GraphQL security scanner: Securing modern APIs with Invicti
Scan your GraphQL APIs for exploitable vulnerabilities as part of your wider application attack surface.

G2 Awarded
What is a GraphQL scanner?
A GraphQL scanner is a security testing tool designed to analyze GraphQL APIs for vulnerabilities. Compared to REST APIs with their multiple operation-specific endpoints, GraphQL provides a single endpoint that supports rich, nested queries. This means traditional API security scanners often fall short because they’re not schema-aware and can’t interact with the unique structure of GraphQL requests.
An effective GraphQL scanner must not only recognize GraphQL traffic but also understand the schema, validate inputs, and simulate real attack scenarios to identify exploitable weaknesses. And because APIs don’t exist in a vacuum, they should be scanned as an integral part of the overall application attack surface.
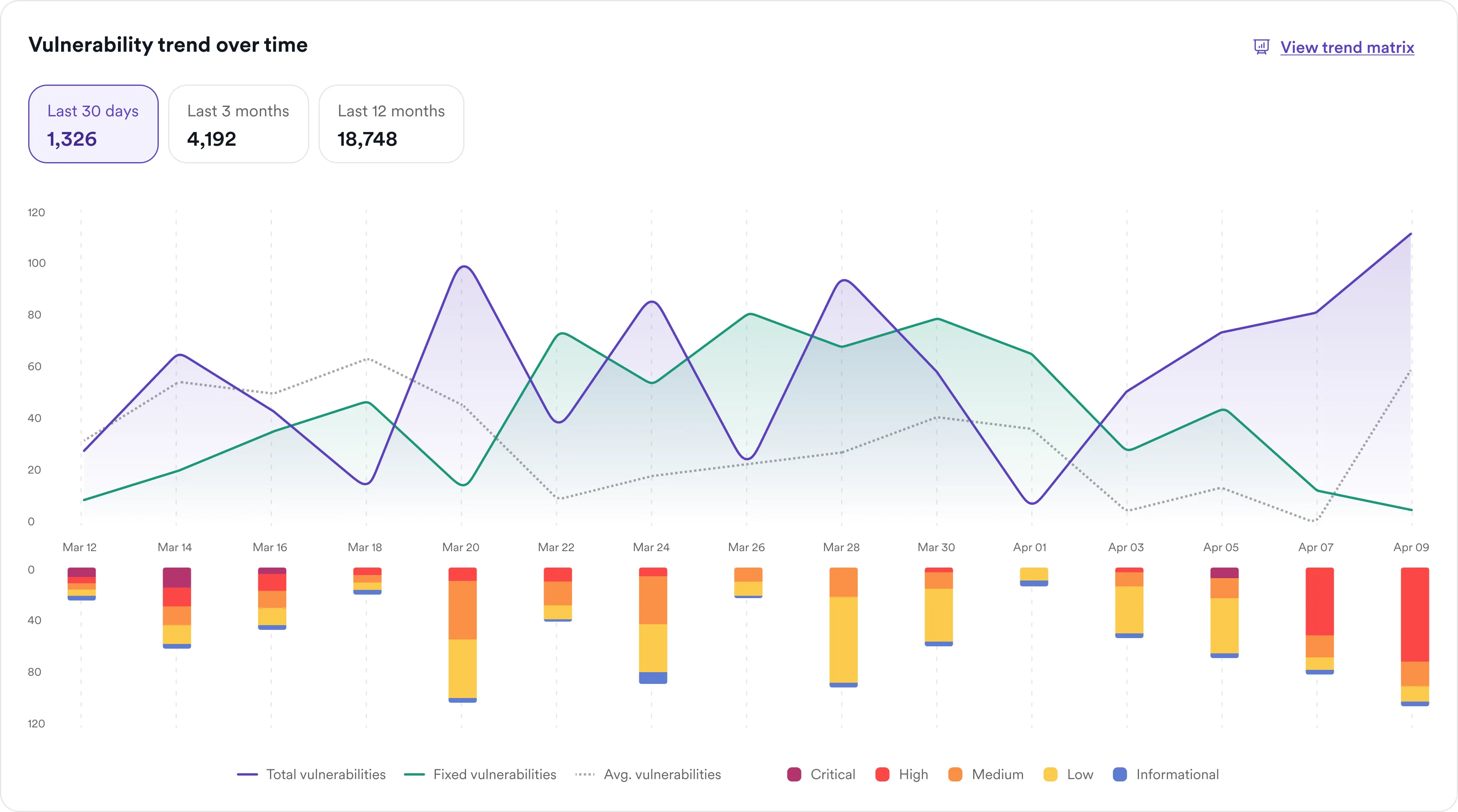
Key benefits of using Invicti for GraphQL scanning
Invicti’s crawler is designed to locate GraphQL endpoints as part of its standard scanning routine. It can identify both embedded and standalone endpoints, including those hidden behind forms or single-page applications. This automated discovery reduces manual effort and ensures full API coverage.
