Adding flexibility to teamwork
Web application development is all about teamwork, as is the process of finding and remediating application vulnerabilities. With its
wide array of integrations, Invicti can feed accurate scan results into your organization’s existing issue trackers, CI/CD tools, and collaboration platforms. It also integrates with single sign-on (SSO) providers and
privileged access management (PAM) solutions to help with user management. Now, we have also completely redesigned the way Invicti works with teams and permissions.
A few years ago, it was common to have only the security team using the
vulnerability scanner. Today, with the move to shift security left and build
DevSecOps workflows, everyone in the development pipeline needs to be involved in ensuring security. Recognizing this, we have rebuilt the roles and permissions system from the ground up to provide granularity and role-based flexibility that matches the needs of modern teams.
Out with the old, in with the new
Previously in Invicti Enterprise, you could only have one team, and members’ access to the product was managed using a handful of built-in roles with predefined permissions. There was no way to edit or create roles and permissions. Each role assigned to a member also applied across all of that member’s website groups, limiting the management options available to administrators.
 The old way: managing member permissions directly
The old way: managing member permissions directly
All this has changed with the new scheme based around teams and roles. You can now create any number of
teams and
roles to match your internal organization and workflows. The new capabilities provide maximum flexibility for access management:
- You can group members in any way you want and assign roles built from granular permissions.
- Members of a team inherit its permissions, in addition to any direct permissions assigned per member.
- Each member can belong to multiple teams.
- You can create custom roles from over 80 detailed permissions and assign them to members and teams.
- You can edit and delete roles and teams at any time.
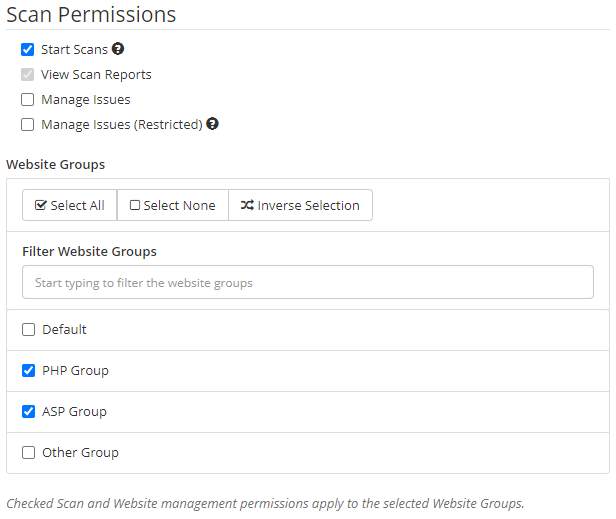
 The new way: managing permissions by assigning roles
The new way: managing permissions by assigning roles
To ensure backward compatibility, all existing Invicti roles have been transferred into the new version as built-in roles.
More effective management and improved coordination
While web application security teams are usually small, in large organizations they can be responsible for
securing hundreds of websites and coordinating the remediation efforts of multiple developer teams. Effective management in the face of ever-increasing workloads requires good coordination and orchestration. With the new features in Invicti Enterprise, you can create as many teams and roles as you need, so each team knows its exact scope of responsibilities and can perform better.
For example, you can define a dedicated team responsible for running and scheduling vulnerability scans and a separate team tasked with fixing vulnerabilities. When defining team or member roles, you can select any combination of over 80 permissions for maximum flexibility. You can also edit teams and roles at any time in response to new projects, policies, and business priorities. The new scheme ensures full transparency, so you always know exactly which teams and members have which permissions.
Making security everyone’s business
In modern agile web development, security is no longer handled only by the security team. After all, a large organization might have hundreds of developers but only a handful of security professionals, so shifting security left towards development is a practical necessity. With
Proof-Based Scanning and a wide array of integrations, Invicti can deliver actionable vulnerability reports directly to developers, making them an integral part of the extended security team.
The new teams and permissions system in Invicti Enterprise makes it easy to involve a variety of stakeholders in the vulnerability management process. You can set up custom teams and granular roles that precisely match the responsibilities and permissions you need. For example, you can define separate roles for security engineers, scan administrators, developers, team managers, and executives to enable self-service reporting and progress monitoring.
Seamless provisioning and handovers
User provisioning and management are a vital part of running a dynamic organization where development teams can grow and shift on a monthly basis, depending on the workload and business priorities. Invicti Enterprise now makes it easy to define and manage teams and team permissions so a new employee can automatically get the right permissions without manual intervention by an administrator. Because a new member now inherits team permissions, simply adding the member already assigns the right starting roles. You can then add any individual permissions as necessary.
With the new set of granular permissions, members can clearly see exactly what tasks they are allowed to perform. It is also much easier to follow the principle of minimum necessary privileges for improved security, so even if a member’s credentials are compromised, the operations available to any malicious users will be strictly limited by that member’s roles and permissions. For example, if a member is only authorized to launch and schedule scans, compromising their account will not give attackers any additional information about your applications or security status.
Invicti Enterprise has also added support for the
System for Cross-domain Identity Management (SCIM) 2.0 standard, enabling you to automate user identity lifecycle management. Any changes to user role or responsibilities made via your identity providers, such as
Azure AD or
Okta, can now be directly reflected in your Invicti Enterprise teams. Combined with the other benefits of the new teams and permissions system, this allows you to manage your web application security workflows in a more collaborative, orchestrated, and effective manner.

 The old way: managing member permissions directly
The old way: managing member permissions directly The new way: managing permissions by assigning roles
The new way: managing permissions by assigning roles




