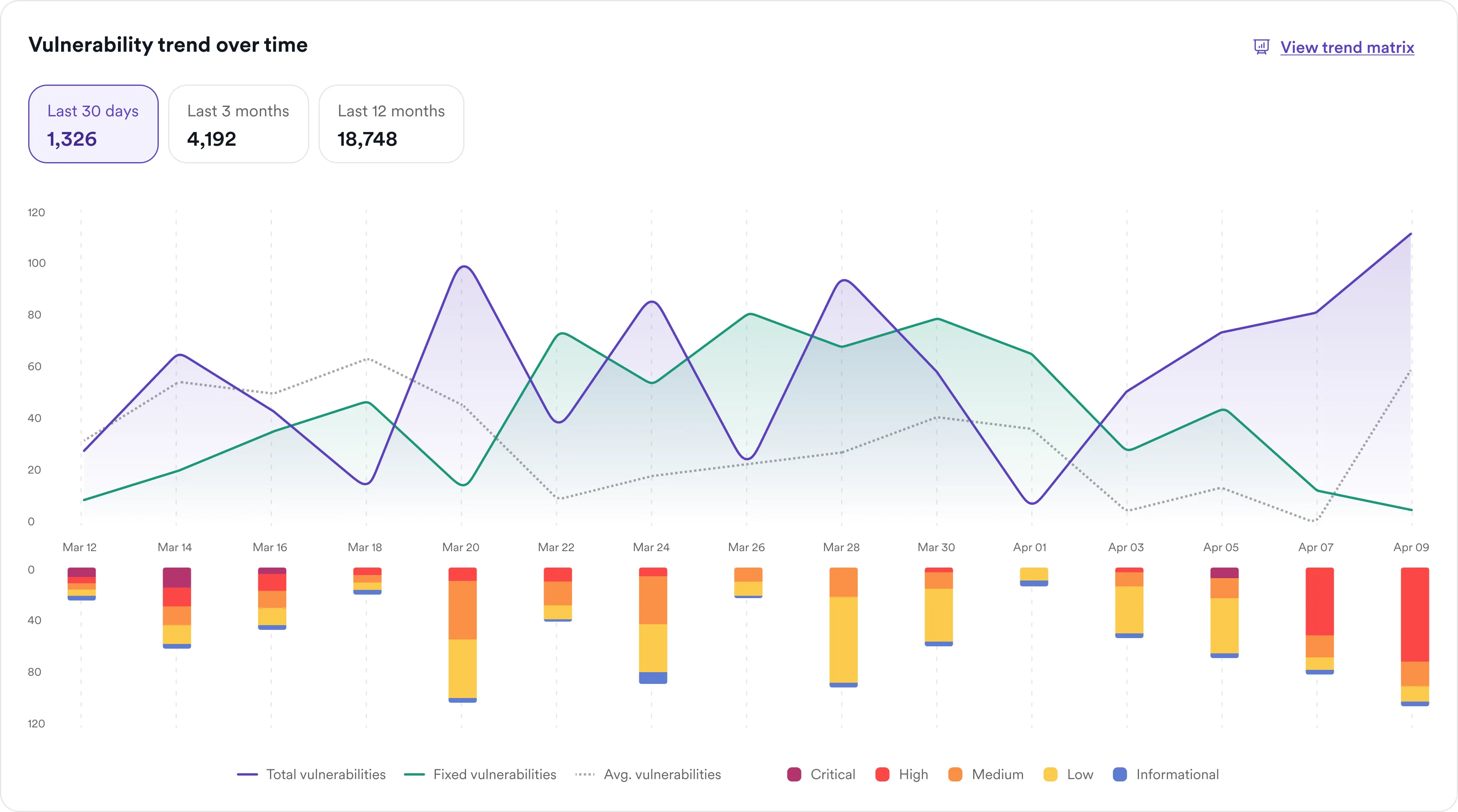
Improve accuracy and cut down on false positives
Accurate vulnerability detection is essential to ensure that real security vulnerabilities are addressed while avoiding unnecessary remediation efforts. Using subpar scanning tools while preparing for PCI DSS (Payment Card Industry Data Security Standard) certification can generate false positives and miss real vulnerabilities, creating inefficiencies and leaving you with more to fix during certification. While final validation for compliance is still performed by the ASV (as per PCI DSS rules), Invicti’s proof-based scanning technology validates many exploitable issues, streamlining the compliance process and helping teams focus on real risks that could expose application environments to attacks:
- Automatically confirm vulnerabilities to cut down on unnecessary manual validation
- Receive high-confidence scan results that directly support rapid validation by the ASV
- Reduce rescans and delays with precise, actionable findings
- Streamline vulnerability management to maintain PCI DSS compliance year-round
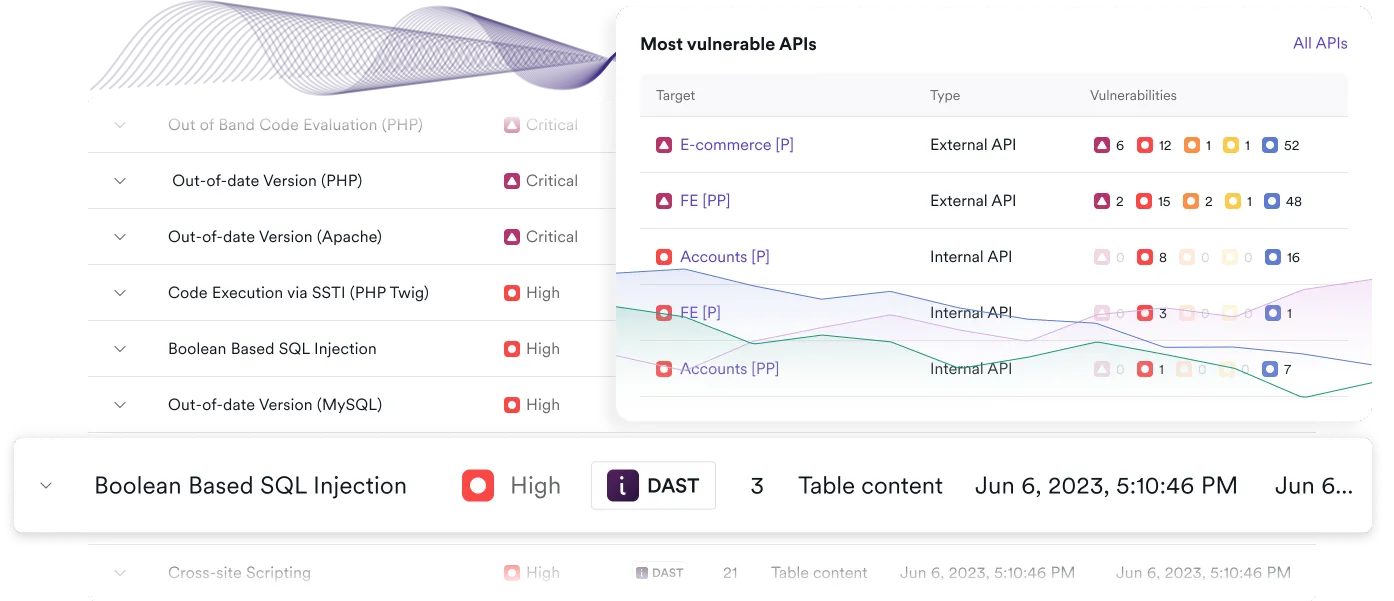
Save time on compliance with automation and flexible reporting
PCI DSS compliance is not a one-time task – it requires ongoing effort to continuously test, validate, and report on security vulnerabilities in internet-facing systems. Invicti automates key processes, making it easier to embed PCI ASV scan requirements into regular vulnerability management and cybersecurity operations. By integrating scanning services and detailed reporting, organizations can stay ahead of compliance requirements and protect against data breaches involving credit card data.
- Schedule and automate PCI scans across web-facing assets
- Get official and unofficial PCI DSS compliance reports formatted for both internal teams and your qualified security assessor (QSA)
- Use detailed remediation guidance to quickly resolve findings and prepare for the next scan cycle
- Track compliance status easily within your vulnerability management processes
An approved scanning vendor (ASV) is an organization certified by the PCI Security Standards Council (PCI SSC) to conduct external vulnerability scanning for PCI DSS compliance.
An ASV scan is an external vulnerability scan performed by a PCI SSC-certified approved scanning vendor to identify security vulnerabilities in internet-facing systems, required at least quarterly by PCI DSS.
Web vulnerability scanners such as Invicti are used to test websites, web applications, and API endpoints for vulnerabilities that malicious users could exploit using a web browser or another tool communicating over HTTP. Network scanners such as nmap are a different class of tools, used to probe networks for open ports to find vulnerable services and systems. A network vulnerability scanner is not designed to detect application vulnerabilities such as cross-site scripting (XSS) or SQL injection.
Learn about the differences between application security and network security
3600+ Top Organizations Trust Invicti

















Save your security team hundreds of hours with Invicti’s web security scanner.




.png)