Invicti uses GraphQL introspection (when enabled) and schema definitions to map out the structure of your API. This enables the scanner to build precise attack surfaces, testing each query and mutation individually. As a result, Invicti can simulate attacker behavior more accurately and catch vulnerabilities that static tools may miss.
Using its DAST engine, Invicti can detect a wide range of security flaws exploitable via GraphQL APIs, including:
- SQL injection
- Command injection
- Remote code execution
- Server-side request forgery (SSRF)
- Remote code execution (RCE)
These are critical application vulnerabilities that, if left unchecked, could allow attackers to exfiltrate data,
gain unauthorized access, or take control of application servers.
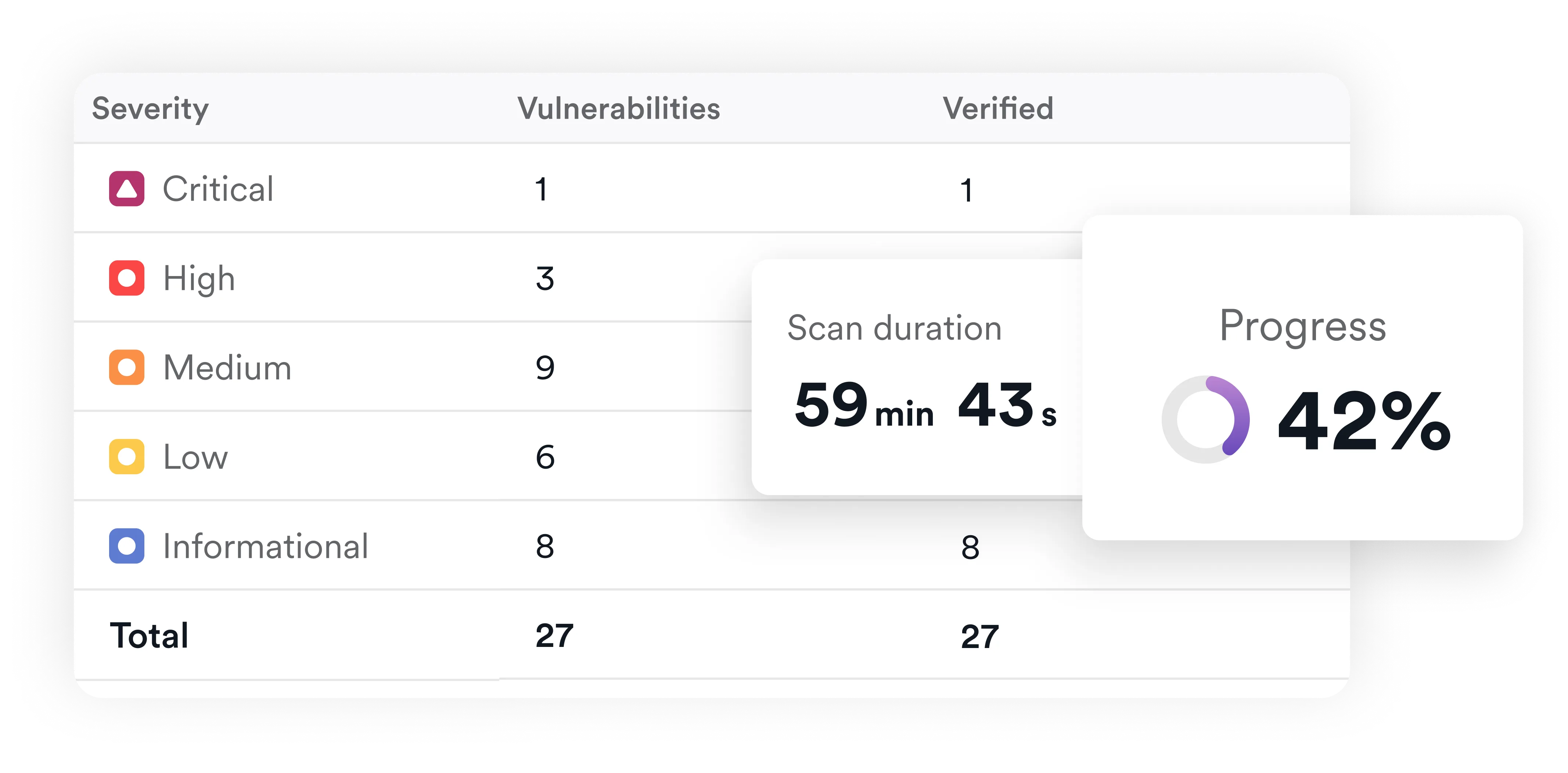
One of Invicti’s most powerful features is proof-based scanning, where exploitable vulnerabilities are automatically verified by the scanner and a proof of exploit is extracted when technically feasible. This validation eliminates the vast majority of false positives, so your security and development teams can focus on reducing actual risk without wasting time on theoretical issues.
