Netsparker’s 2019: The Year in Review
2019 has been a very special year for Netsparker, as we celebrated our 10th anniversary. For the past 10 years, our revolutionary web vulnerability scanner has been helping organizations of all sizes worldwide to eliminate vulnerabilities, reduce costs, and embrace automation. We’ve also been busy with industry events, security research, whitepapers, and blog articles – so please join us for a look back at this year’s highlights and most popular content.
Your Information will be kept private.
Begin your DAST-first AppSec journey today.
Request a demo
2019 has been a very special year for Netsparker, as we celebrated our 10th anniversary. Since 2009, our revolutionary web vulnerability scanner has been going from strength to strength, helping organizations of all sizes worldwide to eliminate vulnerabilities, reduce costs, and embrace automation. During the past decade, Netsparker has gone from startup to market leader, and we are still accelerating growth to build on this success in the coming years. We want to thank all our customers and partners for being with us on this very special journey.

Industry events
Our exhibition team has been busy this year – from OWASP AppSec California 2019 to the NOPcon hacker conference 2019 in Ankara, we’ve been exhibiting the Netsparker Web Application Security Scanner at events worldwide. For most of these, Netsparker was also proud to be among the sponsors. A big thank you to everyone who came to visit our stands, and we look forward to seeing you next year!
Whitepapers
How to Secure Thousands of Websites with a Small Security Team
Large companies can now have hundreds or thousands of websites and web applications, and without the right tools and processes, security teams can find themselves overwhelmed and understaffed. This whitepaper examines how integration and automation of enterprise web security can help to combat the growing cybersecurity talent shortage.
Enterprise Web Security Best Practices: How To Build a Successful Security Process
Ensuring web application security in a large organization is a complex task that requires far more than a simple vulnerability scanner. In this whitepaper, you will learn how to choose the right tools and build a comprehensive and scalable enterprise web security process.
Deobfuscating JavaScript Code: A Steam Phishing Website
News of a highly sophisticated phishing website imitating one of Steam’s sites inspired one of our Security Researchers to do an in-depth analysis. In this technical whitepaper, Sven Morgenroth takes apart the attack code, discovers its inner workings, and shows why the scam was possible.
Cookies are a vital part of securing user interactions with modern websites – so they, too, must be protected. This technical paper looks at cookie security and shows various security measures that can protect the content of sensitive cookies, and therefore also protect users from a variety of attacks.
Top 10 posts on the Netsparker blog in 2019
In the News
Clickjacking Attack on Facebook: How a Tiny Attribute Can Save the Corporation – Ziyahan Albeniz examines a clickjacking vulnerability discovered in 2018 in Facebook’s content sharing feature and shows what you can do to prevent clickjacking.
From the Lab
Transforming Self-XSS Into Exploitable XSS – A detailed look at an advanced cross-site scripting vector.
Using Session Puzzling to Bypass Two-Factor Authentication – Ziyahan Albeniz, our Security Researcher, explains vulnerabilities in session variable handling that can allow attackers to bypass two-factor authentication.
What Impact Does the Autocomplete Feature Have on Web Security? – An analysis of variations in autocomplete behavior in different browsers, with recommendations for secure and predictable use of autocomplete functionality.
Vulnerabilities and Security Best Practices
Man-in-the-Middle Attacks and How To Avoid Them – An in-depth guide to man-in-the-middle attacks, including security tips for website administrators and end-users.
Protecting Your Website Using an Anti-CSRF Token – This blog post outlines the dangers of Cross-Site Request Forgery and shows how to use server-side tokens to prevent attacks.
What Is Session Hijacking: Your Quick Guide to Session Hijacking Attacks – An overview of web application session hijacking vectors, complete with best-practice recommendations for reducing the risk of attacks.
Frame Injection Attacks – Ziyahan Albeniz, our Security Researcher, explains frame injection attacks, analyzes a specific injection scenario, and shows how to mitigate this class of vulnerabilities.
How Buffer Overflow Attacks Work – A detailed look at buffer overflow vulnerabilities, including examples for several programming languages and tips on writing secure code.
What Is Privilege Escalation and Why Is It Important? – An overview of the causes and consequences of privilege escalation vulnerabilities, with recommendations for protecting systems and applications.
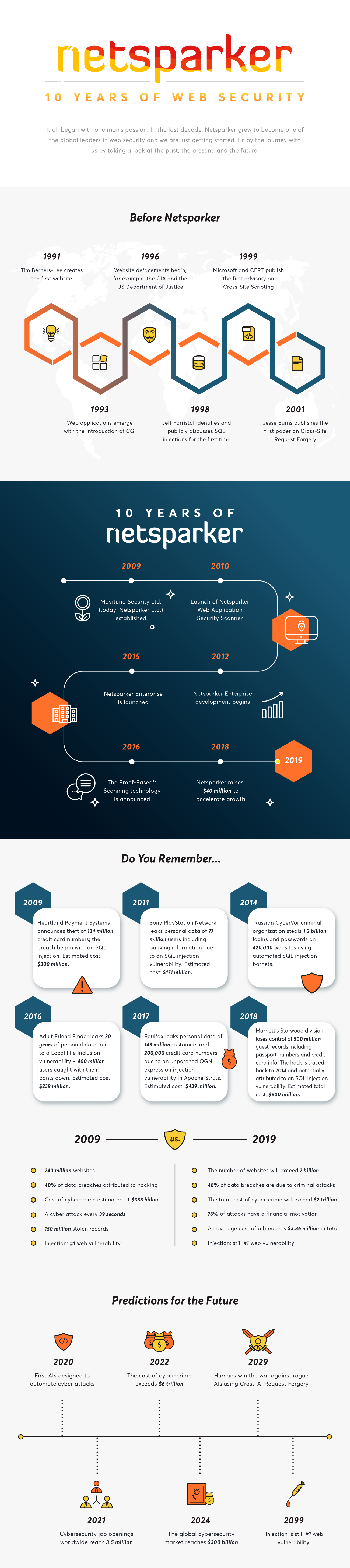
The Past, Present, and Future of Web Security
And finally, let us take you on a graphic journey through the history of web security – from the inception of the World Wide Web through the development of Netsparker to our predictions for the distant (and not-so-distant) future.