Security testing is only effective when it fits into your development process. Invicti’s GraphQL scanning integrates with your CI/CD pipeline to provide continuous security coverage. You can trigger scans automatically, get actionable results fast, and keep pushing code without bottlenecks.
How Invicti scans GraphQL APIs
Invicti supports GraphQL scanning as a core part of its dynamic application security testing (DAST) capabilities. Typically, you import your schema into Invicti from a file or URL and the scanner will can automatically scan your GraphQL API for vulnerabilities. If introspection is enabled for testing, you don’t even need to import the schema manually – Invicti will detect GraphQL endpoints, map them out using introspection, and run the scan.
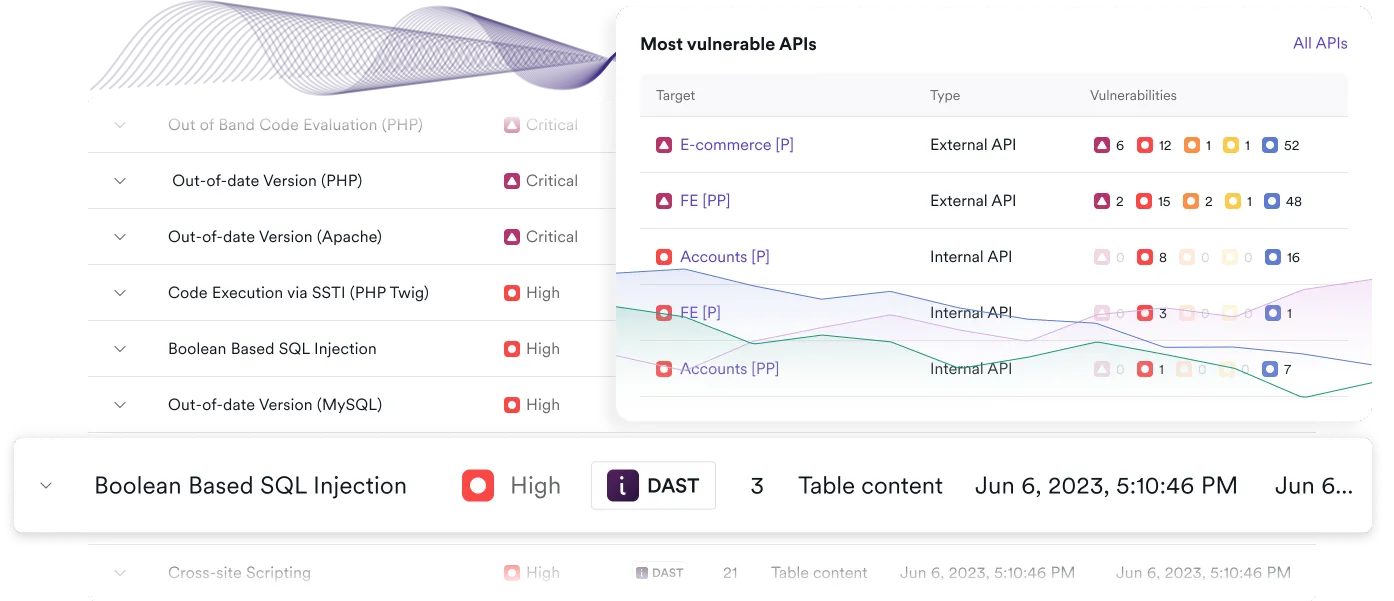
Why choose Invicti as your GraphQL vulnerability scanner
Invicti is not just another vulnerability scanner – it’s a DAST-first platform built for modern application security. Its support for GraphQL API testing is an integral part of securing your entire application by combining deep technical understanding with automation, scalability, and integration.
By focusing on exploitable risks and removing the noise, Invicti helps you secure your most critical APIs with minimal overhead. Whether your GraphQL endpoints are public-facing or internal, standalone or embedded, Invicti provides the visibility and control you need to secure them with confidence.
Secure your GraphQL APIs with confidence
GraphQL may make data access more efficient, but it also introduces a unique and growing attack surface. As attackers continue to probe APIs for weaknesses, securing them is no longer optional.
With Invicti, you can automatically discover, scan, and validate vulnerabilities in your GraphQL APIs as part of your broader application security program. Start finding and fixing real risks – before attackers do.
Ready to test your GraphQL APIs with Invicti? Learn more about GraphQL scanning or request a demo today.

3600+ Top Organizations Trust Invicti

















Save your security team hundreds of hours with Invicti’s web security scanner.






